SentinelOne experts have discovered a previously unknown Metador hack group that attacks telecommunications companies, Internet providers and universities in many countries of the Middle East and Africa.
Researchers report that the group’s main goal appears to be long-term espionage. Metador uses two malware for Windows that experts describe as “extremely sophisticated,” but signs of a Linux malware have also been found.Let me remind you that we also wrote that Cyber-Espionage Group Worok Attacks Asian Governments and Companies.
Metador’s presence was first discovered on the network of an unnamed telecommunications company in the Middle East, which had previously been hacked by about ten other hack groups from China and Iran, including Moshen Dragon and MuddyWater.
Although the details of Metador’s penetration into the victim’s network remain unknown, two malicious frameworks have been found that target Windows. They are called metaMain and Mafalda and are specifically designed to work in memory and evade detection.
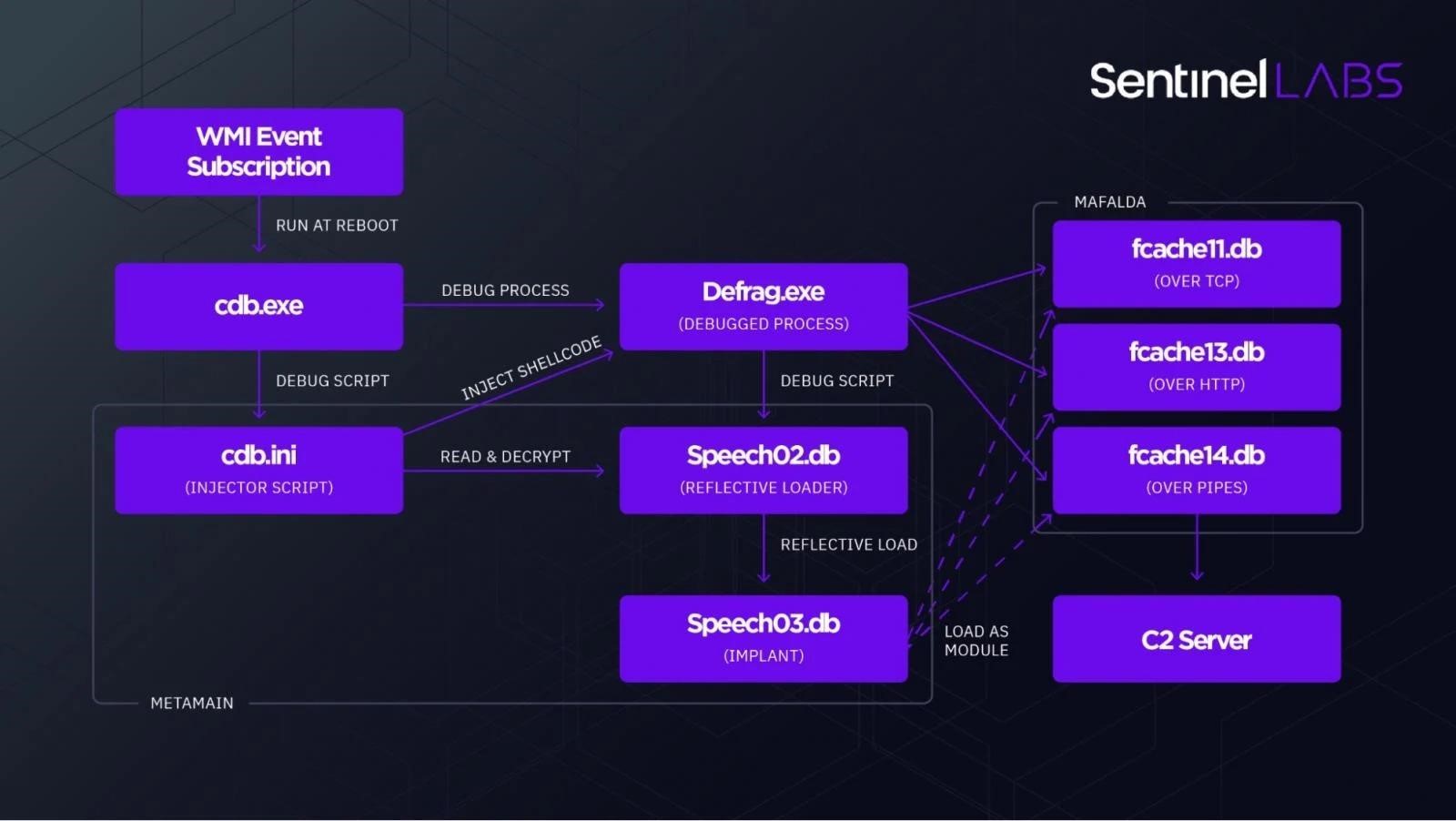
The researchers say that metaMain is multifunctional and allows attackers to retain access to the victim’s system, intercept keystrokes, take screenshots, upload and download arbitrary files, and execute arbitrary shellcode. It also acts as a conduit for the deployment of Mafalda, a more flexible and versatile malware that supports 67 commands. Its multi-level obfuscation significantly hampered in-depth analysis.
Experts believe that Mafalda is more actively supported by developers, since in the period from April to December 2021 alone, the malware received the support of 13 new commands, having learned to steal credentials, conduct network reconnaissance and manipulate the file system. Judging by the comment in the code, Mafalda is being developed by people specially hired for this, that is, there is a clear separation between developers and malware operators.
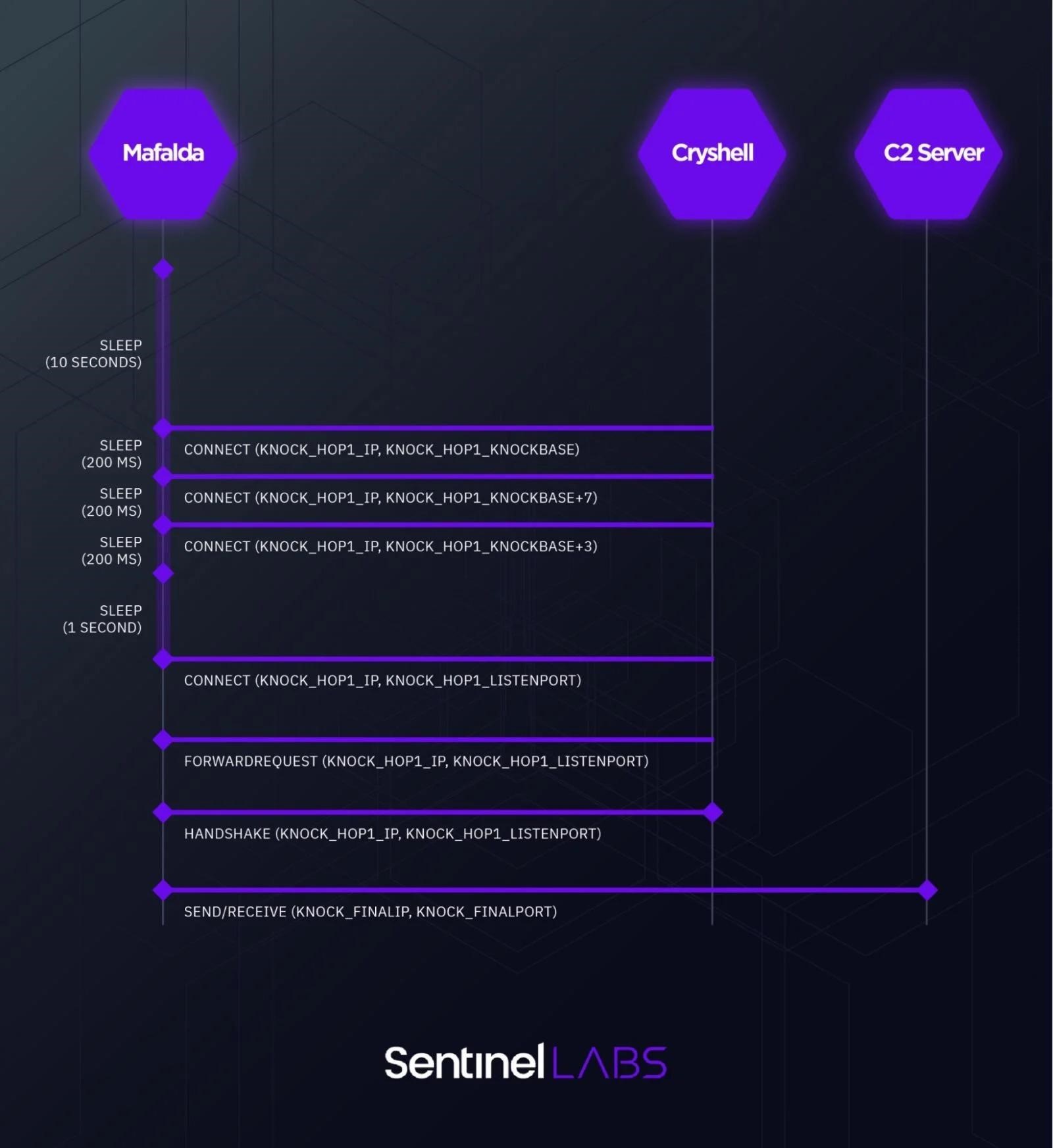
Also, analysts found signs of a special malware Cryshell, which is used for actions on the internal network and an unnamed Linux tool that steals credentials from workstations and sends them to Mafalda.