More and more evidence proves that GandCrab team has regrouped into a more advanced ransomware program.
It’s known as REvil, Sodin and Sodinokibi.
“We are getting a well-deserved retirement. We are a living proof that you can do evil and get off scot-free”, — the GandCrab administrator(s) wrote in their farewell message on May 31.
However, now it seems that the GandCrab team has already begun preparations for the rebranding.
At the end of April, researchers from Cisco Talos discovered a ransomware strain called Sodinokibi, which was used to deploy GandCrab. It encrypts files on infected systems until the victim pays the required amount. A month later, GandCrab suddenly announced its closure.
There is an interesting coincidence in the behavior of “ransomwre” associated with … Syria.
The ban on malware distribution in the CIS countries has long been the main requirement of cybercriminal affiliate programs.
Kaspersky Lab discovered that Sodinokobi/REvil also includes another nation in its list of countries that affiliates should avoid infecting: Syria.
Interestingly, the latest versions of GandCrab made the same unusual step. After criminals learned that a person from Syria complained on Twitter that due to GandCrab lost access to photos of their dead children – they released a key that allowed to unblock all infected computers in Syria.
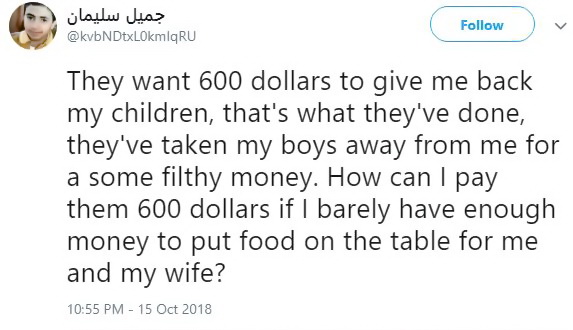
In October 2018, a Syrian man tweeted that he had lost access to all pictures of his deceased children after his computer got infected with GandCrab
A week after that, the No More Ransom project released the free GandCrab decryption tool developed by the Romanian police in collaboration with law enforcement agencies in several countries and the security firm Bitdefender. Decryption keys for Syrian victims allowed calculating the entropy used by the random number generator for the ransomware’s master key.
According to a recent report by the Dutch security company Tesorion, there is also a similarity between the ways that GandCrab and REvil generate URLs that are used as part of the infection process.
Tesorion reports that there are some striking similarities in how this specific part of the code works, e.g., in the somewhat far-fetched way that the random length of the filename is repeatedly recalculated.
“My guess is the GandCrab team has not retired, and has simply regrouped and re-branded due to the significant amount of attention from security researchers and law enforcement investigators. It seems highly unlikely that such a successful group of cybercriminals would just walk away from such an insanely profitable enterprise”, — concludes well-known author of materials and notes on Internet security Brian Krebs.

