36″Mado” Virus
Mado is a STOP/DJVU family of ransomware-type infections1. This ransomware encrypts your private files (video, photos, documents). The infected files can be tracked by specific “.mado” extension. So, you can’t open them at all.
In this article I will try to help you remove Mado virus without any payment. As a bonus I will assist you in decoding your encrypted files.
What is “Mado”?
Mado can be correctly identify as a ransomware infection.
Ransomware is a kind of virus that crypted your documents and then forces you to pay for them. DJVU (aka STOP) ransomware family was first revealed and analyzed by virus analyst Michael Gillespie2.Mado is similar to other ransomware like: Jope,Opqz, Npsk, Remk. It crypted all popular file types. Hence, users can’t open files. Mado adds its particular “.mado” extension into all files after encryption. For instance, the file “video.avi”, will be amended into “video.avi.mado”. As soon as the encryption is accomplished, Mado drops a special text file “_readme.txt” and adds it into all folders that contain the modified files.
Here is a short info for the Mado :
| Ransomware family3 | DJVU/STOP4 ransomware |
| Extension | .mado |
| Ransomware note | _readme.txt |
| Ransom | From $490 to $980 (in Bitcoins) |
| Contact | [email protected], [email protected] |
| Detection | BScope.TrojanSpy.Zbot, Trojan-Dropper.Win32.Dropback.ln, Trojan:Win32/Glupteba.RDL!MTB |
| Symptoms | Your files (photos, videos, documents) have a .mado extension and you can’t open it |
| Fix Tool | See If Your System Has Been Affected by .mado file virus |
This text asking payment is for restore files via decryption key:
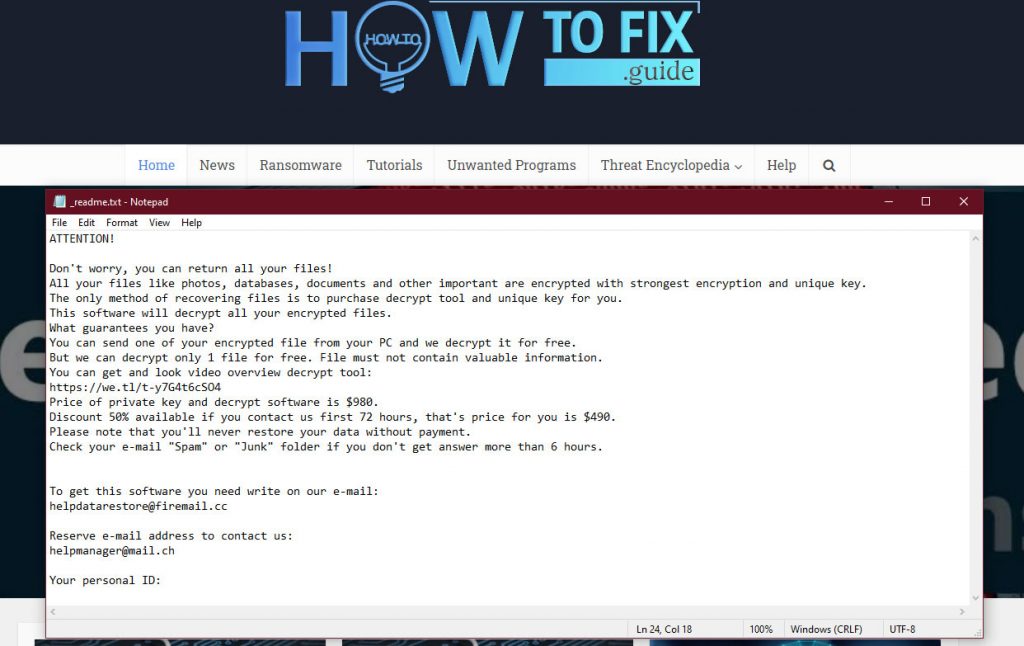
The scary alert demanding from users to pay the ransom to decrypt the encoded data contains these frustrating warnings: _readme_txt
The cryptography algorithm used by Mado is AES-256. So, if your files got encrypted with a specific decryption key, which is totally unique and there are no other copies. The sad reality is that it is impossible to recover the information without the unique key available.
In case if Mado worked in online mode, it is impossible for you to gain access to the AES-256 key. It is stored on a remote server owned by the criminals who promote the Mado ransomware.
There are also some reports that saying about Mado ransomware add it’s readme.txt file in autoload registry bush, so every time user logging in his system, he will get annoying reminder. This causes are not widespread, but, as we can see, Mado has a lot of subversions that have a lot of distinction in it’s performance.
But adding his entities to Run key is not the only Mado ransomware action with registry. The common practice is that it adds it’s .exe file in the RunOnce key. So, every time user starts Windows – ransomware will start, too, so you can’t stop ransomware with simple system restart. But, it could be prevented with system launch in special mode – safe mode or mode with command line support.
In spite of registry, Mado ransomware can also change hosts file to disable Windows updates. Thus, Windows can’t perform “self-cleaning”, changing all it’s internal settings, registry keys and directories on the C:/ to default. So, if you used to have Windows updates regulary, and notice that your PC haven’t got them for a long time – it can be a sign of slow Mado ransomware activity on your PC.
One of the most knavish trick of Mado ransomware is hosts file editing. It can add all popular sites of anti-malware softare, forums, where ransomwares are disscussed, to hosts file. So, you wouldn’t able to open this pages. It’s quite easy to fix, but not being in panic and having the only wish to get your files back.
Jope ransomware distributors understand, that a huge part of their victims can be get cured using advices given on such sites. So, they are usually blocking all sites you can see below:
This list is updating.
For receiving decryption key the payment should be $980. To obtain the payment details the victims are encouraged by the message to contact the frauds by email ([email protected]).
N.B. Some users, generally from Western Europe, reporting about modified readme.txt files, that contains much bigger sum asked for decryption key. In majority of cases it vary from 1300$ up to 1500$ for key, but their pricing in 72 hrs term is unchanged – 490$. It looks like crooks forcing their victims to pay now, or pay much more.
UPD 17.04.2020. One more group of Mado ransomware victims reported that their readme.txt contained another information about the sum they need to pay. Ransomware distributors are asking them to send 0.3 BTC (about 2100$) to decrypt their files. They have even changed a sum for 72-hrs payment. Now, that is 0.1 BTC. It can also be an instrument to force users to pay faster. Bitcoin price is unstable, so scared victims will probably hurry up to pay less.
Do not pay for Mado!
Please, try to use the available backups, or Decryptor tool
_readme.txt file also indicates that the computer owners must get in touch with the Mado representatives during 72 hours starting from the moment of files where encrypted. On the condition of getting in touch within 72 hours, users will be granted a 50% rebate, thus the ransom amount will be minimized down to $490). However, stay away from paying the ransom!
I definitely recommend that you do not contact these crooks and do not pay. The one of the most real working solution to recover the lost data – just using the available backups, or use Decrypter tool.
There are quite clear reasons not to contach ransomware distributors. You likely wouldn’t get any decryption key while talking to them. But fraudsters will get a profit from you even without your participation. Even if they lost trying to force you to pay them, they will then sold your e-mail to another knaves, who will spam your e-mail.
Fraudsters may try to show you, that they are honest and will decrypt your files after payment. We have a lot of comments of victims who contacted fraudsters and got 1-2 files decrypted. Croocks are calling it “decryption test”, hoping that you will pay them a full price, seeing that thet are not lying. But everyone need to understand that to entrust fraudsters is like to let them to fool you again
The peculiarity of all such viruses apply a similar set of actions for generating the unique decryption key to recover the ciphered data.
The mechanism of Mado ransomware supposes that it’s .exe file contains offline keys, that can help user to decrypt his files. However, this ransomware final action is self-destruction. So, if you want your files to be decrypted faster, and you want to help antimalware developers – start full scan as soon as you detected a ransomware activity on your PC. It will help developers to add their offline keys database, and improve Decryptor tool functionality.
Some users we contacted with said that their “edition” of Mado ransomware had an offline key, that was been hidden inside of one of the readme.txt files, that was been generated by ransomware. So, if you have installed some dubious software long ago, and guess that ransomware could be asleep for a long time – check your luck, maybe you will be able to decrypt your files without any payments.
You can find a link to decryption manual inside of readme.txt file. Fraudsters are offering to download their decryptor, which demands any type (online or offline) of decryption key. But there is no guarantee that they wouldn’t inject any malware with this “decryptor”. So, if you are really lucky and removed Mado ransomware with it’s own offline key and decryptor, that is offered by ransomware distributors – check your PC with an anti-malware program.
There is an interesting information about Mado ransomware encryption mechanics. The STOP ransomware family (Mado ransomware belongs to this family) only encrypts the first 150 kilobytes of files. Since MP3 or MP4 files are rather large, some media players ( Winamp, for example ) may be able to play the files, but the first 3-5 seconds (the encrypted portion) will be missing. That could be a solution if you need to listen to the someone’s voice recording or watch a video but got attacked by Mado ransomware.
Another way you can get to know if you have an offline key is checking the PersonalID.txt file. You can find it in SystemID folder, which is located on C:/ disk. If any of present entries ends with “t1” – you can recover your data using the decryptor we are offering to use below.
That’s also quite dangerous to use and share the decryptor that is offered by ransomware distributors. No one can be sure if this software contains another malware. It could be with adware or browser hijacker inside, may also contain trojans or backdoors, or even be clear. But I think that such risk is not nesessary, especially if you PC is already encrypted.
Thus, unless the ransomware is still under the stage of development or possesses some hard-to-track flaws, manually recovering the ciphered data is a thing you can’t really perform. The only solution to prevent the loss of your valuable data is to regularly make backups of your crucial files.
Note that even if you do maintain such backups regularly, they ought to be put into a specific location without loitering, not being connected to your main workstation.
For instance, the backup may be kept on the USB flash drive or some alternative external hard drive storage. Optionally, you may refer to the help of online (cloud) information storage.
Another problem can be ransomware injection in your backups. It can contaminate backups that are already done as well as new backups you are making already with ransomware onboard. So, you can get a malicious joke – yes, you are making a backup, but using it as a system restore base have literally no effect.
Even more – Mado ransomware can delete the darkness duplicate files from your PC in order to disable Windows Recovery. So, if you use proprietary Windows backup methods and mechanisms – be ready your backup to be blocked by sly ransomware.
The feature of all ransomware, including Mado ransomware, is that their performance is not instantaneous. No one can surely say how long encryption takes, and do this term specified in the command that launches ransomware. All these timings are specified by ransomware. But one is clear – you can notice encrypted files with .mado extension even before readme.txt file appearing.
Also, Mado ransomware performance cannot be surely defined with timeframes of some sort. After formal starting of encryption process, it can randomly encrypt your videos or music, or can choose the files you are opening and files, that are in the same folder with first file. Anyway, the way it will perform the encrypring process is defined only by ransomware distributors.
Another noteworthy issue is Mado ransomware influence on weak systems performance. After the encryption process started, old and weak systems with low RAM capacity could suffer of a lagspikes, slow application opening and general system inhibition.
N.B. Majority of ransomware have troubles with large files encrypting, like films, videos or archives. And Mado ransomware is not an exclusion. When some troubles occure till the big file encryption, it can just add .mado extension, then switch to another file. So, you can try to delete .mado extension and run the file as usual. But that’s not a panacea – there is still a chance that this big file will be encrypted.
UPD. 15.04.2020. We got a significant number of reports about odd behaviour of some versions of Mado ransomware. This modifications have other encryption performance and one interesting feature. It starts encryption with choosing randomly a file that would be encrypted first, then ransomware encrypts all files from the same folder with first one. The mentioned interesting feature is that this versions of Mado ransomware cannod encrypt files that are on another disk.
We compared a lot of users’ reports about different ransomware and draw a conclusion that this “random” disk encryption is a common feature of all STOP/Djvu ransomware family, to which belongs Mado ransomware. But, nonetheless, there are a lot of causes when Mado ransomware, like all other ransomware of his family, encrypted both disks.
Needless to mention, when you maintain your backup data on your common device, it may be similarly ciphered as well as other data.
For this reason, locating the backup on your main PC is surely not a good idea.
How I was infected?
Mado has a various methods to built into your system. But it doesn’t really matter what concrete method had place in your case.
Crackithub[.]com, kmspico10[.]com, crackhomes[.]com, piratepc[.]net — sites that distribute DJVU Ransomware. Any app downloaded from there sites can be infected by this ransomware.
Examples of such sites:
xxxxs://crackithub[.]com/adobe-acrobat-pro/ xxxxs://crackithub[.]com/easyworship-7-crack/ xxxxs://kmspico10[.]com/ xxxxs://kmspico10[.]com/office-2019-activator-kmspico/ xxxxs://piratepc[.]net/category/activators/ xxxxs://piratepc[.]net/startisback-full-cracked/
Mado attack following a successful phishing attempt.
- hidden installation along with other apps, especially the utilities that work as freeware or shareware;
- dubious link in spam emails leading to the Mado installer
- online free hosting resources;
- using illegal peer-to-peer (P2P) resources for downloading pirated software.
There were cases when the Mado virus was disguised as some legitimate tool, for example, in the messages demanding to initiate some unwanted software or browser updates. This is typically the way how some online frauds aim to force you into installing the Mado ransomware manually, by actually making you directly participate in this process.
Surely, the bogus update alert will not indicate that you are going to actually inject the Mado ransomware. This installation will be concealed under some alert mentioning that allegedly you should update Adobe Flash Player or some other dubious program whatsoever.
Of course, the cracked apps represent the damage too. Using P2P is both illegal and may result in the injection of serious malware, including the Mado ransomware.
To sum up, what can you do to avoid the injection of the Mado ransomware into your device? Even though there is no 100% guarantee to prevent your PC from getting damaged, there are certain tips I want to give you to prevent the Mado penetration. You must be cautious while installing free software today.
Make sure you always read what the installers offer in addition to the main free program. Stay away from opening dubious email attachments. Do not open files from the unknown addressees. Of course, your current security program must be always updated.
The malware does not speak openly about itself. It will not be mentioned in the list of your available programs. However, it will be masked under some malicious process running regularly in the background, starting from the moment when you launch your computer.
It’s important to understand that Mado ransomware creators and distributors never spreads their malware to victims directly. The usuall distribution model is freeware-as-a-carrier. Croocks contact with freeware software distributors, which are oftenly add some kind of PUP-browsers, antiviruses or so to their product, and offering them to add their Mado ransomware file to installation file of the freeware program; of course, fraudsters are offering quite big payment for this action. So, you can install a freware programm, that can have literally no signs of the ransomware inside, and even disable installation of all PUPs, that are usually included in “Standart” installation programme. But anyway, you will get a ransomware.
A lot of users from Central Europe reporting that Mado ransomware distributors started an e-mail spamming process. The majority of messages were sent from dead e-mails to Gmail, Tuta.io, Yahoo and Yandex e-mail hostings users. In these messages, users are invited to test a new add-on for Google Chrome and Mozilla, that allows checking coronavirus disease statistics in your region and worldwide. If you install this add-on, the countdown of your PC encryption will be started.
Another popular way of Mado ransomware distribution is torrent-trackers. The most often appearance of Mado was been spotted on 1337x tracker, one of the most popular torrent-trackers in Europe. Usually, users noticed ransomware activity after films, games and music downloading. All of them had common peers of the seedings, but there are no common features of this peers, so currently we cant find out, who’s standing behind this attack.
UPD. 09.04.2020. We got a lot of compliances from The Pirate Bay users, one of the biggest and most popular torrent trackers, about ransomware wave. A lot of new seedings of, generally, games and films, are contaminated with different ransomware. But the majority of reports was about Mado ransomware. That’s another reminder about why torrent-trackers can be very dangerous source of files.
UPD. 12.03.2020. Our team collected a lot of data about possible ransomware source. For the last 4 days, one of the most popular program type which was installed and run before Mado ransomware encryprion was keygen for Adobe products, generally Photoshop, Premiere Pro and Illustrator. Some of this keygens were really useful and generated a true key, but majority was just a billet. It seems that the main target-group for croocks was designers and photo editors.
Majority of ransomwares are distributed with another malware, e.g. adware, trojan, backdoor, or, perhaps, browser hijacker. And Mado ransomware has the same “distribution policy”. So, if you detected simple malware activity – don’t shelve a full scan of your PC with anti-malware software, because every adware or hijacker may be a sign of something much more serious.
And we have a lot of reports about AZORult trojan that is usually “follows” Mado ransomware. AZORult is a trojan-stealer, that is targeted on your personal information, like passwords or credit card data.
UPD. 10.04.2020. Another malware that is typically distributed with Mado ransomware is SAntivirus. It is a PUP, which is trying to be anti-malware program, so, showing you plenty of threats on your PC, and offering to cure them after the puchasing of full version. We was contacted by a lot of users, who previously removed SAntivirus, using our guidance, and they told that now they’ve got Mado ransomware. So, if you noticed this annoying PUP-antivirus (and it is VERY hard to not to notice him) – start the full scan as soon as possible.
A lot of ransomware injection in April, 2020 is caused by adware+ransomware joint action. After you got an adware on your PC, all usuall ads will be changed to ads with link on ransomware downloading. Such ads usually contains “update your browser now” offer, promising to give you the last version of Opera, Chrome, Mozilla or so.
One more way of Mado ransomware distribution is advetiserments on random sites, which are offering you to install free and 100% effective antivirus, and, perhaps, saying that you have dozens of threats on your computer (which they detected, of course, through TCP/IP). If you follow such link, you will get SAntivirus, a PUP-antivirus, that is at least useless and showing you a false positive threat scan results. But besides useless PUP you will also get a Mado ransomware with all usuall consequenses.
UPD. 07.04.2020. A lot of users who previously got a message on their e-mail with an add-on installation offer became a victims of another spam wave, organized by ransomware distributors. In this message you get a repayment invoice for a some puchase you have done before. This invoice is in .pdf or .docx file, and you are suggested to download it. And, of course, you won’t get anything but ransomware on your PC, trying to open this file.
UPD. 12.04.2020. Another group of users reported that they’ve got a lot of e-mails with fake PayPal invoices. Scheme is the same as in previous paragraph – the victim gets a message about some puchases need to be paid via PayPal; the invoice of this puchasement is attached to this e-mail. After the “invoice” downloading, user gets Mado ransomware that starts encryption immediately.
UPD. 14.04.2020. New e-mail spam wave started in United States. This time, the target of this spamming is DHL or FedEx customers. They’ve got a messages about unpaid invoice for delivery they ordered before. Of course, in current situation, when literally everyone uses online-shops and delivery, that is a lot of people who doesn’t remember about all their orders. Then, the typical invoice injection scheme, that was described earlier, starts.
Earlier we mentioned about possible hazard that can be caused by decryptor that is distributed by Mado ransomware distributors. That was a real reason to do this. Some users reported about a huge pack of “simple” malware that is distributed with so-called “decryptor1.exe.”. After installation of this decryptor, search engines of all user’s browsers was changed, and every twenty-thirty minutes they got a separate browser window full of advetiserments.
UPD. 19.04.2020. Another PUP-antivirus have been detected as a satellite for the Mado ransomware. Now I’m talking about Restoro – potentially unwanted program, that is very similar to SAntivirus with it’s distribution model and functionality. In a last couple of days we got significant number of complains, talking about joint Restoro adn Mado ransomware attack.
UPD 20.04.2020. New distribution wave detected on ExtraTorrent. Of course, we are talking about his clones, based on The Pirate Bay, because the original site was been shut down 3 years ago. According to the reports, a lot of fresh seedings are contaminated with different malware, including Mado ransomware.
The message by the Mado ransomware states the following frustrating information:
ATTENTION! Don't worry, you can return all your files! All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. You can get and look video overview decrypt tool: https://we.tl/t-WJa63R98Ku Price of private key and decrypt software is $980. Discount 50% available if you contact us first 72 hours, that's price for you is $490. Please note that you'll never restore your data without payment. Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours. To get this software you need write on our e-mail: [email protected] Reserve e-mail address to contact us: [email protected] Your personal ID: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
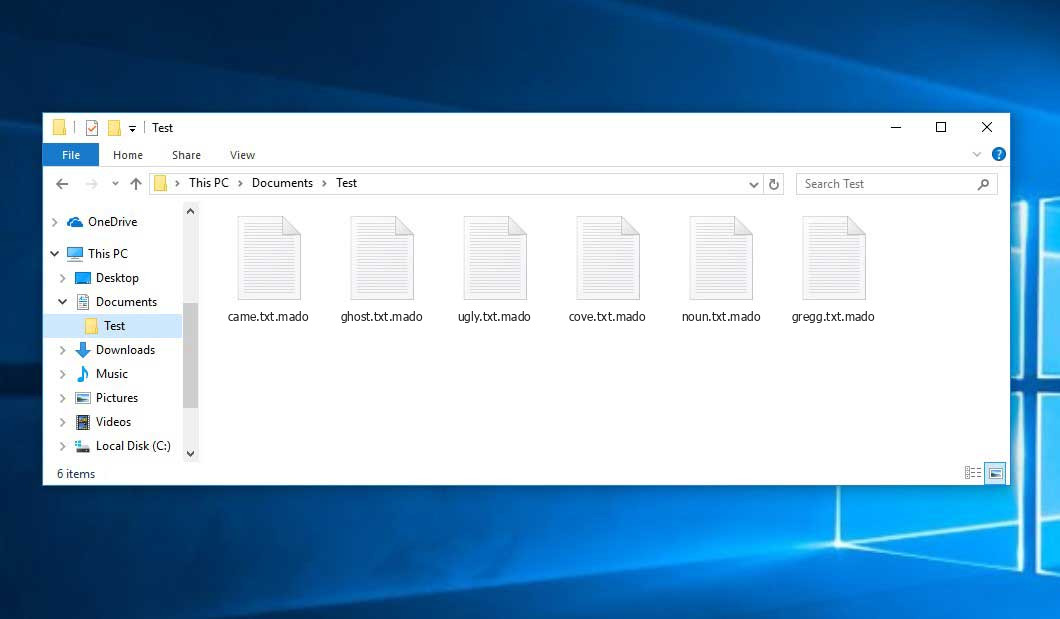
The image below gives a clear vision of how the files with “.mado” extension look like:
How to remove Mado virus?
In addition to encode a victim’s files, the Mado virus has also started to install the Azorult Spyware on PC to steal account credentials, cryptocurrency wallets, desktop files, and more.
Reasons why I would recommend GridinSoft5
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes6.
Download Removal Tool.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your PC.
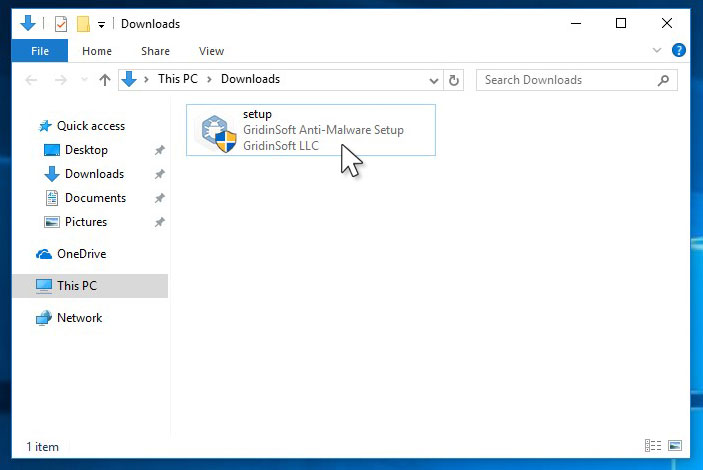
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

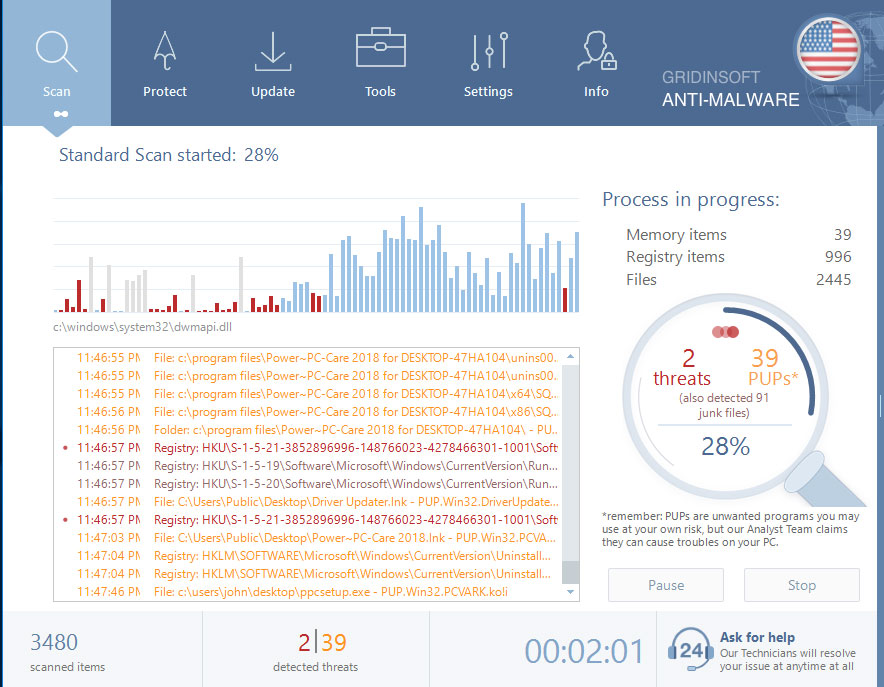
Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Mado infections and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
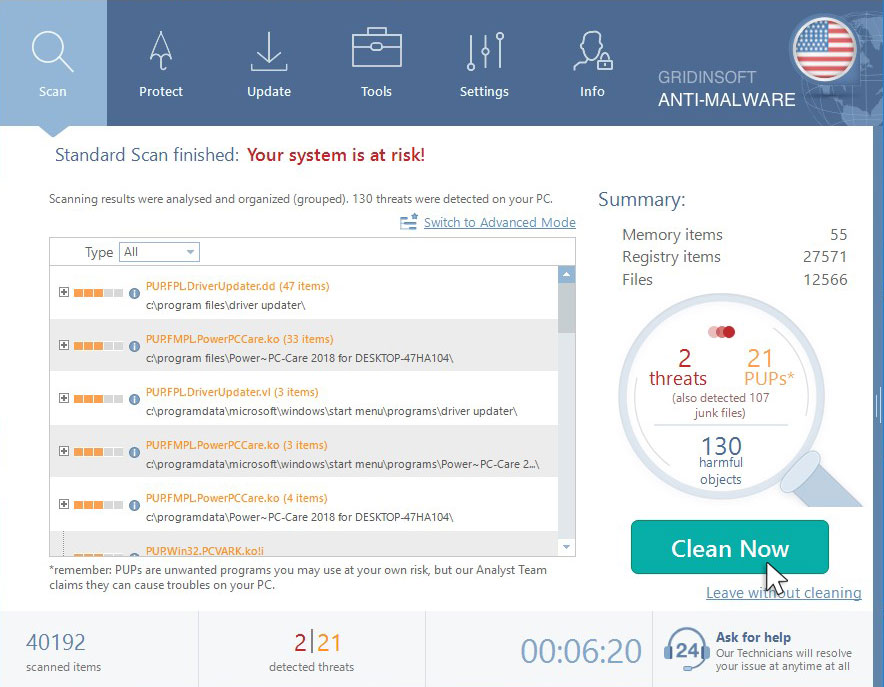
Click on “Clean Now”.
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
How to decrypt .mado files?
Restore solution for big “.mado files“
Try removing .mado extension on a few BIG files and opening them. Either the Mado virus read and did not encrypt the file, or it bugged and did not add the filemarker. If your files are very large (2GB+), the latter is most likely. Please, let me know in comments if that will work for you.
The newest extensions released around the end of August 2019 after the criminals made changes. This includes Opqz, Npsk, Remk, etc.
As a result of the changes made by the criminals, STOPDecrypter is no longer supported. Tt has been removed and replaced with the Emsisoft Decryptor for STOP Djvu Ransomware developed by Emsisoft and Michael Gillespie.
You can download free decryption tool here: Decryptor for STOP Djvu.
Download and run decryption tool.
Start downloading the decryption tool.
Make sure to launch the decryption utility as an administrator. You need to agree with the license terms that will come up. For this purpose, click on the “Yes” button:
As soon as you accept the license terms, the main decryptor user interface comes up:
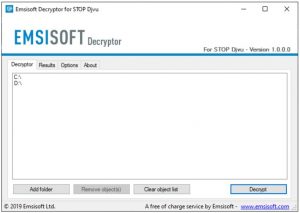
Select folders for decryption.
Based on the default settings, the decryptor will automatically populate the available locations in order to decrypt the currently available drives (the connected ones), including the network drives. Extra (optional) locations can be selected with the help of the “Add” button.
Decryptors normally suggest several options considering the specific malware family. The currently possible options are presented in the Options tab and can be activated or deactivated there. You may locate a detailed list of the currently active Options below.
Click on the “Decrypt” button.
As soon as yo add all the desired locations for decryption into the list, click on the “Decrypt” button in order to initiate the decryption procedure.
Note that the main screen may turn you to a status view, letting you know of the active process and the decryption statistics of your data:
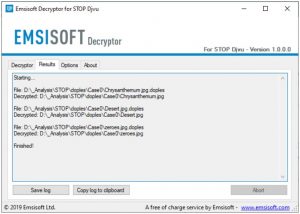
The decryptor will notify you as soon as the decryption procedure is completed. If you need the report for your personal papers, you can save it by choosing the “Save log” button. Note that it is also possible to copy it directly to your clipboard and to paste it into emails or forum messages if you need to do so.
Frequently Asked Questions
How can I open “.mado” files?
Why is the MADO decrypter stuck on “Starting”?
mado files contain important information. How can I decrypt them urgently?
If not, then you can try to restore them through the system function – Restore Point.
All other methods will require patience.
You have advised using GridinSoft Anti-Malware to remove Mado. Does this mean that the program will delete my encrypted files?
You need GridinSoft Anti-Malware to remove active system infections. The virus that encrypted your files is most likely still active and periodically,
runs a test for the ability to encrypt even more files. In addition, these viruses install keyloggers and backdoors for further malicious actions
(for example theft of passwords, credit cards) often.
Decrytor did not decrypt all my files, or not all of them were decrypted. What should I do?
We will keep you posted on when new Mado keys or new decryption programs appear.
What can I do right now?
- In the United States: On Guard Online;
- In Canada: Canadian Anti-Fraud Centre;
- In the United Kingdom: Action Fraud;
- In Australia: SCAMwatch;
- In New Zealand: Consumer Affairs Scams;
- In France: Agence nationale de la sécurité des systèmes d’information;
- In Germany: Bundesamt für Sicherheit in der Informationstechnik;
- In Ireland: An Garda Síochána;
Video Guide
It’s my favorite video tutorial: How to use GridinSoft Anti-Malware and Emsisoft Decryptor for fix ransomware infections.
If the guide doesn’t help you to remove Mado infection, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments for getting help.
User Review
( votes)References
- Ransomware-type infection: https://en.wikipedia.org/wiki/Ransomware
- Twitter: https://twitter.com/demonslay335
- My files are encrypted by ransomware, what should I do now?
- About DJVU (STOP) Ransomware.
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison


Hello
I cannot access my laptop with mado extension virus input files. Can you help me with this? Do I have a chance to recover my files?
No key for New Variant offline ID: 8TaHEsq5r7cNJKbYdWseLEB2pW1FuZKoKjKg5tt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
The MADO offline key was uploaded to the server. Try to decrypt.
I am from China, and I am infected with mado virus today, I hope to get help
Your personal ID:
0217OIWojlj48ce361sNqvFnwlFIG6pXkP1a1Y4dXs6fmxbAfWZWF
No key for New Variant online ID: TuFBYW6vhfDm3PFpAPKOWTopdDIwrLp3r1ciqqqm
Notice: this ID appears to be an online ID, decryption is impossible
Please help! The decryptor is not working and showing this message each time I use it.
Your personal ID:
0217OIWojlj48TuFBYW6vhfDm3PFpAPKOWTopdDIwrLp3r1ciqqqm
Please tell me weather i can recover my .bds extension database files or not with your software. i am infected with ransomware attack all of my files are effected with it. Please help me
File: D:\quar\2011-12SGS-advertisement.pdf.mado
No key for New Variant offline ID: 8TaHEsq5r7cNJKbYdWseLEB2pW1FuZKoKjKg5tt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
I was attacked with a Mado ransomware
The day before, I contacted them and two files were recovered for free.
Most of my files are scientific researches I am a master’s in medical chemistry.
– How can the rest of the files be recovered?
How do I get rid of the virus? Can I do this when downloading the anti virus that you put in the article?
– Do you recommend formatting the memory?
After that, restore the files with the data recovery program?
If I format the memory, will the virus go out of memory?
my personal ID:
0217OIWojlj488TaHEsq5r7cNJKbYdWseLEB2pW1FuZKoKjKg5tt1
even if you delete or format the memory.
after you recover them,
same .mado files will come again. i.e., same encrypted files are going to recover.
example
my original file is abc.jpg
after it is encrypted it becomes abc.jpg.mado
after i delete/format
if i recover by any software
again same abc.jpg.mado will come not your original file.
The MADO offline key was uploaded to the server. Try to decrypt.
You can open your encrypted files via multi extractor
Please help me, all my file ekstention. mado
How to remove .MADO file
My all folder is .MADO
I am very unhappy.
Please help me
No key for New Variant offline ID: 8TaHEsq5r7cNJKbYdWseLEB2pW1FuZKoKjKg5tt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
We hope the key will be found soon.
i help .mado
I am also got caught in this same problem if you gets proper solution please mail me.
Help can i recover files?
Your personal ID:
0217OIWojlj48Lud2Pr8UERUdw6BFRWUwfskDNUJd0xitsgbveCCw
Kindly help me, recovering files effected from .mado virus. I lost my imporotant data.
can i recover my data of .MADO ?
ID:IctSwMHyRVQHBNE0fj3eiM6bd4FG8NesBYjy5GTf
File: D:\09092019\HTKK\DataFiles\0302362510\HEADER.xml.mado
No key for New Variant online ID: g7B4GGmWFHZujwxenYJhlkqe4aW5JdLAWerfLfQB
Notice: this ID appears to be an online ID, decryption is impossible
Error: No key for New Variant online ID: 7BbaAFoTkYb9w2YqvW5U4CmAChHryB0ZMZOlg26C
Notice: this ID appears to be an online ID, decryption is impossible
I already download the app but is not working. Please help!
Thank you
I cant decrypt my files, please help
No key for New Variant online ID: Vq1M8BSYjiydOggyOwJTrW76pW8ZKOMOYFBB5E3J
Notice: this ID appears to be an online ID, decryption is impossible