The Lumino_ransom virus belongs under the ransomware type of infection. Malware of this type encrypts all user’s data on the computer (images, text files, excel tables, audio files, videos, etc) and appends its extra extension to every file.
What is known about the Lumino_ransomvirus?
☝️ A strictly accurate denomination for the Lumino_ransom would be “a ransomware-type malicious agent”.
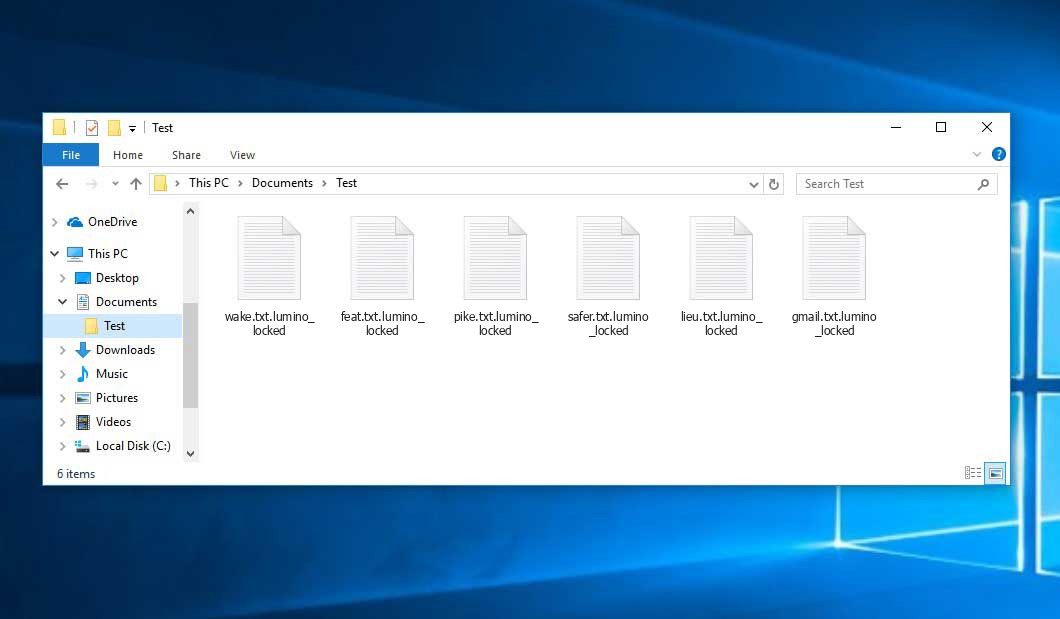
Lumino_ransom appends its specific .lumino_locked extension to the name of each encoded file. For example, a file named “photo.jpg” will be altered to “photo.jpg.lumino_locked”. Likewise, the Excel file named “table.xlsx” will be altered to “table.xlsx.lumino_locked”, and so forth.
The ransom note usually contains a description of how to buy the decryption tool from the racketeers. You can get this tool after contacting [email protected] by email. That is how they do it.
Lumino_ransom abstract:
| Name | Lumino_ransom Virus |
| Extension | .lumino_locked |
| Contact | [email protected] |
| Detection | Win32/Packed.BlackMoon.A suspicious, BScope.TrojanDownloader.Deyma, Mal/Kryptik-BX |
| Symptoms | Your files (photos, videos, documents) have a .lumino_locked extension and you can’t open them. |
| Fix Tool | See If Your System Has Been Affected by Lumino_ransom virus |
The note coming in package with the Lumino_ransom malware states the following:
Hi !!! Your file was encrypted by the ransomware: Lumino_Ransom, if you want to decrypt him, send me à mail with the user name pc at [email protected] and I give to you the password for free ; that you need to enter in Lumino_decrypt ! On the other hand, you have no luck, it\'s the Hard\'s version of my Ransomware that I\'ve created then... FR: Salut !!! Vos fichier on été encypté par le ransomware: Lumino_ransom, si tu veux les décryptés, envoie moi un mail avec ton nom d\'utilisateur à [email protected] et je te donnerais le mot de passe gratuitement ; qu\'il faudra entrer dans Lumino_decrypt ! Par contre, t\'as pas de chance, c\'est la version Hard mon Ransomware que j\'ai crée donc... The window/notepad gonna be closed automaticaly after 20 secondes ! La fenettre/le bloc note vas être fermée automatiquement après 20 secondes !
In the screenshot below, you can see what a directory with files encrypted by the Lumino_ransom looks like. Each filename has the “.lumino_locked” extension appended to it.
How did my computer get infected with Lumino_ransom ransomware?
There are many possible ways of ransomware injection.
There are currently three most popular ways for tamperers to have ransomware settled in your digital environment. These are email spam, Trojan introduction and peer networks.
If you open your inbox and see emails that look like familiar notifications from utility services companies, postal agencies like FedEx, web-access providers, and whatnot, but whose addresser is strange to you, be wary of opening those emails. They are very likely to have a harmful item enclosed in them. So it is even riskier to download any attachments that come with letters like these.
Another thing the hackers might try is a Trojan file scheme1. A Trojan is a program that infiltrates into your PC disguised as something else. For example, you download an installer for some program you need or an update for some software. But what is unboxed turns out to be a harmful program that compromises your data. As the update file can have any title and any icon, you have to make sure that you can trust the source of the stuff you’re downloading. The optimal thing is to use the software developers’ official websites.
As for the peer-to-peer networks like BitTorrent or eMule, the danger is that they are even more trust-based than the rest of the Web. You can never know what you download until you get it. So you’d better be using trustworthy websites. Also, it is reasonable to scan the directory containing the downloaded files with the anti-malware utility as soon as the downloading is done.
How do I get rid of the Lumino_ransom virus?
It is crucial to inform you that besides encrypting your files, the Lumino_ransom virus will probably deploy the Azorult Spyware on your computer to seize your credentials to different accounts (including cryptocurrency wallets). The mentioned program can derive your logins and passwords from your browser’s auto-filling cardfile.
Sometimes criminals would decode some of your files to prove that they do have the decryption tool. As Lumino_ransom virus is a relatively recent ransomware, safety measures designers have not yet found a method to reverse its work. However, the anti-ransomware instruments are frequently upgraded, so the solution may soon arrive.
Of course, if the criminals do the job of encrypting someone’s essential data, the desperate person will most likely comply with their demands. However, paying to criminals does not necessarily mean that you’re getting your blocked information back. It is still risky. After receiving the ransom, the racketeers may deliver a wrong decryption code to the victim. There were reports of racketeers just vanishing after getting the ransom without even writing back.
The optimal solution against ransomware is to have aan OS restore point or the copies of your essential files in the cloud disk or at least on an external disk. Surely, that might be not enough. Your most important thing could be that one you were working on when it all started. But at least it is something. It is also wise to scan your drives with the antivirus program after the system restoration.
Lumino_ransom is not the only ransomware of its kind, since there are other specimens of ransomware out there that act in the same manner. For instance, Oflg, Ofww, Towz, and some others. The two major differences between them and the Lumino_ransom are the ransom amount and the method of encryption. The rest is the same: documents become encoded, their extensions altered, ransom notes emerge in each directory containing encrypted files.
Some lucky users were able to decode the arrested files with the help of the free software provided by anti-malware experts. Sometimes the racketeers mistakenly send the decryption code to the victims in the ransom readme. Such an extraordinary fail allows the victim to restore the files. But of course, one should never rely on such a chance. Remember, ransomware is a bandits’ instrument to pull the money out of their victims.
How do I avert ransomware infiltration?
Lumino_ransom ransomware doesn’t have a superpower, neither does any similar malware.
You can protect yourself from ransomware attack within three easy steps:
- Never open any emails from unknown mailers with unknown addresses, or with content that has nothing to do with something you are waiting for (how can you win in a money prize draw without participating in it?). In case the email subject is more or less something you are expecting, check all elements of the questionable email with caution. A hoax letter will always contain mistakes.
- Never use cracked or untrusted software. Trojan viruses are often shared as a part of cracked software, most likely as a “patch” which prevents the license check. But dubious programs are difficult to tell from trustworthy software, because trojans sometimes have the functionality you need. Try to find information on this program on the anti-malware forums, but the best way is not to use such programs at all.
- And to be sure about the safety of the files you downloaded, scan them with GridinSoft Anti-Malware. This program will be a perfect defense for your personal computer.
Reasons why I would recommend GridinSoft2
There is no better way to recognize, remove and prevent ransomware than to use an anti-malware software from GridinSoft3.
Download Removal Tool.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your PC.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Lumino_ransom infections and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
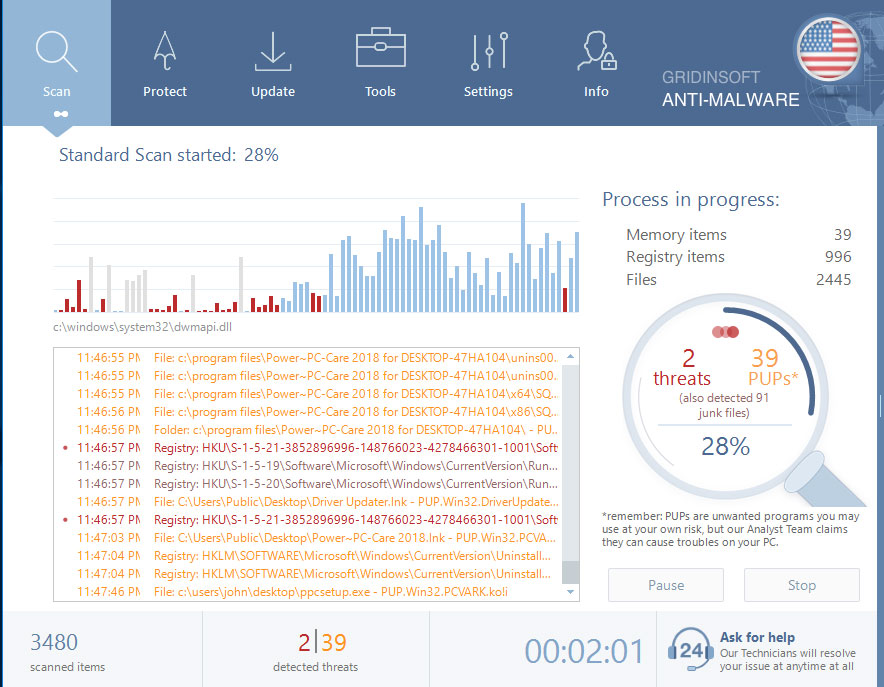
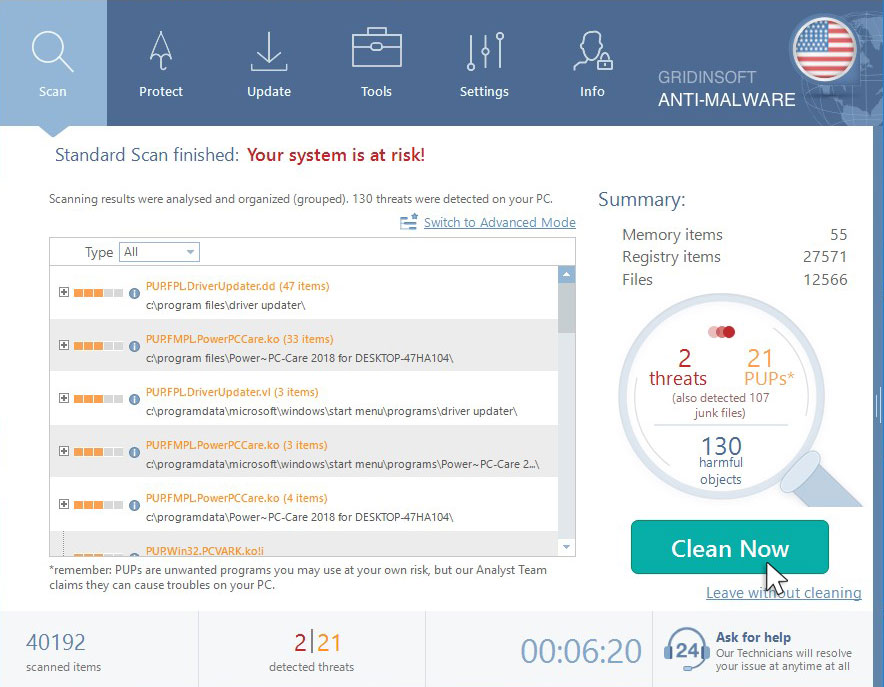
Click on “Clean Now”.
When the scan has completed, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
Frequently Asked Questions
🤔 How can I open “.lumino_locked” files?Is it possible to open“.lumino_locked” files?
Negative. That is why ransomware is so frustrating. Until you decode the “.lumino_locked” files you will not be able to access them.
🤔 The encrypted files are very important to me. How can I decrypt them quickly?
It’s good if you have fаr-sightedly saved copies of these important files elsewhere. Otherwise, you might try to employ System Restore. The only question is whether you have saved any Restore Points that would be helpful now. The rest of the methods require patience.
🤔 You have advised using GridinSoft Anti-Malware to get rid of the Lumino_ransom virus. Does it mean that all my files, currently encrypted, will be removed too?
Of course not. Unlike the ransomware program itself, the encrypted files do not jeopardize your system.
GridinSoft Anti-Malware only deals with active viruses. The ransomware that has infiltrated your PC is must be still functional and running scans every so often to encrypt any new files you might create on your computer after the attack. As it has been mentioned above, the Lumino_ransom ransomware comes with the company. It installs backdoors and keyloggers that can steal your account credentials and provide malefactors with easy access to your system after some time.
🤔 What actions should I take if the Lumino_ransom ransomware has blocked my PC and I can’t get the activation code.
In such a case, you need to have a memory stick with a previously installed Trojan Killer. Use Safe Mode to execute the procedure. You see, the ransomware runs automatically as the system boots and encodes any new files created or brought into your computer. To suppress this function – use Safe Mode, which allows only the vital programs to run automatically. Consider reading our manual on running Windows in Safe Mode.
🤔 What can I do right now?
Some of the blocked files can be found elsewhere.
- If you sent or received your important files by email, you could still download them from your online mailbox.
- You may have shared photographs or videos with your friends or family members. Simply ask them to give those images back to you.
- If you have initially downloaded any of your files from the Internet, you can try doing it again.
- Your messengers, social networks pages, and cloud drives might have all those files too.
- Maybe you still have the needed files on your old computer, a laptop, phone, memory stick, etc.
HINT: You can employ file recovery utilities4 to retrieve your lost information since ransomware blocks the copies of your files, removing the original ones. In the tutorial below, you can learn how to recover your files with PhotoRec, but remember: you can do it only after you eradicate the virus with an antivirus program.
Also, you can contact the following governmental fraud and scam sites to report this attack:
- In the United States: On Guard Online;
- In Canada: Canadian Anti-Fraud Centre;
- In the United Kingdom: Action Fraud;
- In Australia: SCAMwatch;
- In New Zealand: Consumer Affairs Scams;
- In France: Agence nationale de la sécurité des systèmes d’information;
- In Germany: Bundesamt für Sicherheit in der Informationstechnik;
- In Ireland: An Garda Síochána;
To report the attack, you can contact local executive boards. For instance, if you live in USA, you can have a talk with FBI Local field office, IC3 or Secret Service.
I need your help to share this article.
It is your turn to help other people. I have written this article to help people like you. You can use the buttons below to share this on your favorite social media Facebook, Twitter, or Reddit.
Brendan SmithHow to Remove LUMINO_RANSOM Ransomware & Recover PC

Name: LUMINO_RANSOM Virus
Description: LUMINO_RANSOM Virus is a ransomware-type infections. This virus encrypts important personal files (video, photos, documents). The encrypted files can be tracked by a specific .lumino_locked extension. So, you can't use them at all.
Operating System: Windows
Application Category: Virus
User Review
( votes)References
- You can read more on Trojans, their use and types in the Trojan-dedicated section of GridinSoft official website.
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison
- Here’s the list of Top 10 Data Recovery Software Of 2023.


Hi,
It’s me, the creator of Lumino_Ransom, and he is not so dangerous because the encryption of files is make by just a AES encrypt !
And for the decryption key, with me, it’s free !
hxxps://github.com/Lumino-2-0/LuminoWare/tree/main