One of the most successful ransomware groups of these days, Lockbit, reportedly committed a cyberattack on the regional governmental agency in the USA. Besides that goes against the “ethical hacking” rules this group tries to follow, the exact event took about 6 months to complete.
Lockbit group – what are they?
Lockbit is considered one of the most successful ransomware gangs in 2021. Having the software with outstanding performance and good coordination between units, it reached a lot of well-protected targets and successfully hacked them. The cybersecurity community knows them for having the fastest encryption module, and the use of elliptic curve encryption. Another notable thing about LockBit is its constant image care. During each interview, the group assures that they always give the decryption key and never attack government-related companies.
After the REvil group shutdown, they quickly consumed the released attack potential. In November 2021, the overall share of the LockBit group in total ransomware attacks on the corporations reached 40%. By the rules of “normal” markets that means a complete monopoly. Fortunately, this group opted for small-but-stable gains, attacking generally small companies and avoiding governmental, infrastructure, and educational institutions. At least, they did so up until uncovering the latest attack case.
LockBit attack lasted for half a year
Obviously, none of the ransomware attacks on corporations happen in one day. Usually, it is a chain of events for taking over the corporate network, stealing data, and encrypting the files. The average duration of cyberattacks is around 1 week. In some cases – when the network is well-protected, or the security system alarms about the attack – it may take a bit longer. But this time, LockBit has likely set up a record – more than 5 months since the initial penetration.
Sophos group specialists shared the report that shows the fraudsters did over a dozen steps. They’ve tested different hacktools, remote-access utilities and various programs for file transferring to the remote machine. The peculiar element of this event is that the first infected computer (so-called “patient zero”) was the domain controller. Usually, such an occasion means that the whole network is compromised. Even if it is not – using the DC crooks can create the administrator accounts on all machines in the network. And they apparently did that – but for some reasons, they decided to idle.
Tracing the longest attack
It is quite usual for cyberattacks to wipe the logs to prevent quick attack tracing. Sure, analysts will likely find the paths in other forms, but the initial slowdown gives the crooks several days or even weeks. Hackers who broke into the network did the same, but cybersecurity specialists who reviewed the attack recovered most of the steps they did.
Cybercriminals were thoroughly making their way into the network by choosing the tools to control the event. After that, they spend a lot of time trying different applications for file transfer and password hacking. They even approached hacked VPN clients and scripts that could possibly disable the anti-malware program running in the network. Fortunately for the company, they failed to delete it. Before the final act of that drama, crooks took a month-long vacation, and then were back with Mimikatz and the exact LockBit payload. The strangest thing is that there was no file encryption performed. All the hackers did is changed the file extension to the ransomware-specific, but without any ciphering. There were also two non-typical (for LockBit) ransom notes in the system.
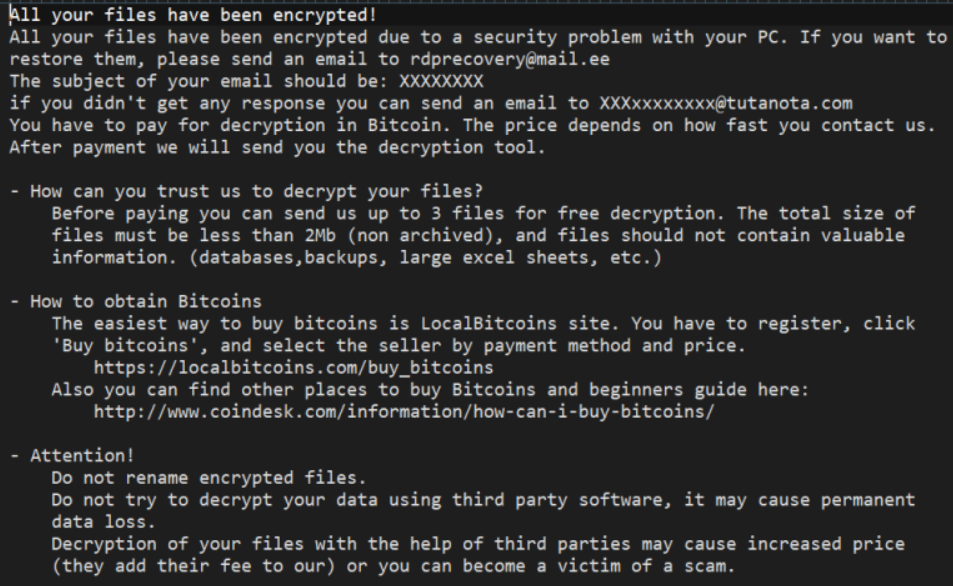
One of two ransom notes that crooks left in the infected system
The exact attack became possible because of the recklessness of the server’s maintainers. Specialists who did certain operations on this server left the important security feature disabled. And hackers did not miss such an opportunity. Sure, it is still a bit of coincidence – they left the breach, and crooks found it and successfully used it. As practice shows, it is quite hard to reach such conditions. But the term “perfect storm” exists for a reason.
Here is the list of software cybercriminals used during the attack:
- Advanced Port Scanner
- AnyDesk
- LaZagne
- Mimikatz
- ProcessHacker
- Putty
- Remote Desktop Passview
- ScreenConnect
- SniffPass
- WinSCP
Analysing the LockBit half-a-year-attack
Such a long period of time since the initial breaking to payload deployment is not a usual thing. It is hard to say for sure what was on the crooks’ minds, but logs analysis shows that they were trying to choose the utilities as best as they could. Triggering the EDR system that was running in that system meant a complete failure for them, so they tried to not to cut even a single tripwire. But the attack is still strange – at least because the supposedly LockBit hackers attacked the company which belongs to the sector they were obliged to avoid. And why did not they encrypt a thing? Too many questions, too few answers.