Firmware security company Binarly has discovered more than a dozen UEFI vulnerabilities on HP devices and probably other manufacturers.
The vulnerabilities were assigned 16 CVE IDs. The errors are stack overflows, heap overflows, and memory corruption that affect the UEFI Runtime Driver eXecution Environment (DXE) and System Management Mode (SMM) components. All bugs were assigned a “high severity” rating.
SMM Callout (privilege escalation):
- CVE-2021-39298: callout leading to privilege escalation (CVSS – 7.5);
- CVE-2021-23932: callout leading to privilege escalation (CVSS – 8.2);
- CVE-2021-23933: callout leading to privilege escalation (CVSS – 8.2).
System Management Mode (SMM):
- CVE-2021-23924: Heap buffer overflow leading to arbitrary code execution (CVSS – 8.2);
- CVE-2021-23925: Memory corruption leading to arbitrary code execution (CVSS – 8.2);
- CVE-2021-23926: Memory corruption leading to arbitrary code execution (CVSS – 8.2);
- CVE-2021-23927: Memory corruption leading to arbitrary code execution (CVSS – 8.2);
- CVE-2021-23928: Memory corruption leading to arbitrary code execution (CVSS – 8.2);
- CVE-2021-23929: Memory corruption leading to arbitrary code execution (CVSS – 8.2);
- CVE-2021-23930: Heap buffer overflow leading to arbitrary code execution (CVSS – 8.2);
- CVE-2021-23931: Heap buffer overflow resulting in arbitrary code execution (CVSS – 8.2);
- CVE-2021-23934 – Memory corruption leading to arbitrary code execution (CVSS – 8.2).
Driver eXecution Environment (DXE):
- CVE-2021-39297: Stack buffer overflow leading to arbitrary code execution (CVSS – 7.7);
- CVE-2021-39299: Stack buffer overflow leading to arbitrary code execution (CVSS – 8.2);
- CVE-2021-39300: Stack overflow leading to arbitrary code execution (CVSS – 8.2);
- CVE-2021-39301: Stack overflow leading to arbitrary code execution (CVSS – 7.7).
The issues affect a wide range of HP enterprise products, including desktops, laptops, PoS, and so on. Since DXE and SSM are activated before the operating system starts, any bugs in these components that exceed the privileges of the kernel OS can help bypass almost any protection.
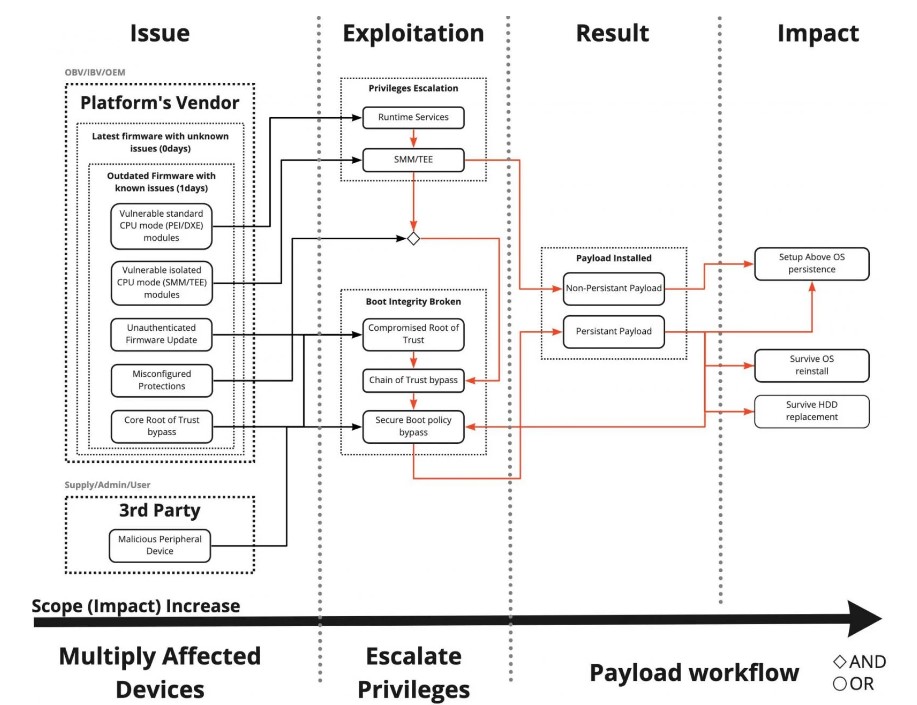
According to Binarly, exploitation of the vulnerabilities allows an attacker with user rights to execute arbitrary code at the firmware level, which can be useful for delivering stable malware to the system, bypassing endpoint security products, Secure Boot and products based on virtualization. HP also reports that exploitation of vulnerabilities can lead to denial of service (DoS) and information disclosure.
In addition, at least one of the vulnerabilities affecting HP systems also affects Dell devices: careful analysis showed that the vulnerability was present in a firmware driver provided by AMD. Thus, bugs can affect devices and other manufacturers using problematic code.
HP has already published two security bulletins and has started releasing firmware updates.
Recall that we also wrote that HP Fixed Critical Potential Worm Vulnerability in 150 Printer Models, and also that Thunderbolt PCs Can Be Hacked In Less Than 5 Minutes.
