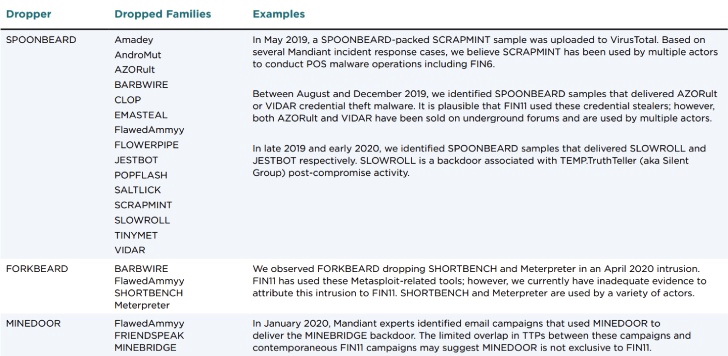
Experts from Mandiant (FireEye) have published a recent report that the FIN11 group, which has existed since 2016, usually pursuing financial gain in its attacks, is now engaged in ransomware attacks and infects company networks with the Clop ransomware.
The early FIN11 campaigns focused primarily on organizations in the financial, retail and restaurant sectors, but in recent years hackers have been less selective in targeting. Attackers now target a wide variety of companies in North America and Europe.For example, since August 2020, criminals have compromised companies in defense, energy, finance, healthcare and pharmaceuticals, law, telecommunications, technology and transportation.
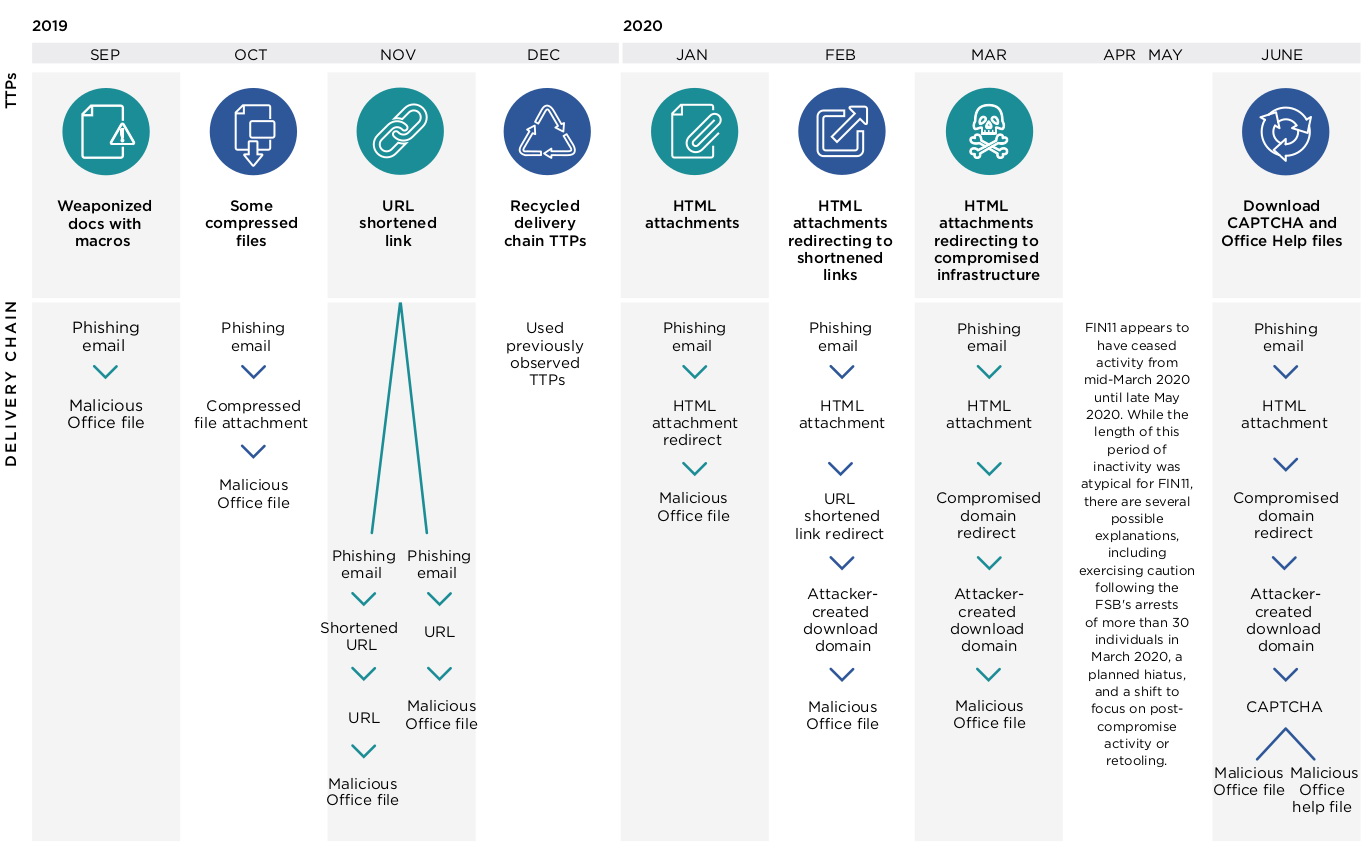
FIN11 attacks usually start with phishing emails, through which the FRIENDSPEAK malware downloader is distributed. Attackers’ emails contain a variety of decoys, including money transfer documents, invoices, or fake confidential bonus information.
In reality, such messages are bundled with malicious HTML attachments to download content (iframes or embedded tags) from compromised sites, which are often filled with outdated content and look abandoned. However, before downloading Excel with a malicious macro, the victim will be asked to solve the CAPTCHA.
The aforementioned FRIENDSPEAK, in turn, will download another malware to the user’s machine – MIXLABEL, which is also considered to be specific to FIN11. This malware is used to communicate with the domain of the command and control server, which is often disguised as the Microsoft Store (us-microsoft-store[.]сom).
Mandiant’s experts have discovered another interesting feature: after the victim’s networks were infected with the Clop ransomware, hackers do not back down. For example, in one case, attackers re-compromised an organization a few months after the first incident. In another case, FIN11 regained access to the company’s network after the victims restored the infected servers from their backups.
The researchers did not specify what ransom amounts are required FIN11 participants, but note that Coveware, which specializes in rehabilitating firms after ransomware attacks, reports amounts ranging from several hundred thousand to tens of millions of dollars.
Recently, TA505 has also been distributing the Clop ransomware and recently began exploiting the critical ZeroLogon vulnerability to gain domain controller administrator rights in the networks of compromised organizations.
Based on their own analysis, the researchers write that FIN11 is a Russian-speaking group that operates from some of the former-USSR countries. This theory is supported by the discovered metadata of files in Russian, the fact that hackers deploy the Clop ransomware only on machines with the layout used outside the former-USSR countries, as well as a clear decrease in the group’s activity during the Russian New Year and Orthodox Christmas holidays.
By the way, recently The Clop ransomware attacked the German Software AG company.