Troy Hunt, creator and operator of the well-known leak aggregator Have I Been Pwned (HIBP), says that from now on, the FBI will directly upload compromised passwords to the service database, which already contains more than 613 million passwords.
So, if the FBI discovers compromised passwords during its investigations, they are uploaded to the Pwned Passwords section. Law enforcers will provide passwords in the form of SHA-1 and NTLM hashes, and not in clear text. That is, no one will see the personal data of users.Whereas the main HIBP site allows users to check if their email, name, or username was involved in any data breaches, the smaller Pwned Passwords section reports specifically about compromised passwords, without linking the password to any user information.
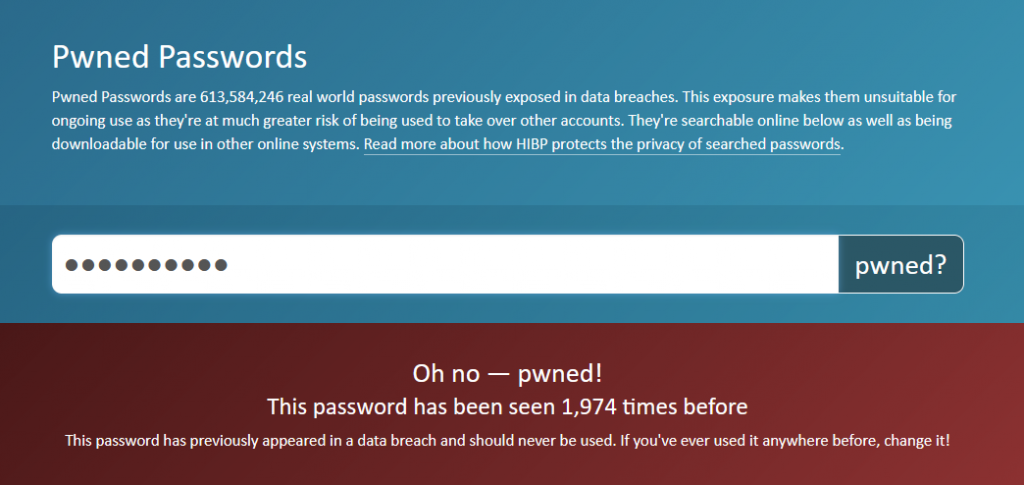
Although most people are familiar with the HIBP site mainly because of the search for leaked data, the Pwned Passwords section is even more useful and functional.
For example, currently 17 countries around the world use Pwned Passwords to check passwords for civil servants.
However, until recently, only information security researchers and anonymous informants provided Hunt with data for Pwned Passwords. The FBI is now the first official source to release data for this section of the HIBP.
Simultaneously with the conclusion of the partnership with the FBI, Hunt announced the opening of the source code for Pwned Passwords. In his blog, Hunt writes that this is pure coincidence, and the FBI did not require him to open source (the expert had been planning this since August last year).
The source code is now available on GitHub and will be uploaded to the .NET Foundation. Hunt promises that the sources for the main part of Have I Been Pwned will also be released in the near future, as he planned.
Let me remind you that earlier already FBI Shared 4 Million Emotet Email Addresses with Have I Been Pwned.
