The attackers pretend to be security researchers on Twitter and on GitHub, publishing fake PoC exploits for various zero-day vulnerabilities in the public domain. In fact, under the guise of exploits, hackers distribute malware that infects machines running Windows and Linux.
The experts from VulnCheck were the first to notice this malicious campaign. According to them, the attackers have been active since May 2023 and are actively promoting fake exploits for vulnerabilities in Chrome, Discord, Signal, WhatsApp and Microsoft Exchange online.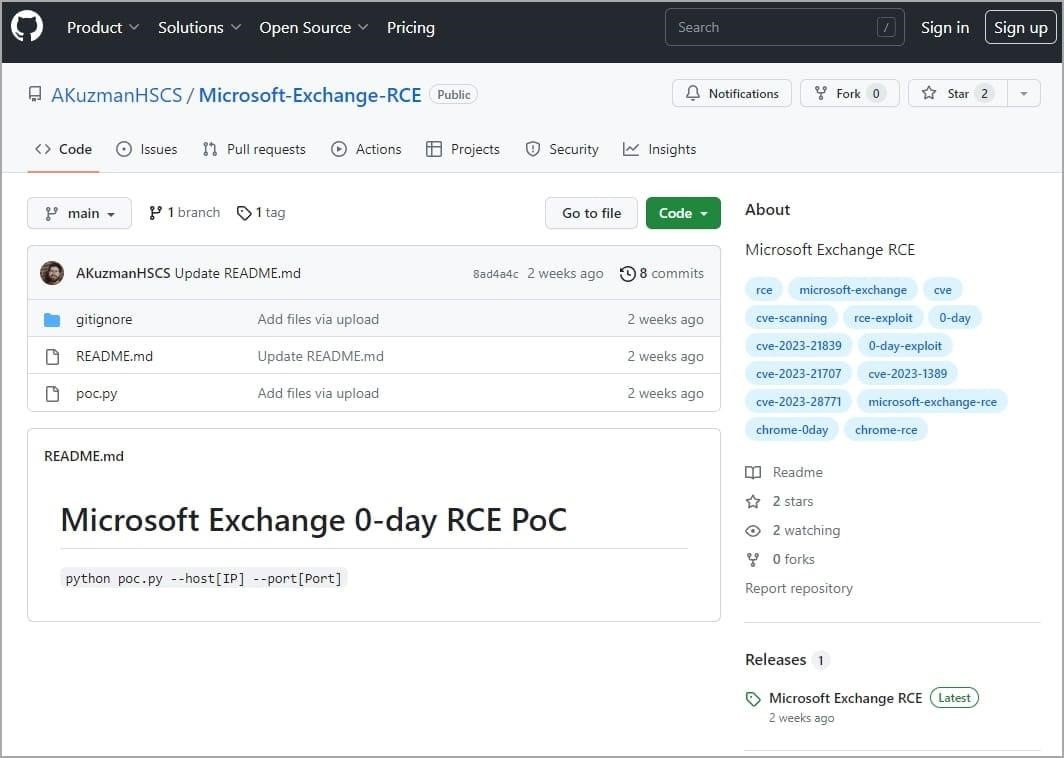
Malicious repository
Let me remind you that we also wrote that Miners abuse GitHub infrastructure, and also that Many Repositories on GitHub Are Cloned and Distribute Malware.
And also information security specialists pointed out that Attackers Can Use GitHub Codespaces to Host and Deliver Malware.
The fakes are spread on behalf of the defunct security company High Sierra Cyber Security and are actively promoted on Twitter so that researchers and vulnerability analysis firms are interested in them.
The hacker’s repositories seem legitimate, and their maintainers pose as real experts from Rapid7 and other well-known companies, even using real photos for this.

Fake Profile
In all the cases studied, the attacker’s repositories contain the poc.py Python script, which acts as a malware loader for Linux and Windows. The script downloads a ZIP archive to the victim’s computer from an external URL. Depending on the operating system, the target receives either cveslinux.zip (Linux) or cveswindows.zip (Windows).
As a result, the malware is stored in the %Temp% folder on Windows or /home/
It is not yet clear what type of malware the attackers are spreading, but both executables install the TOR client, and the Windows version is sometimes found to be a password-stealing Trojan.
Although the scope and effectiveness of this campaign is unclear, VulnCheck notes that the hackers are very aggressive in creating new accounts and repositories when the old ones are discovered and deleted.
There are currently seven GitHub repositories known to be owned by these attackers:
- github.com/AKuzmanHSCS/Microsoft-Exchange-RCE
- github.com/MHadzicHSCS/Chrome-0-day
- github.com/GSandersonHSCS/discord-0-day-fix
- github.com/BAdithyaHSCS/Exchange-0-Day
- github.com/RShahHSCS/Discord-0-Day-Exploit
- github.com/DLandonHSCS/Discord-RCE
- github.com/SsankkarHSCS/Chromium-0-Day
In addition, the following Twitter accounts are owned by hackers:
- twitter.com/AKuzmanHSCS
- twitter.com/DLandonHSCS
- twitter.com/GSandersonHSCS
- twitter.com/MHadzicHSCS
It is worth saying that this is not the first case of targeted attacks on information security experts and not the first case when hackers distribute fake exploits (1, 2). The fact is that by attacking members of the cybersecurity community, in theory, attackers not only gain access to data on vulnerability research (which the victim can work on), but can also gain access to the network of a cybersecurity company. And this can be a real gold mine for hackers.
