ESET analysts Denise Giusto Bilić and Cecilia Pastorino have studied and tested several sex toys and concluded that they are unsafe.
The researchers’ main concern stems from the fact that wearable devices and “smart” sex toys are equipped with numerous features, including Internet access and Bluetooth support, access to online conferences and instant messengers.All this opens up great opportunities for attackers who want to attack such devices.
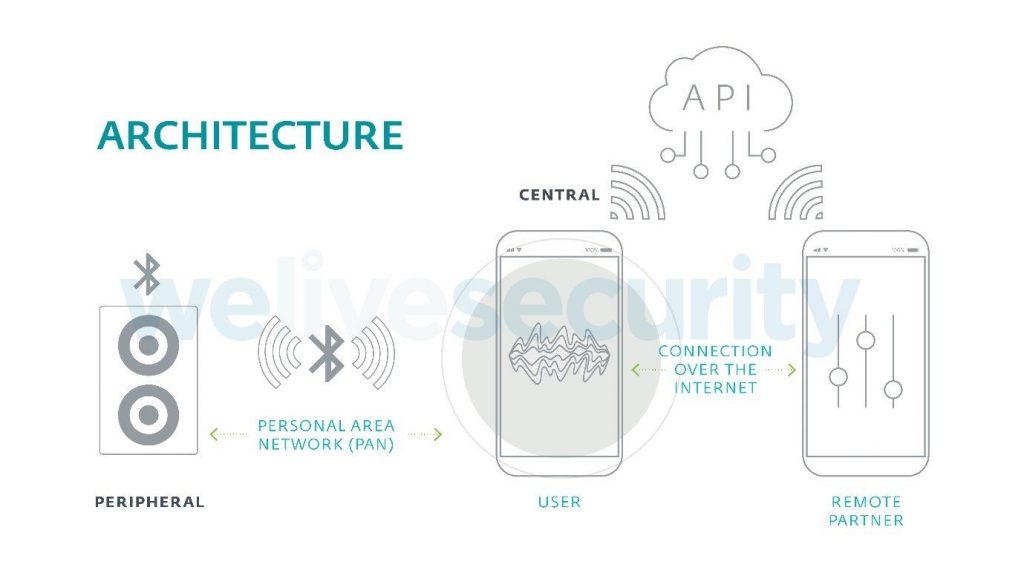
Experts write that most “smart” devices have two main communication channels. So, communication between the smartphone user and the device itself is via Bluetooth Low Energy (BLE) when the user launches the sex toy application. The connection between the remote sexual partner and the application that controls the device is established via the Internet.
To implement these functions, smart sex toys, like any other IoT device, use API endpoints that process requests.
At the same time, the information processed by sex toys consists of extremely confidential data, including the names of people, their sexual orientation, gender, a list of sexual partners, personal photos, videos, and so on. In short, this is a real treasure trove of data for malefactors, for example, engaged in “sexual extortion” (sextortion).
Worse, such IoT devices can be compromised and used for malicious activities, including physically harming the user. This can happen, for example, when a sex toy overheats.
To demonstrate the dangers of these security flaws, the researchers conducted their own tests on the Max sex toys from Lovense and We-Vibe Jive. It quickly became clear that both gadgets use the least secure Bluetooth connection method that is called Just Works.
Using the BtleJuice framework and two BLE dongles, the experts were able to demonstrate how an attacker can carry out a Man-in-the-Middle attack, take control of a device, and intercept packets. The hacker can then retransmit the modified packets by first changing the settings, including, for example, vibration mode and intensity, or even implementing their own commands.
Worse, it turns out that the API endpoints used to connect the remote peer to the user use a token that can be brute-forced.
This allows users to remotely control their devices by simply entering such URLs into the browser.
The devices also lack the end-to-end encryption and certificate binding used when receiving firmware updates.
Let me remind you that I talked about the fact that Sextortion ransomware writes letters in foreign languages to bypass filters.
