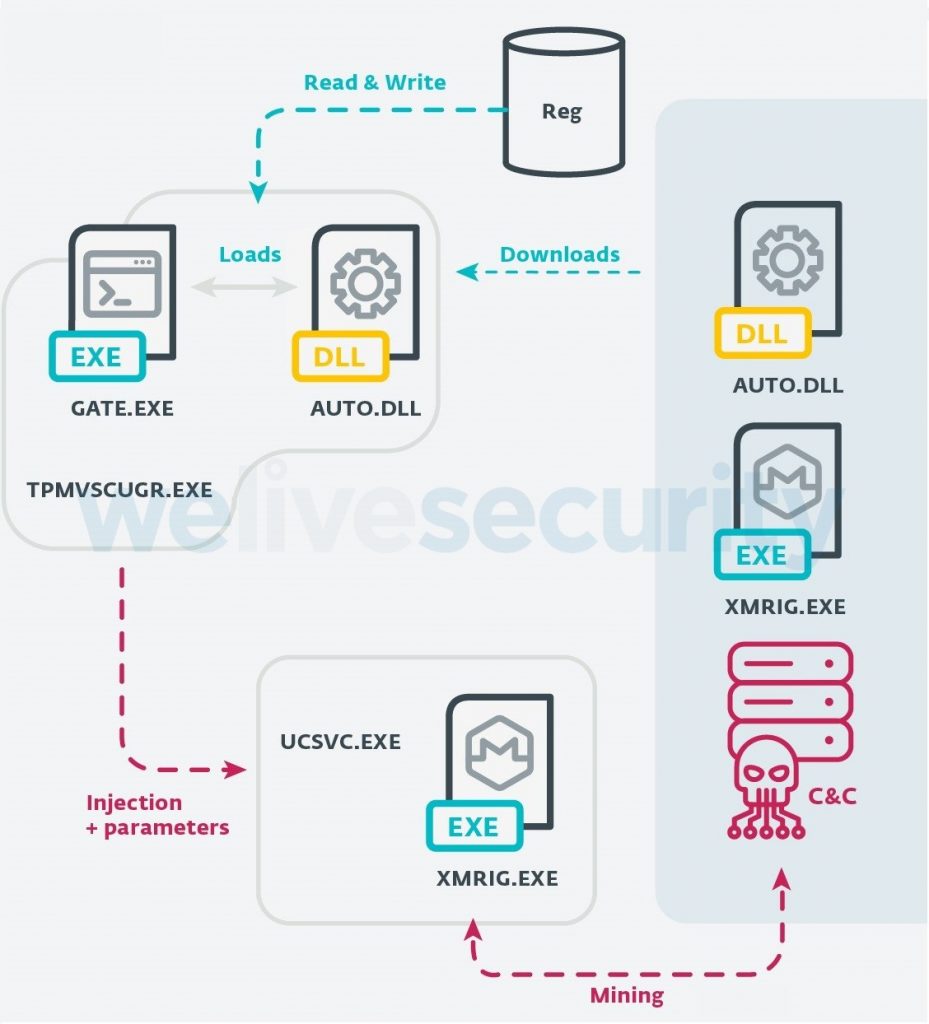
ESET analysts reported that they eliminated the VictoryGate botnet, which infected at least 35,000 machines and secretly mined the Monero cryptocurrency with their help.
According to researchers, the botnet has been active since May 2019, and most of its victims were in Latin America. So, computers in Peru accounted for more than 90% of the total number of infections.The botnet was managed through dynamic No-IP DNS. We managed to detect and disable the botnet’s managing server, and also create a fake (so-called sinkhole) to monitor and control previously infected hosts” – say ESET experts.
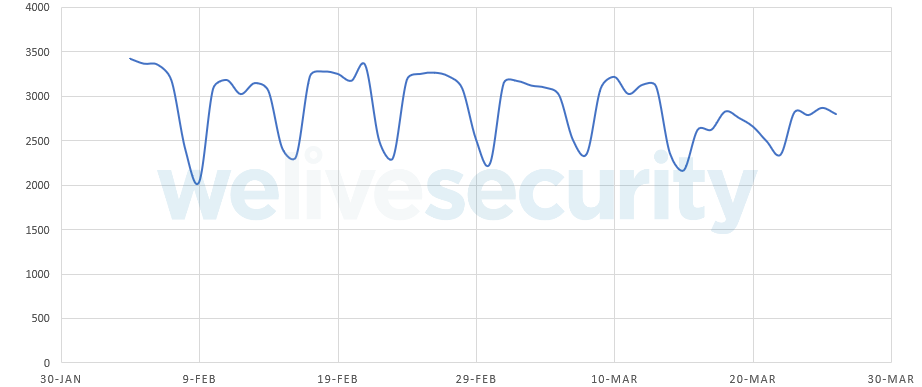
The company is currently working with the Shadowserver Foundation to notify the owners of all infected machines about the problem and eliminate malware from their computers. According to data from the sinkhole server, every day from 2000 to 3500 computers try to contact him to receive new commands.
Researchers write that they are still studying VictoryGate, because so far ESET specialists have been able to discover only one of the methods for distributing malware, which is not very common for the miner:
The only distribution vector that we were able to confirm was through removable media. That is, the victim receives a USB drive that was previously connected at some point to the infected machine. “ – write ESET researchers.
As a result, it seems that VictoryGate could have infected a whole batch of USB drives that were sent to Peru. VictoryGate contains a component that copies malware to new USB devices connected to an already infected computer, and thus the threat extends to new devices.
One of the interesting characteristics about VictoryGate is that it shows a greater effort to avoid detection than previous, similar campaigns in the region.
Despite our efforts, infected USB drives will continue to circulate and new infections will still occur. The main difference is that the bots will no longer receive commands from the C&C. This will prevent new victims from downloading secondary payloads from the internet. However, those PCs that were infected prior to the disruption may continue to perform cryptomining on behalf of the botmaster.” , — write ESET specialists.
According to the researchers, the authors of VictoryGate currently “earned” at least 80 Monero, that is, approximately $6,000 at the current rate.
Recall that earlier ESET experts introduced a free utility for detecting BlueKeep vulnerabilities.