Employee retention credit virus is a notorious name for the unwanted email spam you can get in your mail client. These messages consist of false claims about your employee retention credit program, where you were said that this policy for your company is changed. As the letter states, you can get the information in the attached Excel file. You will see the comprehensive description of this phishing, as well as the risks related to it in this article.
Employee retention credit is a special taxation program, offered to the corporations from the government. If the company retains its employees and keeps paying them the salary during the lockdown, it can pretend to get a 100% refundable tax credit. This thing allows the companies to save a lot of money during the pandemic. Nowadays we can hear more and more talks about the economy opening, so a lot of companies wait for the retention credit cancellation.
What is the employee retention credit virus?
The name that was assigned to this scam by nervous users does not mean that a person from IRS (Internal Revenue Service) has really peculated the credit program you have. The scammers who distribute TrickBot malware in such a method just choose this name to lull the vigilance. Name of the IRS is a famous thing, which is recognized trustworthy by a big number of users. And at the moment when the user gets this email, he/she will not even think that this is a fraud1. The possibility that a person will launch the file attached to this email is very high.
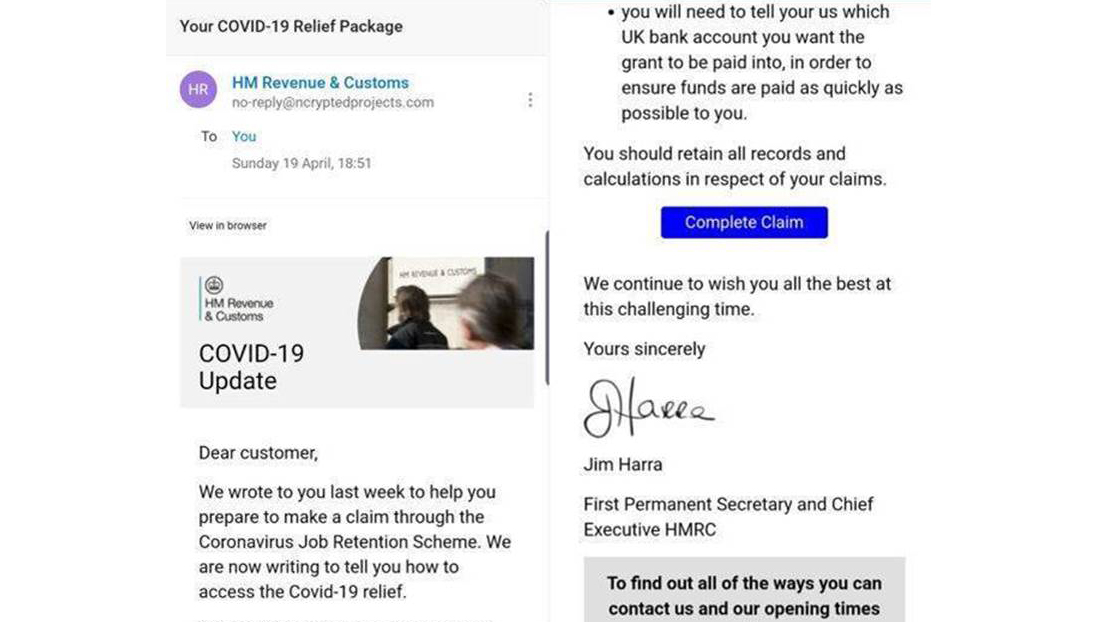
The employee retention credit virus spam message
The hysteria element is escalated by the text of the employee retention credit virus message: it says that the terms for the retention credit program for your company are changed. The reasons, as the message states, are listed in the attached Excel file, together with the scheme of taxation and list of changes. Everything looks legit, so the victim will likely open the attached file. The TrickBot virus is hidden in the macros element inside of the document. User sees the offer to enable macroses, and at this moment the virus begins its activity.
This is a notification from Internal Revenue Service (IRS)
Renewed taxation policies for all areas of business due to the Covid-19 Form1859-2021* kindly contact the Internal Revenue Service, details in attached document. IRS.
*Due to the new security measures, file can be opened on the PC ONLY (any web browser exept Edge and IE)
Sincerely, Wayne K. Smith Administrative Assistant Employee ID 3-81584 IRS Head Department
How dangerous the employee retention credit virus is?
Regardless of the stimulus the user clicked the link/file, he will download different viruses . The exact type of the virus is not related to the contents of the spam email, since all malicious items are distributed by the same cybercriminals. These viruses are just injected to your computer as a part of Microsoft Word file, directly from the email program or from the hyperlink added to the employee retention credit virus message. No complicated methods, like exploit kit usage – victims will do everything themselves.
Here is a short description of employee retention credit virus:
| Name | Employee retention credit virus |
| Type | Email spam |
| Hazard type | Spyware |
| Malware source | Infected Excel file attached to the email |
| Disguise | Notifications from IRS |
| Protection methods | To remove possible virus infections, try to scan your PC |
This malware spreading scheme is used to spread spyware, banking trojans and keyloggers. All of them are targeted on your personal information, in the majority of cases – on the critical logging keys. The second possible type of the virus can be the most harmful one if you use online banking. It is aimed on collecting the logging keys on the websites of the banks, so it can easily get your login/password. So, the fraudsters will be free to do whatever they want with your equity2. Meanwhile, spyware can ignore your banking login credentials, but will definitely get all possible info about you and your computer. List of the installed utilities, often-used apps, antivirus software onboard, logins and passwords for the social networks – this and a lot of other information will be collected and sent to the control server.
Can I avoid this scam?
The things are not so pessimistic for the employee retention credit virus. It is possible to distinguish the phishing email. First, you need to remember if you ever had a employee retention credit saving or deposit account. It may be very humorous to spectate such email spam when you don’t have one. However, some users may open the added file/link just because of the simple interest. People can do spontaneous acts, and this is just such a case. Another item which can help you to uncover that someone tries to scam you is the sender’s email address. Official IRS email address has a specific domain name, and the scammers will not be able to get an email address in this domain. Instead, fraudsters will likely create an email address like “irsofficial@gmail.com” or even “uasfbp12309@aol.com”. It is very easy to distinguish the first one from the second and third, isn’t it?
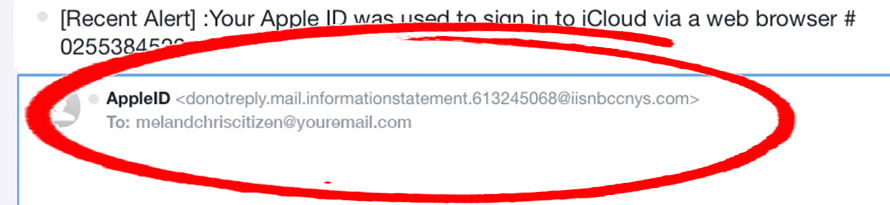
The example of dubious email address on another online spamming campaign
The final protection layer is an anti-malware software. A big number of users have their email chats in the separated app, called mail client. Some of that clients download the document at the moment when you open the message. In this case, you must have an anti-malware tool which has a function of proactive protection. Last function makes it possible to prevent the virus launching when the situation is just like I have described in this paragraph. Same thing is with attached links: to inform you that these links are malevolent, the security tool must have an internet protection option. All of these functions are available in GridinSoft Anti-Malware, and I will recommend you to use it to protect your personal computer from employee retention credit virus and similar hazards.
What can I do if I have clicked on the link/file in the spam email?
Don’t panic. The spyware activity is not a doom. Of course, the important data you have on your computer is definitely in danger, but the logging keys can easily be changed. First of all, you need to delete the viruses you have got through the employee retention credit virus. I can offer you to make use of GridinSoft Anti-Malware to perform this step.
Removing the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you can choose the action for each detected virus. For all files of the viruses distributed through the described phishing the default option is “Delete”. Press “Apply” to finish the malware removal.



Now, when the virus is removed, you need to remember which credentials you inputted after clicking the spam message. Malware is not omnipotent, and is not able to steal the logins and passwords which were not in use. So, keep calm and change the login details that are about to be compromised.
User Review
( votes)References
- About phishing methods and ways of counteraction.
- Detailed explanation of the banking trojans on Investopedia


