Bitdefender has released the MortalKombat ransomware decryptor, a free tool for victims of malware attacks.
This ransomware was first discovered in January 2023 by Cisco Talos experts and attacks mainly users from the United States.Let me remind you that we also talked about the fact that Emsisoft released a decryptor for SynAck ransomware, and also that The Kaseya company has a decryptor for the REvil ransomware. Also information security experts said that Free decryptor for BlackByte ransomware was published.
Basically, MortalKombat operators target casual users by sending out malicious emails with ZIP archive attachments containing BAT scripts. If such a script is launched, the ransomware binary and the Laplas Clipper malware (monitors the clipboard to steal cryptocurrency) are loaded, after which they are launched in the system.
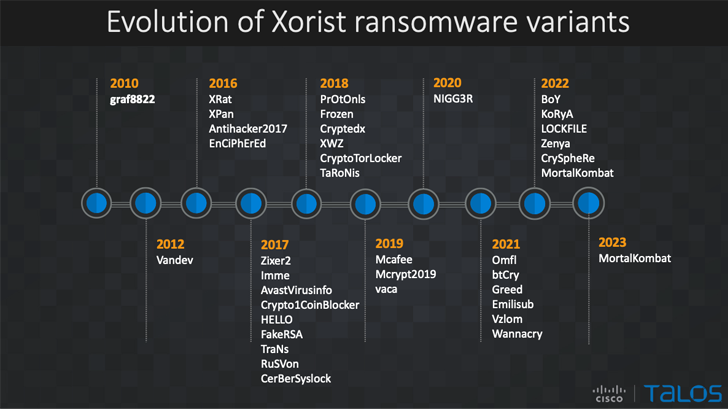
Apparently, the experts managed to hack MortalKombat so quickly, thanks to a feature that was noted back in Cisco Talos. The fact is that MortalKombat seems to be built on the basis of the Xorist ransomware malware, which cybersecurity specialists hacked back in 2016.
Xorist uses TEA (Tiny Encryption Algorithm) and XOR to work and attacks 57 different file types.
Despite the different file extensions, Xorist has a number of distinguishing features that make it difficult to confuse it with other malware. So, after infecting the victim, the malware requires the victim to send an SMS message containing a unique ID to a specific phone number. The attackers also send the code for decrypting information via SMS, and you need to enter it in a special pop-up window, the operation of which is initiated by the malware. The number of attempts to enter the code is limited: if you try to guess the password for decryption by brute force, you can lose your data forever.
This is all rather unusual (and a bit old-fashioned) as ransomware these days mostly prefers to use Tor and receive payments in bitcoin.
The decryptor for MortalKombat is a standalone executable file that does not require installation on infected devices. It offers to scan the entire file system to automatically find MortalKombat-infected files, but the user can also specify a specific location where encrypted data is backed up.
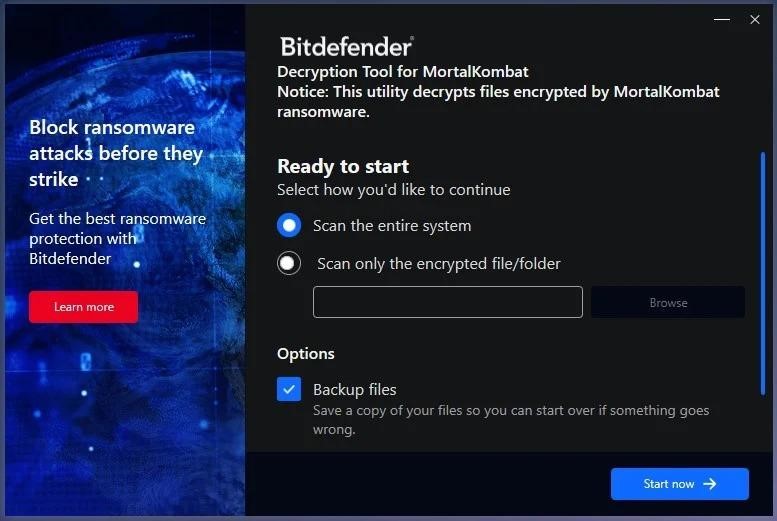
Bitdefender also notes that the decryptor can be run from the command line, which should make the data recovery process easier for companies that may need to bulk decrypt files on large networks or recover data from damaged operating systems.
