It was found that the certificates that Android OEM manufacturers Samsung, LG and Mediatek use to sign basic system applications were also used to sign malware.
Let me remind you that we also wrote that Hackers stole Mimecast certificate to attack Microsoft 365 users, and also that Critical vulnerabilities in HP Teradici PCoIP endanger 15 million endpoints.Google experts say that Android device OEMs use special certificates or keys to sign the main ROM images of devices containing the OS itself and related applications. When applications are signed with this certificate and assigned the highly privileged used ID android.uid.system, they gain access to the device at the system level.
Such privileges provide access to sensitive permissions that are not normally granted to applications: manage ongoing calls, install or remove packages, collect device information, and other similar actions.

Łukasz Siewierski
The misuse of such platform certificates was discovered by Łukasz Siewierski, a reverse engineer on the Android Security team.
Seversky found several samples of malware at once signed using the mentioned certificates and provided the SHA256 hashes for each of them. At the same time, it is not yet clear what led to the abuse of certificates: whether they were stolen by attackers, or an insider with the necessary access signed malicious APKs in this way. The detected malicious packages are listed below.
- com.russian.signato.renewis
- com.sledsdffsjkh.Search
- com.android.power
- com.management.propaganda
- com.sec.android.musicplayer
- com.houla.quicken
- com.attd.da
- com.arlo.fappx
- com.metasploit.stage
- com.vantage.ectronic.cornmuni
Also, there is no information yet on where these malware samples were found – in the Google Play Store, in third-party stores, or the malicious apps were distributed in some other way.
Bleeping Computer journalists checked the malware hashes through VirusTotal and found out that some of the abused certificates belong to Samsung Electronics, LG Electronics, Revoview and Mediatek. The ownership of other certificates has not yet been determined.
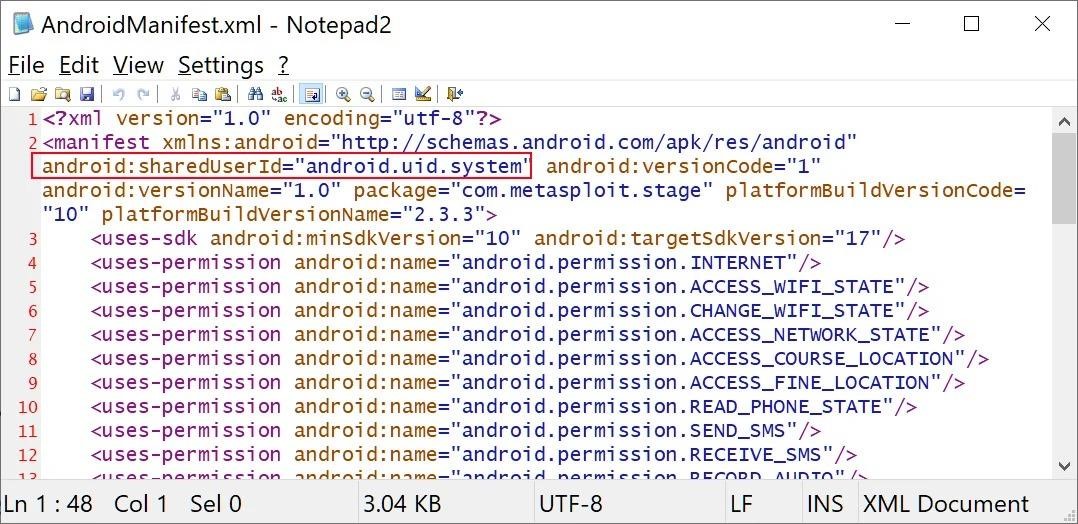
Malware with android.uid.system
Malware signed in this way includes Trojans from the HiddenAd family, unnamed infostealers, Metasploit, and droppers that attackers use to deliver additional payloads to compromised devices.
Journalists write that an easy way to get a list of all apps signed with compromised certificates is to use APKMirror (apps signed with a Samsung certificate, apps signed with an LG certificate).
Google says it has already notified all affected manufacturers of the abuse and recommended that they change their certificates and investigate the leak to minimize the number of applications signed with their certificates. According to the company, “all affected parties have already taken remedial action to minimize the impact on users.”
That being said, Bleeping Computer notes that not all vendors seem to have followed Google’s recommendations, as in Samsung’s case, compromised certificates are still being used to sign apps. Google assured journalists that they have already added tools to detect compromised certificates in the Android Build Test Suite (BTS), and malware will be detected through Google Play Protect.
The media also reported that Porn and gambling apps are also exploiting Apple’s Enterprise Certificate.
