Pulse Security consultant Denis Andzakovic discovered a critical vulnerability in the popular Untitled Goose Game. Australian developer from House House released the Untitled Goose Game on September 20 of this year, and the game...
Security
Microsoft: Russian hackers attack anti-doping organizations
Microsoft claims that Russian hackers from the Fancy Bear group (aka Strontium and APT28) are attacking anti-doping organizations ahead of the Tokyo Olympics next year. to the company, at least 16 anti-doping organizations have...
Chrome 78 cannot work with Symantec Endpoint Protection
Last week, Chrome upgraded to version 78, which brought support for DoH (DNS over HTTPS), the ability to enable forced dark mode for any sites, support for Password Checkup, and much more. However, Chrome 78 cannot work with...
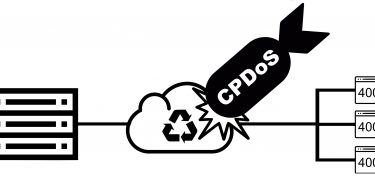
New CPDoS attack threatens sites that base on popular CDNs
Experts from the Technical University of Cologne described a new attack aimed at poisoning the web cache. According to them, a new CPDoS attack threatens sites that base on popular CDNs. problem possess a danger to the content...
Trend Micro Anti-Threat Toolkit will launch any malware if the file with it is called cmd.exe or regedit.exe
Researcher John Page, also known as hyp3rlinx, spoke about the discovery of the CVE-2019-9491 vulnerability affecting the Trend Micro Anti-Threat Toolkit (ATTK) and allowing arbitrary code execution. turns out that the software...
Facebook expanded bug bounty program for third-party services
Facebook expanded its bug bounty program for searching for bugs in third-party services integrated with the social network. Now researchers will be able to claim a reward for code errors that they have discovered both by passive...
Microsoft and NIST will teach business how to install patches
Microsoft and the US National Institute of Standards and Technology (NIST) will create practical guidelines for installing patches in enterprise infrastructures. Microsoft and NIST will teach businesses how to install patches...
Vulnerabilities in NTLM Could Allow Domain Compromise
Two vulnerabilities in Microsoft’s NTLM network authentication protocol allow bypassing of protection with the help of an insert, rollback of NTLM security functions to earlier versions and lead to domain compromise. fixed...