Experts from the Technical University of Cologne described a new attack aimed at poisoning the web cache. According to them, a new CPDoS attack threatens sites that base on popular CDNs.
The problem possess a danger to the content delivery network (CDN) and the sites that work with them, as it can force the CDN to cache and then serve error pages instead of legitimate resources.The attack is called CPDoS (Cache-Poisoned Denial-of-Service) and has three execution options that may well be put into practice.
“CPDoS attacks target two main components of the modern web: web servers and content delivery networks. So, if web servers store the source site and its contents, then the CDN stores a cached copy of the resource, which is updated at regular intervals. This helps significantly ease the load on web servers”, – say the researchers.
AS today CDNs are widely used, an attack on the CDN system can significantly affect the availability of the site and, consequently, affect its profit.
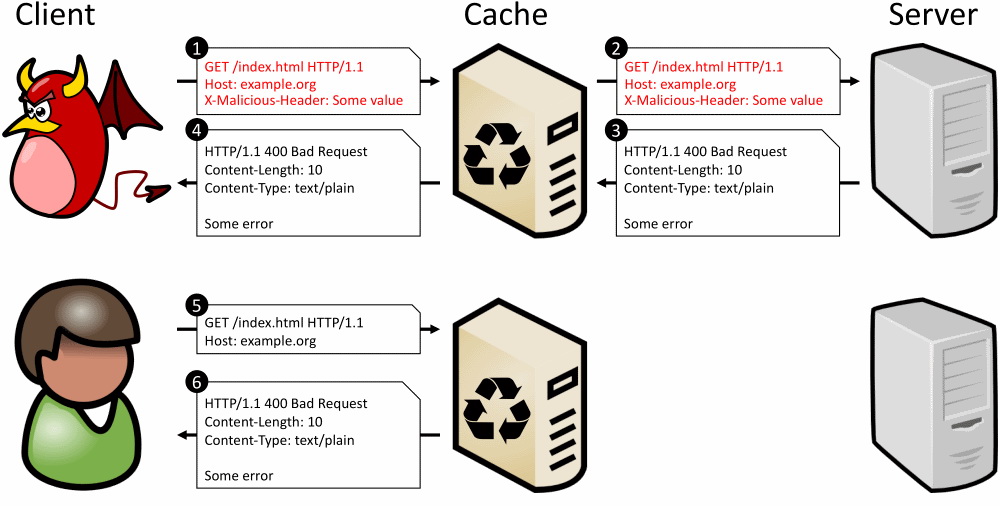
Thus, using CPDoS, criminals can implement the following scenario:
- an attacker connects to the site until his request generates a new CDN record;
- The attacker’s request contains a distorted or too large HTTP header;
- CDN allows this title to go through a legitimate site, and as a result, it can be processed and used to generate the web page that caches CDN;
- too large header provokes an error on the web server;
- the server generates a page with an error (error “400 Bad Request”);
- the error page is cached in the CDN;
- other users accessing the site see an error page instead of the real site;
- the cached error spreads to other nodes of the CDN network, creating a false disconnect on a legitimate site.
Researchers write that there are three types of CPDoS attacks that depend on how the attackers structure their distorted header: using large header fields, metacharacters that cause errors, or instructions that overwrite normal server responses:
- HTTP Header Oversize (HHO);
- HTTP Meta Character (HMC);
- HTTP Method Override (HMO).
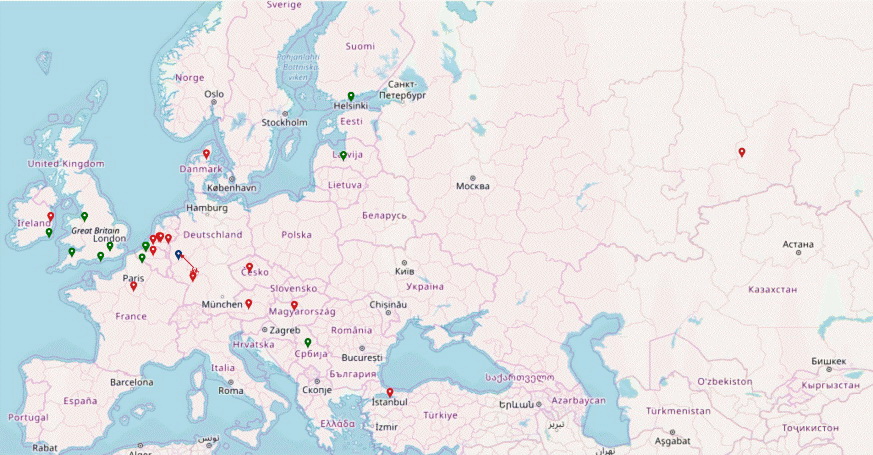
Interestingly, the experts were able to conduct large-scale tests of CPDoS attacks on a test site hosted on a network of several CDN providers.
Therefore, the map below shows that an attacker (danger symbol) launches an attack on the CDN server of a legitimate site (blue marker), which distributes a page with a cached error to other CDN servers (red markers), poisoning most of the provider’s network.
Fortunately, not all web servers (implementations of the HTTP protocol) and CDN providers are vulnerable to CPDoS attacks.
How to resist attacks?
It’s not so difficult for website owners to resist CPDoS attacks: just configure your CDN provider so that HTTP error pages are not cached by default. Many CDN service providers have the appropriate settings in the control panel, so this is not a difficult task. You can also disable this in the server configuration files by adding the HTTP header “Cache-Control: no-store” to each type of error page.
For CDN providers, the root of the problem is that the web caching standard allows CDNs to cache only 404 Not Found, 405 Method Not Allowed, 410 Gone, and 501 Not Implemented error codes, while CDN should not cache 400 pages Bad Request ”generated during CPDoS attacks. Alas, not all CDNs follow the standard, which leads to problems.
According to researchers, 30% of Alexa Top-500 sites, 11% of the US Department of Defense domains, and 16% of 365 million URL samples from the Google Big Query archive show potential vulnerability to CPDoS attacks.