BloodyStealer Malware, which can accurately be categorized as a stealer, is a dangerous virus that has gained immense prevalence in recent times. Numerous cybercriminals utilize this virus to pilfer your data, making it a significant threat. In this post, I will provide you with a comprehensive review of this virus, along with effective strategies to prevent its infiltration.
What is BloodyStealer?
BloodyStealer represents a classic example of a trojan-stealer that specifically targets your personal data, including login credentials, browser cookies, and other vital information. Additionally, this virus possesses the ability to gather details about your PC configuration, such as hardware specifications, installed programs, and session logs from gaming platforms like Steam and Origin. Furthermore, malware analysts affirm that the BloodyStealer virus is also capable of capturing screenshots.
BloodyStealer is a malware that specializes in stealing sensitive information from infected systems. It targets various types of data, including cookies, passwords, autofill forms, and saved maps from web browsers. In addition to browser data, BloodyStealer also targets computer-specific information such as details about installed hardware and software. It has the capability to extract session data from popular platforms like Bethesda, EpicGames, GOG, Origin, Steam, Telegram, and VimeWorld clients. Furthermore, the malware can access and retrieve text (.txt) files stored on the desktop and even capture screenshots of the infected system.
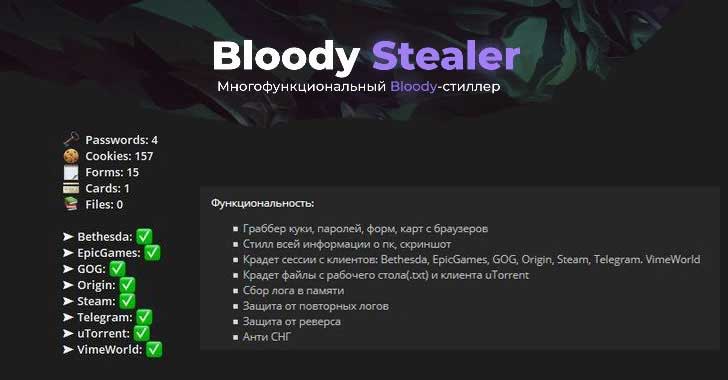
BloodyStealer on the hacker forum
Short info
| Name | BloodyStealer |
| Type | Trojan-stealer |
| Detection name | Microsoft (Trojan:Win32/Wacatac.B!ml), Kaspersky (HEUR:Trojan-Spy.MSIL.Stealer.gen), BitDefender (Gen:Variant.Bulz.412085), Emsisoft (Gen:Variant.Bulz.412085 (B)) (BloodyStealer on VirusTotal) |
| Malware source | Infected file attached to the email, hacktools and riskware |
| Protection methods | To remove possible virus infections, try to scan your PC |
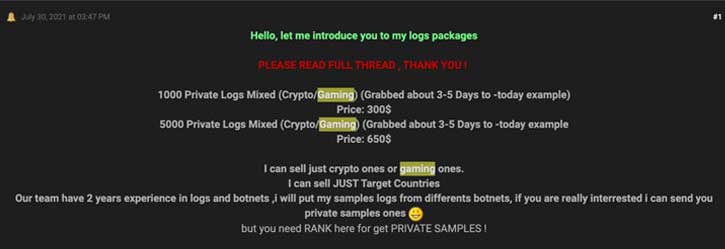
BloodyStealer Sell Logs
All information which BloodyStealer takes from the victim’s PC it sends to attackers through Telegram. Becoming such an attacker is possible through hackers forums, such as infected-zone[.]com. On that forum, this stealer is offered with a subscription: $10 for monthly and $40 for lifetime one. Pretty fair business model, isn’t it?
Message from Infected Zone forum
The total damage which BloodyStealer deals during the attack is huge. That virus is able to nuke all your privacy, so all your accounts in social networks, as well as online banking accounts and emails will be compromised. All data about your daily activities, such as working in the programs or gaming will be visible for crooks. And the most critical thing is credentials theft. One day you may discover that you cannot log in your Twitter account, and there are several strange money transfers from your bank account.
How did I get BloodyStealer malware?
Cybercriminals spread BloodyStealer massively through email spamming. Such a trend is caused by the fact that people trust the email notifications. Malware distributors disguise their emails as shipping notifications from Fedex, or alerts from Citibank about the changes in your account. In addition, they add several logotypes of the companies they mimic, to completely lull the vigilance. That’s why the mentioned spamming campaigns are so effective and profitable for their establishments.
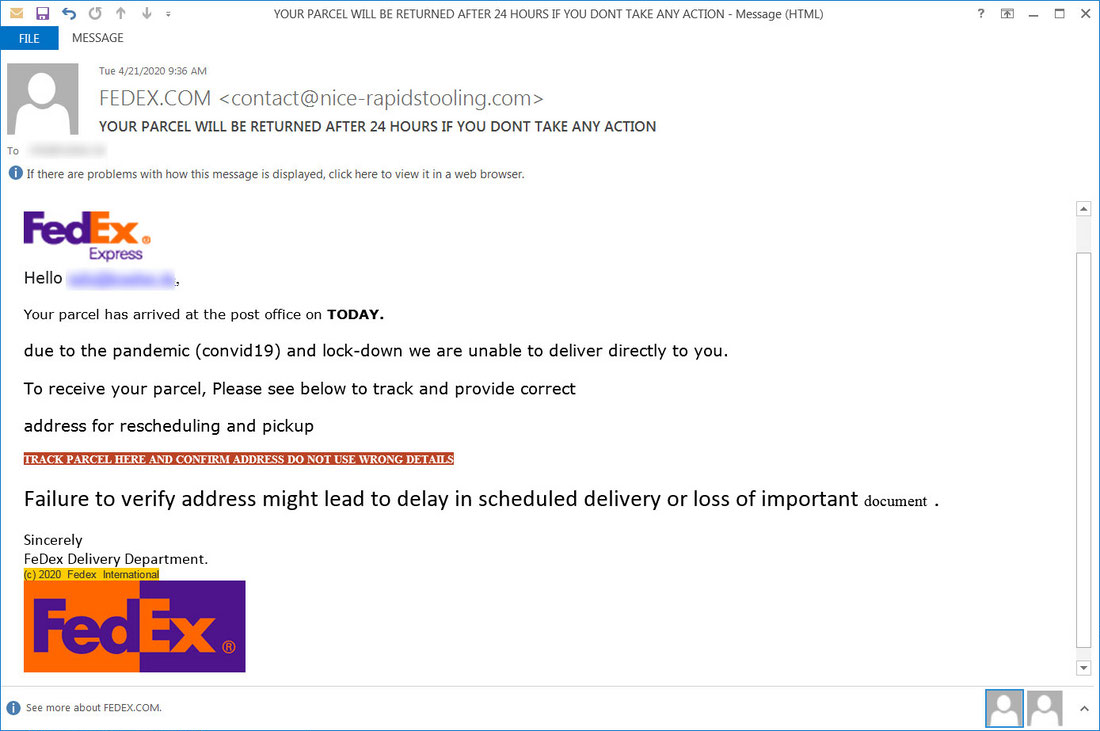
Fake Fedex email with shipping information
But the email spam is a new distribution channel, that does not cancel other distribution ways. Second method by popularity is a hacktools/riskware. Programs like KMSPico/KMS Activator, keygens and cheat engines for different programs and games are a perfect shell for the BloodyStealer, as well as any other stealer. The aforementioned programs may even have declared functions, but the virus will still be in it. Such disguise is an ultimate for malicious targets, since hacktools themselves are usually detected by the anti-malware software. To use these applications, users are forced to stop the antivirus or add the app to the whitelist. So, when the victim discovers the fact of malware activity, it is too late for any countermeasures.
How can I avoid the virus installation?
It is not very hard to uncover the email spamming. Fraudsters try to mimic the companies, but they are not able to get the same email address. You can just check the true email in the messages you have got before, and compare it with the address in a dubious email. Another way to avoid these fraudulent emails is to remember if you really have any incoming deliveries. Crooks can barely have the information if you are waiting for shipments, so it is easy to understand that someone tries to fool you.
In situations where you are not able to prove the benevolence of the email, you can try to download the file they are offering. By default, the typical source of malware in Office documents – macros – are disabled. If the document offers you to enable macroses, ignore this ask and close the document. There is no use for macroses in shipping information, so it is definitely a virus.
How to remove the BloodyStealer from my PC?
This virus hides deeply in the system, so it is likely impossible to remove it manually. The best solution is to use anti-malware software. For BloodyStealer removal, it is recommended to use GridinSoft Anti-Malware.
Remove BloodyStealer with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common Spyware as shown from our tests with the software, and we assure you that it can remove BloodyStealer as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file.
3.Follow the installation setup wizard's instructions diligently.
4. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
5. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
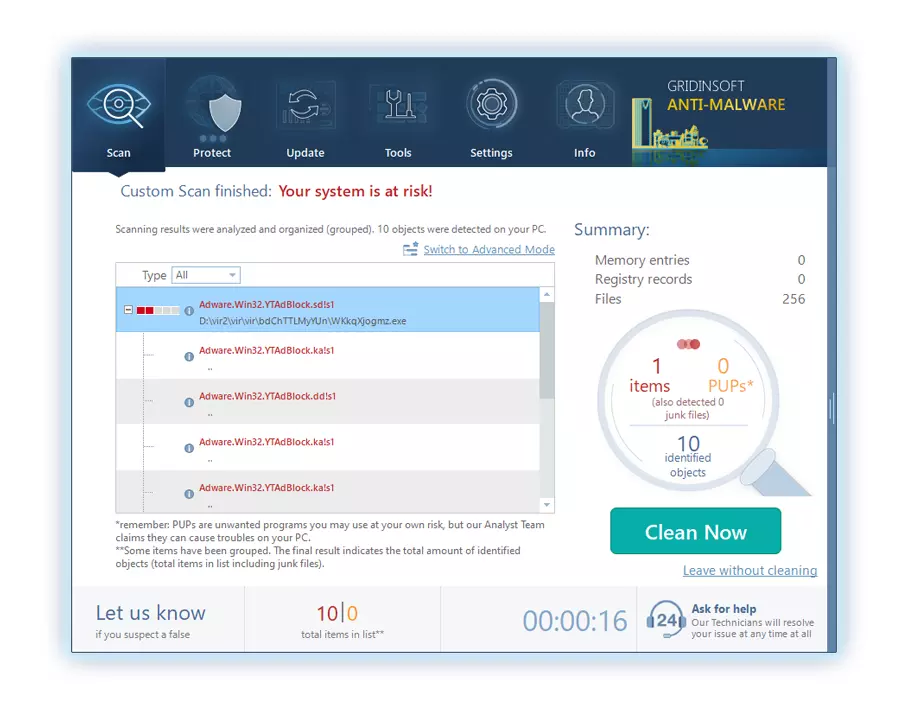
6. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
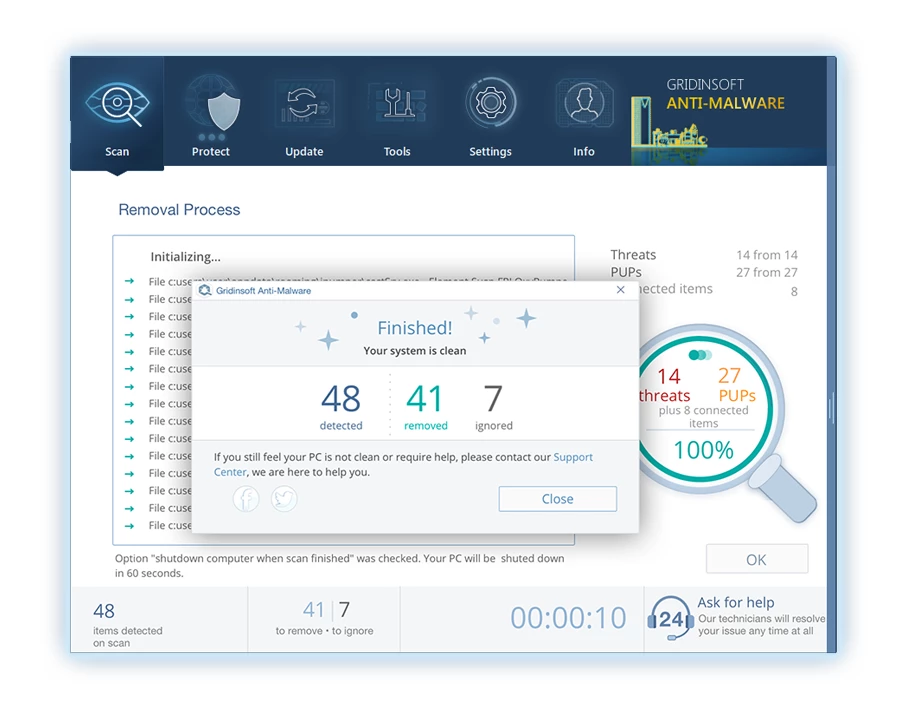
8. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
Trojan Killer for “BloodyStealer” removal on locked PC
In situations where it becomes impossible to download antivirus applications directly onto the infected computer due to malware blocking access to websites, an alternative solution is to utilize the Trojan Killer application.
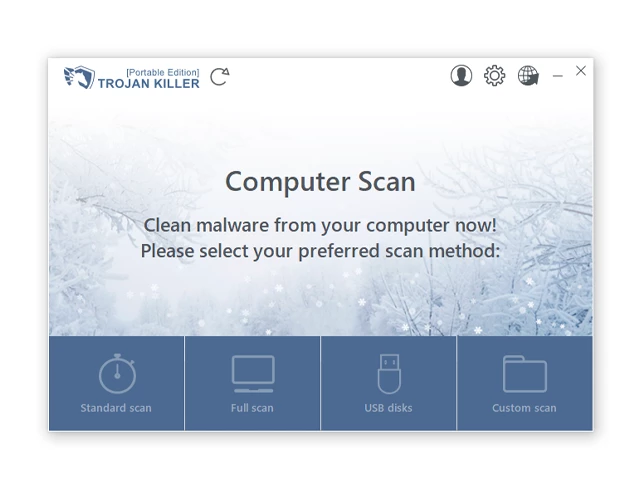
There is a really little number of security tools that are able to be set up on the USB drives, and antiviruses that can do so in most cases require to obtain quite an expensive license. For this instance, I can recommend you to use another solution of GridinSoft - Trojan Killer Portable. It has a 14-days cost-free trial mode that offers the entire features of the paid version. This term will definitely be 100% enough to wipe malware out.
Trojan Killer is a valuable tool in your cybersecurity arsenal, helping you to effectively remove malware from infected computers. Now, we will walk you through the process of using Trojan Killer from a USB flash drive to scan and remove malware on an infected PC. Remember, always obtain permission to scan and remove malware from a computer that you do not own.
Step 1: Download & Install Trojan Killer on a Clean Computer:
1. Go to the official GridinSoft website (gridinsoft.com) and download Trojan Killer to a computer that is not infected.
2. Insert a USB flash drive into this computer.
3. Install Trojan Killer to the "removable drive" following the on-screen instructions.
4. Once the installation is complete, launch Trojan Killer.
Step 2: Update Signature Databases:
5. After launching Trojan Killer, ensure that your computer is connected to the Internet.
6. Click "Update" icon to download the latest signature databases, which will ensure the tool can detect the most recent threats.
Step 3: Scan the Infected PC:
7. Safely eject the USB flash drive from the clean computer.
8. Boot the infected computer to the Safe Mode.
9. Insert the USB flash drive.
10. Run tk.exe
11. Once the program is open, click on "Full Scan" to begin the malware scanning process.
Step 4: Remove Found Threats:
12. After the scan is complete, Trojan Killer will display a list of detected threats.
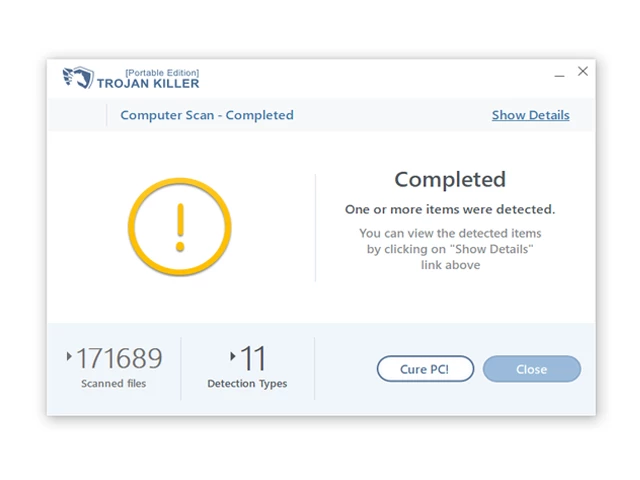
13. Click on "Cure PC!" to remove the identified malware from the infected PC.
14. Follow any additional on-screen prompts to complete the removal process.
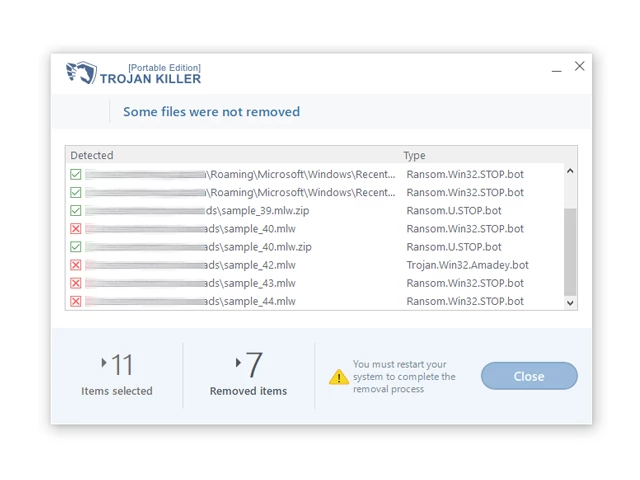
Step 5: Restart Your Computer:
15. Once the threats are removed, click on "Restart PC" to reboot your computer.
16. Remove the USB flash drive from the infected computer.
Congratulations on effectively removing BloodyStealer and the concealed threats from your computer! You can now have peace of mind, knowing that they won't resurface again. Thanks to Gridinsoft's capabilities and commitment to cybersecurity, your system is now protected.
Frequently Asked Questions (FAQ) about the BloodyStealer Virus
What is the BloodyStealer virus?
The BloodyStealer virus is a dangerous form of malware that falls into the category of trojan-stealers. It is designed to steal personal data, including login credentials, browser cookies, and other important information. This virus can also gather details about your computer’s configuration and capture screenshots.
How does the BloodyStealer virus spread?
The BloodyStealer virus primarily spreads through various methods, such as malicious email attachments, software downloads from untrusted sources, or by exploiting vulnerabilities in outdated software. It is essential to exercise caution while opening email attachments or downloading files from the internet to prevent infection.
What are the potential risks of the BloodyStealer virus?
The BloodyStealer virus poses significant risks to your personal and financial security. By stealing your login credentials and personal information, cybercriminals can gain unauthorized access to your accounts, leading to identity theft, financial loss, or unauthorized use of your sensitive data.
How can I protect my computer from the BloodyStealer virus?
To protect your computer from the BloodyStealer virus, follow these preventive measures:
- Keep your operating system and software up to date with the latest security patches.
- Use a reliable antivirus or antimalware program and keep it regularly updated.
- Exercise caution while opening email attachments or clicking on suspicious links.
- Download software only from trusted sources.
- Enable a firewall and configure it to block unauthorized access.
- Regularly backup your important data to an external storage device or cloud service.
If my computer is infected with the BloodyStealer virus, what should I do?
If you suspect that your computer is infected with the BloodyStealer virus, take the following actions:
- Disconnect your computer from the internet to prevent further data theft or unauthorized access.
- Run a full system scan using an updated antivirus or antimalware program.
- If the virus is detected, follow the recommended actions provided by the security software to remove it.
- Change all your passwords for online accounts to prevent unauthorized access.
- Monitor your financial accounts for any suspicious activity and report it to your bank or credit card provider.
- Consider seeking assistance from a professional computer security expert if needed.
User Review
( votes)



