One of the most popular WordPress plugins, Essential Addons for Elementor, was vulnerable to an unauthenticated privilege escalation that allowed attackers to gain administrator rights on the vulnerable site. me remind you that...
Author - Emma Davis
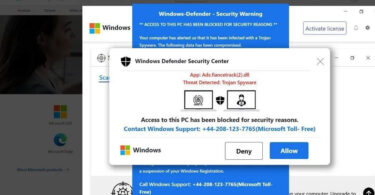
Don’t Fall for the App Ads.fiancetrack(2).dll Tech Support Scam
Do you have concerns about the fake alert of App Ads.fiancetrack(2).dll? This deceptive tactic is known as a browser-based scam, which aims to deceive individuals into calling a fake Tech Support Scam phone number. Here is...
The FBI Destroyed the Snake Spyware Created by the Russian Group Turla
The FBI reported that the countries participating in the Five Eyes alliance (which brings together the intelligence services of Australia, Canada, New Zealand, the US and the UK) destroyed the infrastructure used by the Snake...
Update Windows Urgently: Microsoft Fixes Two Exploited Vulnerabilities and One Disclosed
On Tuesday, Microsoft released 38 security updates, among which it fixed two vulnerabilities that attackers are already exploiting. addition, another vulnerability was disclosed, which has not yet been exploited. We recommend...
Critical Vulnerability in Cisco Phone Adapters Will Not Be Fixed
Cisco warns of a critical vulnerability in the web interface of the SPA112 Dual Port Phone Adapters. issue allows a remote, unauthenticated attacker to execute arbitrary code. Since the support period for the Cisco SPA112 has...
Hackers Use a Five-Year-Old Vulnerability in TBK’s DVR Devices
Fortinet experts have warned that attackers are actively exploiting an unpatched authentication bypass vulnerability discovered in TBK DVR devices in 2018. me remind you that we also wrote that Researchers Discover 22-Year-Old...
Researchers Discovered a Number of Problems in the BGP Protocol
Researchers have discovered a number of serious problems in the software implementation of the Border Gateway Protocol (BGP) that can be used to induce a denial of service (DoS) on vulnerable BGP peers. me remind you that we also...
VMware Fixes Vulnerabilities in Workstation and Fusion
VMware, the largest developer of virtualization software, has released updates to fix a number of vulnerabilities in Workstation and Fusion. other bugs, a 0-day issue was fixed, which was discovered by experts during the Pwn2Own...
GhostToken Vulnerability Allowed Creating a Backdoor for Any Google Account
Google has fixed a dangerous GhostToken vulnerability in the Google Cloud Platform (GCP). The problem affected all users and allowed attackers to create backdoors for other people’s accounts using malicious applications...
Google Fixes the Second 0-Day Vulnerability in Chrome in a Week
Google released yet another update for the Chrome browser, eliminating the second 0-day vulnerability in the last seven days. It is reported that an exploit already exists for the fresh issue, and hackers used it. new 0-day...