“All your data is backed up..” is a message that developers may see in their MongoDB instead of the data they uploaded there. Fraudsters who did this threatening that they will send the report to GDPR if you will not pay them a ransom. In fact, you likely can just skip that thing. But it is also recommended to do some adjustments to your workspace to avoid such things in future.
What is “All your data is backed up..”?
If you see the “All your data is backed up” message in your database, you are likely using MongoDB and have left your database unsecured. Crooks who are hunting for reckless developers check the ability to reach your DBs through port 27017. This port is used in MongoDB by default for external connections. Having an unsecured database with user’s data is forbidden by the General Data Protection Regulation (GDPR). Due to the laws, all personal data of users must be stored securely – ciphered, for example.
The example of MongoDB interface
Hackers try to find the unciphered bases, connecting through port 27017 and checking all databases you have. Sure, they can do nothing to ones that are ciphered. But when you have one or several DBs unsecured, they immediately do their filthy job. First, those fraudsters copy the unsecured data on their disk, then remove it from your DB, and leave the ransom note. The text of this note is following:
All your data is a backed up. You must pay 0.02 BTC to 19sPh8TP3RKHkEG2x9y8y1yXHTChMgrSXU 48 hours for recover it. After 48 hours expiration we will leaked and exposed all your data. In case of refusal to pay, we will contact the General Data Protection Regulation, GDPR and notify them that you store user data in an open form and is not safe. Under the rules of the law, you face a heavy fine or arrest and your base dump will be dropped from our server! You can buy bitcoin here, does not take much time to buy https://localbitcoins.com or https://buy.moonpay.io/ After paying write to me in the mail with your DB IP: [email protected] and you will receive a link to download your database dump
Analyzing the “All your data is backed up” ransom note
As you can see, this note contains a lot of grammar mistakes. It seems that these crooks are somewhere from CIS countries – Russia, Ukraine or so. Those countries are considered as a source of the majority of malicious stuff. Nonetheless, their claims about the punishment from GDPR are true. This organization really stands for proper data storing. In case your organization has databases with users’ data with external access and without any kind of protection, the company will be fined a large sum. This supervision is done to prevent the cases when everyone can see confidential data.
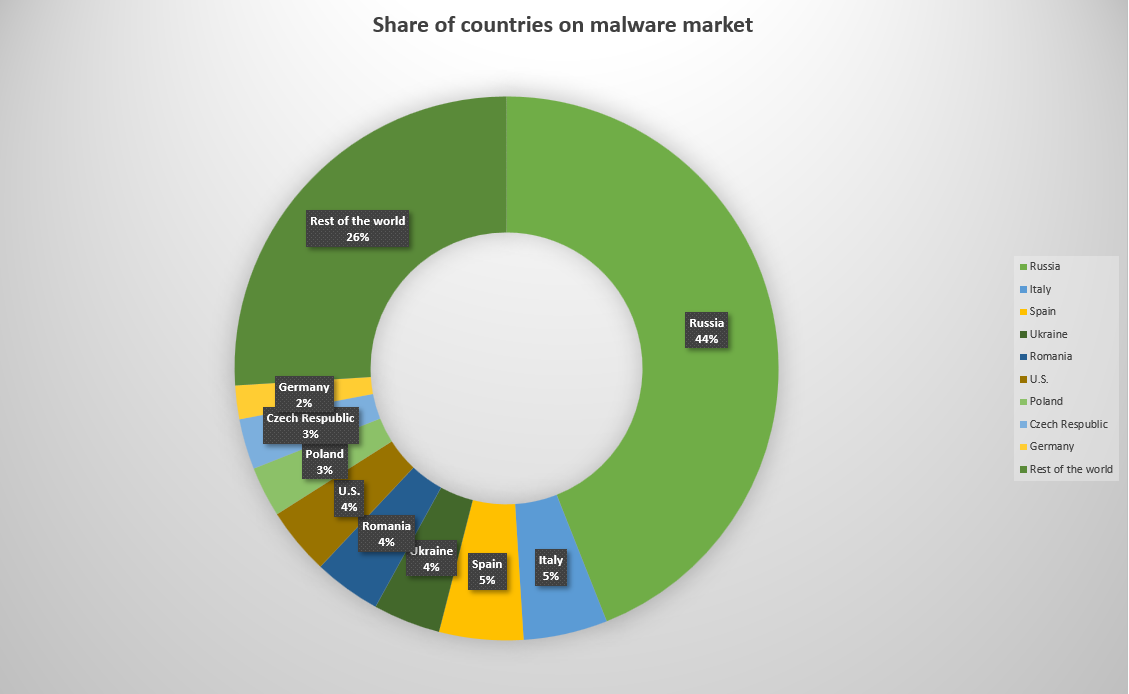
The pie chart shows the share of each country
Am I in danger?
You have nothing to worry about. Fraudsters can barely execute their threats and report the GDPR about violations of the rules. In fact, GDPR will likely ignore these claims, since you may start a controversial claim – stating that they were demanding a ransom payment (which can be classified as a bribe). 0.02 BTC that they ask to give your database back and do not report your case to GDPR are currently equal to ~$850-$900. This sum is close to ransom which is usually charged by ransomware for individual users.
Even more laughable is that almost all developers who work with databases know about GDPR rules. If not silly, they will use unsecured DBs only to store some sort of temporary projects, which still must be accessed from outside of the company’s network. And usually there is nothing valuable in these databases. Hence, any horror stories about the GDPR punishment are just an attempt to scare you.
What do I need to do?
If you had something confidential in those databases, and have no backup – sure, you have no choice but to pay the ransom. No one can guarantee that those fraudsters will not just run with your money, but you still have no alternatives. But you may be sure that you will not be charged by GDPR, so if you have a backup, just forget about that stupid case and continue working as usual. Of course, don’t forget to cipher your database next time.
The overall advice is to change the default connection port. Fraudsters rarely scan other ports for possible connection, so just changing the default networking settings will prevent their attempts. It is a pretty strange situation that the default settings in the majority of IDEs’ setups for database connections are insecure. Another useful advice is to set up your firewall1 – that thing can restrict the external connections. You can allow the connection to a certain DB only from your home IP address, and use it without any fears.
User Review
( vote)References
- Read about the Windows facilities for firewall setup.





