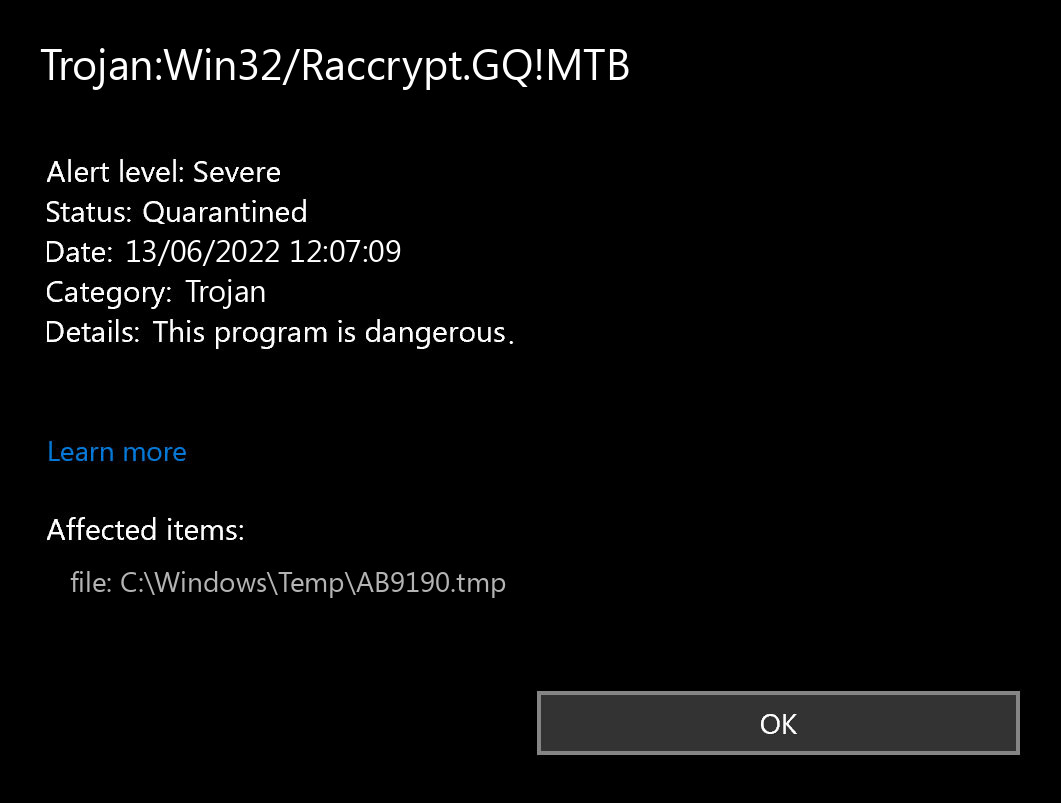
If you spectate the alert of Trojan:Win32/Raccrypt.GQ!MTB detection, it appears that your computer has a problem. All malicious programs are dangerous, with no deviations. Raccrypt is a malware that aims at exposing your PC to further threats. Most of of the modern virus variants are complex, and can inject various other viruses. Getting the Trojan:Win32/Raccrypt.GQ!MTB virus often means getting a malicious thing which can act like spyware or stealer, downloader, and a backdoor. Seeing this detection means that you must to perform the malware removal as fast as you can.
Any malware exists with the only target – gain money on you1. And the programmers of these things are not thinking about ethicality – they utilize all possible methods. Stealing your personal data, receiving the payments for the promotions you watch for them, utilizing your hardware to mine cryptocurrencies – that is not the complete list of what they do. Do you like to be a riding steed? That is a rhetorical question.
What does the pop-up with Trojan:Win32/Raccrypt.GQ!MTB detection mean?
The Trojan:Win32/Raccrypt.GQ!MTB detection you can see in the lower right side is shown to you by Microsoft Defender. That anti-malware application is pretty good at scanning, however, prone to be mainly unstable. It is defenseless to malware invasions, it has a glitchy user interface and problematic malware removal capabilities. For this reason, the pop-up which states about the Raccrypt is rather just a notification that Defender has actually spotted it. To remove it, you will likely need to make use of another anti-malware program.
The exact Trojan:Win32/Raccrypt.GQ!MTB virus is a really nasty thing. It sits inside of your system under the guise of something normal, or as a part of the program you downloaded at a forum. Therefore, it makes all possible steps to weaken your system. At the end of this “party”, it downloads other viruses – ones which are choosen by cybercriminals who manage this malware. Hence, it is impossible to predict the effects from Raccrypt actions. And the unpredictability is one of the most upleasant things when it comes to malware. That’s why it is better not to choose at all, and don’t give it even a single chance to complete its task.
Threat Summary:
| Name | Raccrypt Trojan |
| Detection | Trojan:Win32/Raccrypt.GQ!MTB |
| Details | Raccrypt tool that looks legitimate but can take control of your computer. |
| Fix Tool | See If Your System Has Been Affected by Raccrypt Trojan |
Technical details for Trojan:Win32/Raccrypt.GQ!MTB
Analysts uncovered the following alterations that Raccrypt Trojan does to the attacked system.
- Executable code extraction;
- Attempts to connect to a dead IP:Port (4 unique times);
- Creates RWX memory;
- HTTP traffic contains suspicious features which may be indicative of malware related traffic;
- Performs some HTTP requests;
- Unconventionial language used in binary resources: Serbian;
- The binary likely contains encrypted or compressed data.;
- Collects information to fingerprint the system;
- Anomalous binary characteristics – likely obfuscation in order to evade the detection by anti-malware programs.
Related domains:telete.in Trojan-Ransom.StopCrypt apps.identrust.com Trojan-Ransom.StopCrypt
Detection details
Is Trojan:Win32/Raccrypt.GQ!MTB dangerous?
| telete.in | Trojan-Ransom.StopCrypt |
| apps.identrust.com | Trojan-Ransom.StopCrypt |
As I have specified , non-harmful malware does not exist. And Trojan:Win32/Raccrypt.GQ!MTB is not an exclusion. This virus modifies the system configurations, modifies the Group Policies and registry. All of these components are critical for correct system operating, even in case when we are not talking about Windows safety. Therefore, the malware which Raccrypt contains, or which it will inject later, will try to get maximum revenue from you. Cyber burglars can steal your data, and then push it on the Darknet. Using adware and browser hijacker functionality, built in Trojan:Win32/Raccrypt.GQ!MTB malware, they can make revenue by showing you the ads. Each view gives them a penny, but 100 views per day = $1. 1000 victims who watch 100 banners per day – $1000. Easy math, but sad conclusions. It is a bad choice to be a donkey for crooks.
How did I get this virus?
It is difficult to line the sources of malware on your computer. Nowadays, things are mixed up, and distribution methods chosen by adware 5 years ago can be utilized by spyware nowadays. However, if we abstract from the exact distribution method and will think of why it has success, the explanation will be very basic – low level of cybersecurity understanding. Individuals click on ads on odd sites, click the pop-ups they receive in their browsers, call the “Microsoft tech support” thinking that the odd banner that says about malware is true. It is necessary to recognize what is legit – to avoid misunderstandings when trying to figure out a virus.
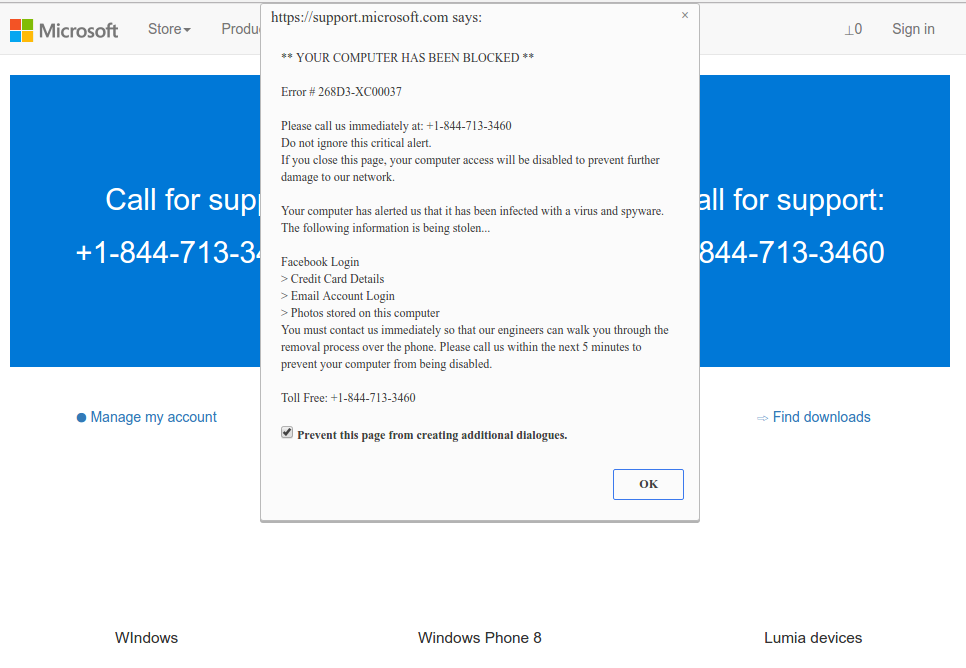
Microsoft Tech Support Scam
Nowadays, there are two of the most common ways of malware distribution – bait emails and also injection into a hacked program. While the first one is not so easy to evade – you need to know a lot to understand a fake – the second one is easy to address: just don’t utilize cracked applications. Torrent-trackers and various other sources of “totally free” applications (which are, in fact, paid, but with a disabled license checking) are just a giveaway point of malware. And Trojan:Win32/Raccrypt.GQ!MTB is simply among them.
How to remove the Trojan:Win32/Raccrypt.GQ!MTB from my PC?
Trojan:Win32/Raccrypt.GQ!MTB malware is extremely hard to erase by hand. It places its documents in numerous places throughout the disk, and can recover itself from one of the parts. Moreover, countless modifications in the windows registry, networking setups and also Group Policies are really hard to find and change to the initial. It is better to make use of a special program – exactly, an anti-malware tool. GridinSoft Anti-Malware will definitely fit the most ideal for virus removal reasons.
Why GridinSoft Anti-Malware? It is really lightweight and has its detection databases updated almost every hour. Furthermore, it does not have such problems and weakness as Microsoft Defender does. The combination of these aspects makes GridinSoft Anti-Malware ideal for clearing away malware of any form.
Remove the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of Raccrypt the default option is “Delete”. Press “Apply” to finish the malware removal.



User Review
( votes)References
- Read about malware types on GridinSoft Threat encyclopedia.