If you see the message reporting that the Trojan:Win32/Phoenix was identified on your PC, or in times when your computer works too slowly as well as give you a ton of headaches, you most definitely compose your mind to check it for Phoenix as well as clean it in a correct way. Right now I will tell to you exactly how to do it.
Trojan Phoenix will perform extensive checks to ensure it is not running in a virtual machine or analysis environment before gathering system information and sending it to an affiliate-supplied command and control server. If successful, Phoenix then attempts to disable Windows security services and begins extracting credentials from the mail, chat, or FTP clients, web browsers, and cryptocurrency wallets.
Phoenix will also use the SetWindowsHookExA function to enable keylogging on the affected system.
The majority of Phoenix are made use of to earn a profit on you. The criminals specify the range of unsafe programs to take your bank card information, online banking credentials, and other facts for fraudulent functions.
Threat Summary:
| Name | Phoenix Trojan |
| Detection | Trojan:Win32/Phoenix |
| Details | Phoenix tool that looks legitimate but can take control of your computer. |
| Fix Tool | See If Your System Has Been Affected by Phoenix Trojan |
Types of viruses that were well-spread 10 years ago are no longer the resource of the problem. Currently, the trouble is a lot more apparent in the locations of blackmail or spyware. The challenge of dealing with these issues needs different tools as well as new methods.
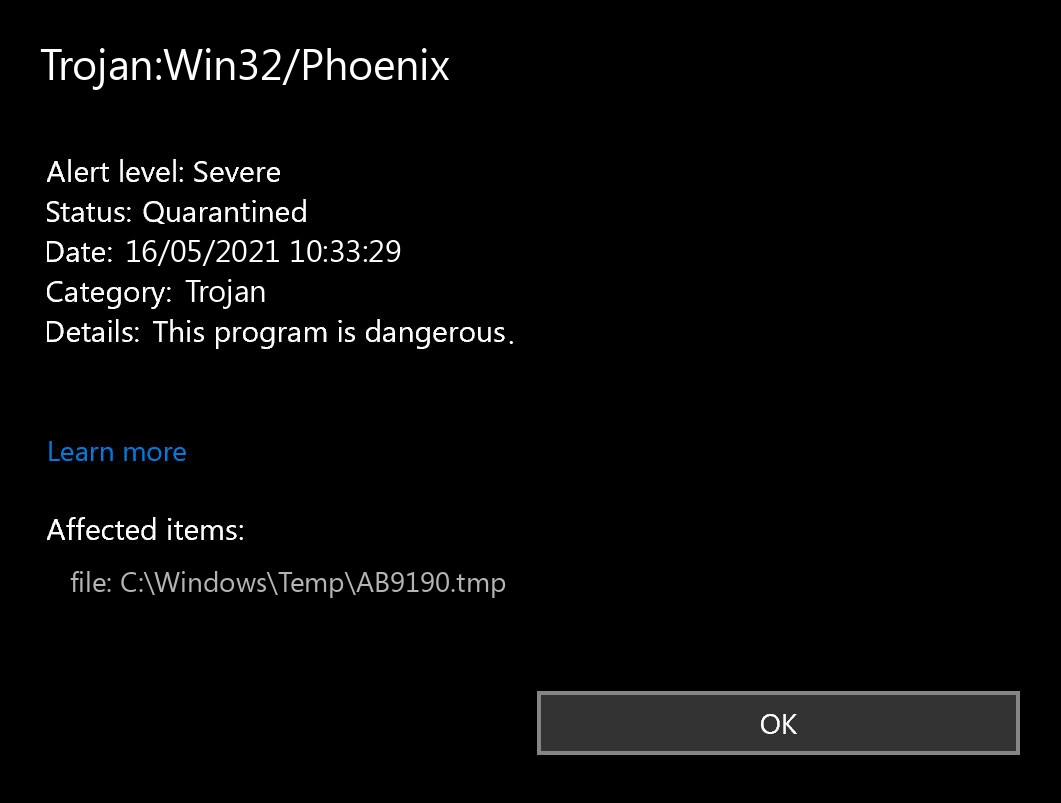
Does your antivirus regularly report about the “Phoenix”?
If you have seen a message indicating the “Trojan:Win32/Phoenix found”, after that, it’s an item of excellent information! The infection “Trojan:Win32/Phoenix” was detected and also, most likely, erased. Such messages do not mean that there was a really active Phoenix on your gadget. You might have merely downloaded and installed documents that contained Phoenix, so your anti-virus software immediately removed it before it was released and also created the troubles. Alternatively, the destructive manuscript on the contaminated internet site might have been discovered as well as avoided prior to triggering any type of troubles.
Simply put, the message “Trojan:Win32/Phoenix Found” during the typical use of your computer system does not mean that the Phoenix has completed its mission. If you see such a message after that it could be the evidence of you seeing the infected page or packing the destructive documents. Attempt to prevent it in the future, but don’t fret way too much. Trying out opening the antivirus program and checking the Trojan Phoenix discovery log file. This will give you more information regarding what the exact Phoenix was spotted and also what was specifically done by your anti-virus software program with it. Naturally, if you’re not confident sufficient, refer to the manual scan– at any rate, this will be valuable.
How to scan for malware, spyware, ransomware, adware, and other threats.
If your computer operates in an exceptionally sluggish method, the website opens in an unusual way, or if you see advertisements in places you’ve never expected, it’s possible that your computer got contaminated and also the infection is currently active. Spyware will track all your tasks or redirect your search or home pages to the areas you do not want to see. Adware may contaminate your web browser and even the entire Windows OS, whereas the ransomware will certainly try to obstruct your PC as well as demand a remarkable ransom amount for your own data.
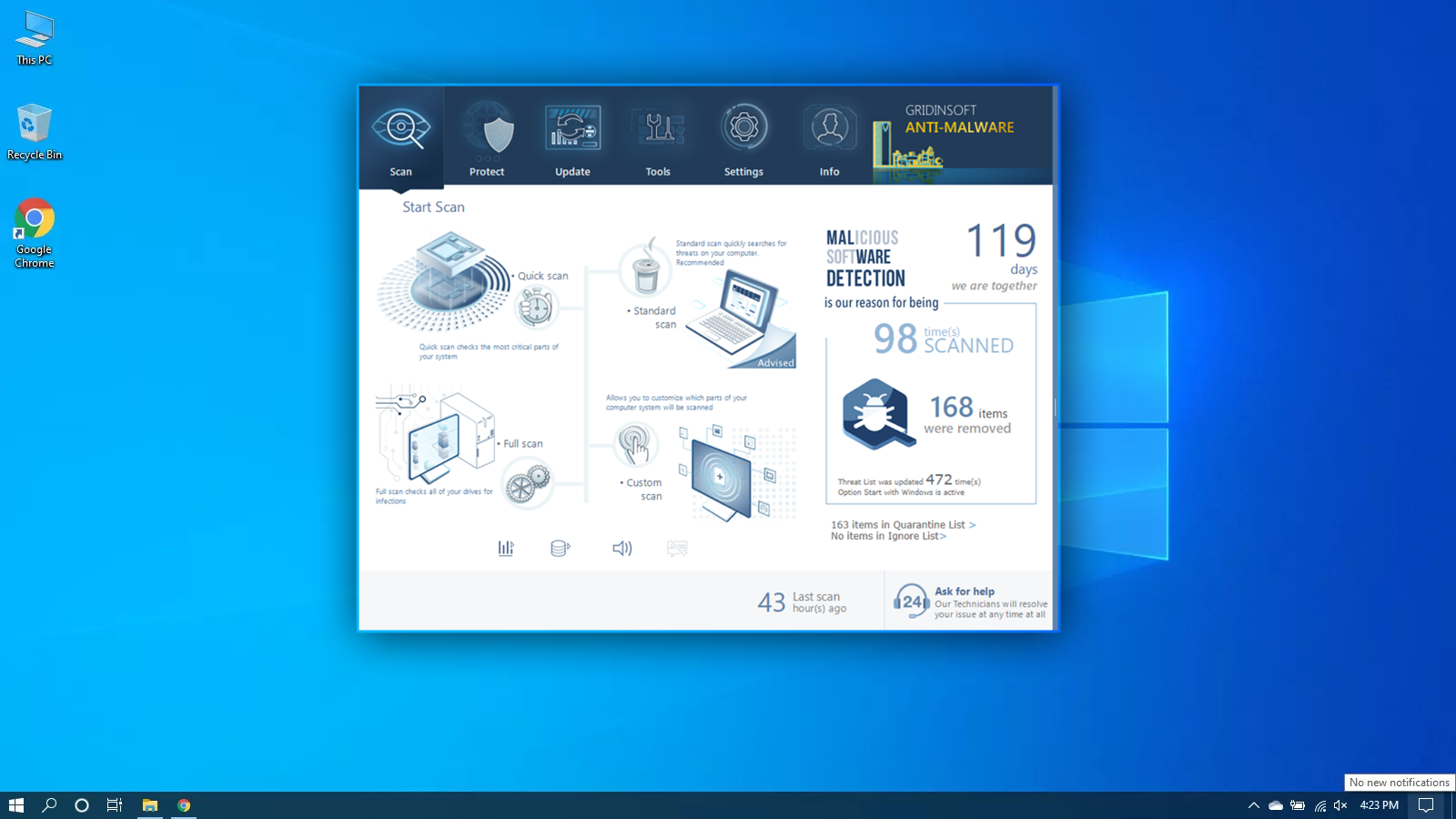
Irrespective of the type of the problem with your PC, the initial step is to scan it with Gridinsoft Anti-Malware. This is the most effective app to detect as well as cure your PC. Nonetheless, it’s not a simple antivirus software program. Its goal is to battle contemporary threats. Today it is the only application on the market that can just clean the PC from spyware and also various other viruses that aren’t also detected by routine antivirus software programs. Download, set up, and also run Gridinsoft Anti-Malware, then check your PC. It will lead you to the system cleaning process. You do not need to get a license to cleanse your PC, the first permit offers you 6 days of a completely complimentary test. However, if you want to protect on your own from long-term dangers, you probably require to take into consideration purchasing the certificate. By doing this we can ensure that your computer will no longer be infected with viruses.
How to scan your PC for Trojan:Win32/Phoenix?
To examine your computer for Phoenix as well as to remove all detected malware, you need an antivirus. The existing variations of Windows include Microsoft Defender — the built-in antivirus by Microsoft. Microsoft Defender is usually rather excellent, nevertheless, it’s not the only point you want to have. In our opinion, the best antivirus solution is to use Microsoft Defender in combo with Gridinsoft.
This way, you may obtain a complicated defense against the selection of malware. To look for viruses in Microsoft Defender, open it and also begin the fresh examination. It will extensively examine your computer for infections. And also, certainly, Microsoft Defender works in the background by default. The tandem of Microsoft Defender and also Gridinsoft will certainly set you free of most of the malware you may ever before encounter. On a regular basis arranged checks may likewise protect your system in the future.
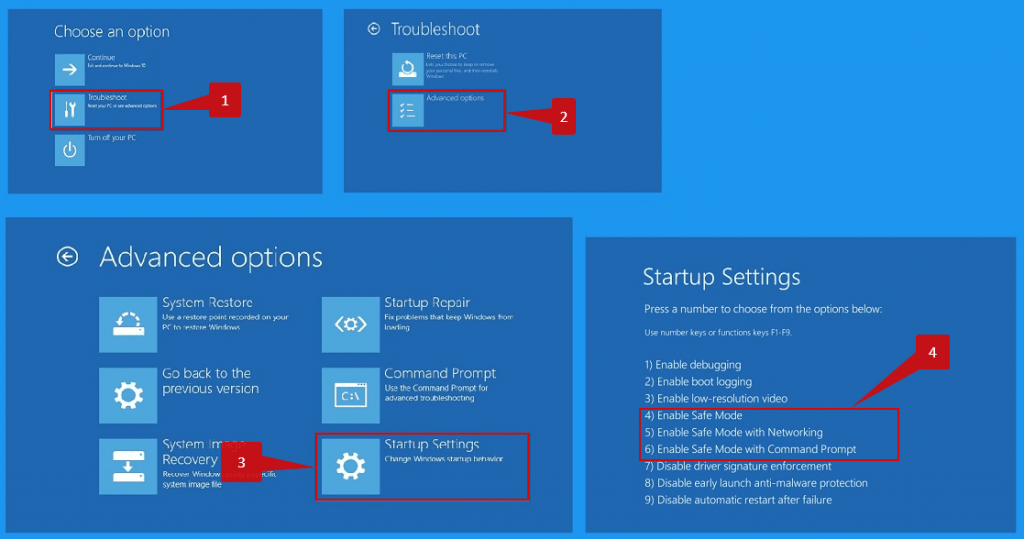
Use Safe Mode to fix the most complex Trojan:Win32/Phoenix issues.
If you have Trojan:Win32/Phoenix type that can barely be gotten rid of, you may require to take into consideration scanning for malware beyond the typical Windows functionality. For this purpose, you need to start Windows in Safe Mode, hence protecting against the system from loading auto-startup items, potentially consisting of malware. Start Microsoft Defender examination and after that scan with Gridinsoft in Safe Mode. This will certainly assist you to discover infections that can’t be tracked in the regular mode.
Use Gridinsoft to remove Phoenix and other junkware.
It’s not sufficient to simply use the antivirus for the safety and security of your PC. You require to have much more detailed antivirus software. Not all malware can be detected by typical antivirus scanners that mostly seek virus-type hazards. Your computer may teem with “trash”, for instance, toolbars, web browser plugins, questionable online search engines, bitcoin-miners, and various other kinds of unwanted programs used for making money on your inexperience. Be cautious while downloading and install programs online to stop your device from being full of unwanted toolbars and also various other junk information.
However, if your system has already obtained a specific unwanted application, you will certainly make your mind to delete it. Most of the antivirus programs are uncommitted concerning PUAs (potentially unwanted applications). To eliminate such programs, I recommend purchasing Gridinsoft Anti-Malware. If you use it regularly for scanning your PC, it will certainly aid you to remove malware that was missed by your antivirus software.
Frequently Asked Questions
There are many ways to tell if your Windows 10 computer has been infected. Some of the warning signs include:
- Computer is very slow.
- Applications take too long to start.
- Computer keeps crashing.
- Your friends receive spam messages from you on social media.
- You see a new extension that you did not install on your Chrome browser.
- Internet connection is slower than usual.
- Your computer fan starts up even when your computer is on idle.
- You are now seeing a lot of pop-up ads.
- You receive antivirus notifications.
Take note that the symptoms above could also arise from other technical reasons. However, just to be on the safe side, we suggest that you proactively check whether you do have malicious software on your computer. One way to do that is by running a malware scanner.
Most of the time, Microsoft Defender will neutralize threats before they ever become a problem. If this is the case, you can see past threat reports in the Windows Security app.
- Open Windows Settings. The easiest way is to click the start button and then the gear icon. Alternately, you can press the Windows key + i on your keyboard.
- Click on Update & Security
- From here, you can see if your PC has any updates available under the Windows Update tab. This is also where you will see definition updates for Windows Defender if they are available.
- Select Windows Security and then click the button at the top of the page labeled Open Windows Security.
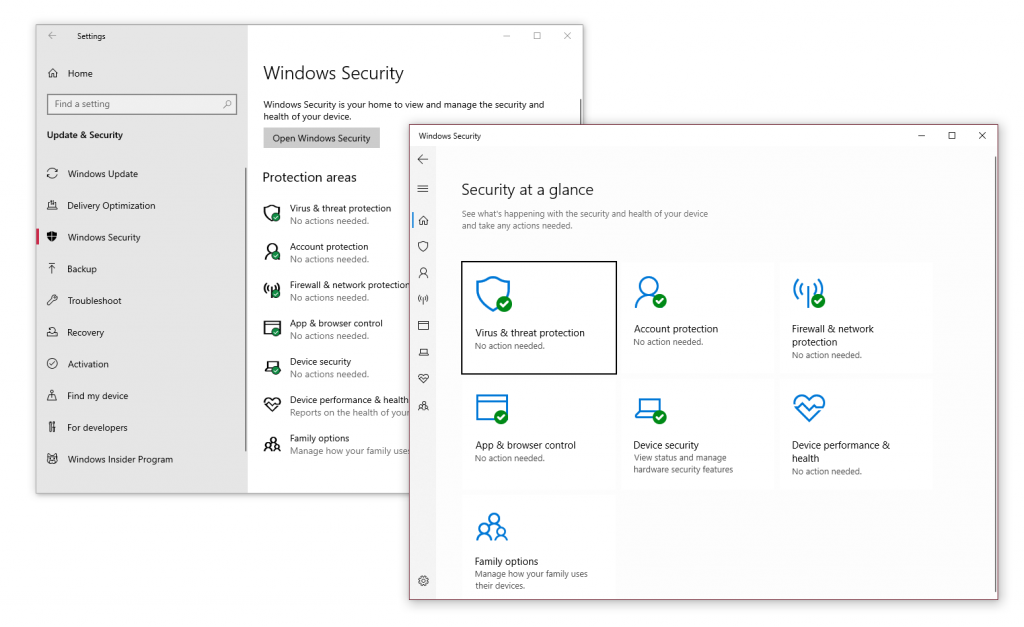
- Select Virus & threat protection.
- Select Scan options to get started.
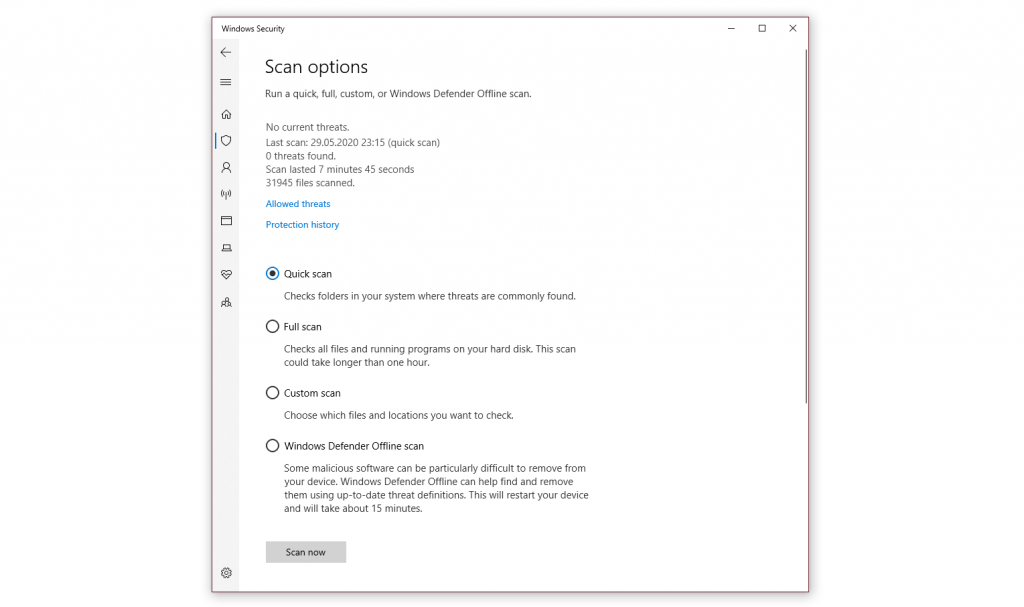
- Select the radio button (the small circle) next to Windows Defender Offline scan Keep in mind, this option will take around 15 minutes if not more and will require your PC to restart. Be sure to save any work before proceeding.
- Click Scan now
If you want to save some time or your start menu isn’t working correctly, you can use Windows key + R on your keyboard to open the Run dialog box and type “windowsdefender” and then pressing enter.
From the Virus & protection page, you can see some stats from recent scans, including the latest type of scan and if any threats were found. If there were threats, you can select the Protection history link to see recent activity.
If the guide doesn’t help you to remove Trojan:Win32/Phoenix infection, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments for getting help.
I need your help to share this article.
It is your turn to help other people. I have written this guide to help users like you. You can use buttons below to share this on your favorite social media Facebook, Twitter, or Reddit.
Wilbur WoodhamHow to Remove Trojan:Win32/Phoenix Malware

Name: Trojan:Win32/Phoenix
Description: If you have seen a message showing the “Trojan:Win32/Phoenix found”, then it’s an item of excellent information! The pc virus Phoenix was detected and, most likely, erased. Such messages do not mean that there was a truly active Phoenix on your gadget. You could have simply downloaded and install a data that contained Trojan:Win32/Phoenix, so Microsoft Defender automatically removed it before it was released and created the troubles. Conversely, the destructive script on the infected internet site can have been discovered as well as prevented prior to triggering any kind of issues.
Operating System: Windows
Application Category: Trojan