Information security researchers found that on YouTube arrived videos about the appearance of the mobile version of the game Valorant (and potential victims are offered to install it). Masking itself as Valorant, the Trojan spreads and enters Android devices, while hackers earn money by participating in affiliate programs.
Those who follow gaming news know that Valorant is still under development and is only available as part of the beta test (and only for computers running Windows). However, fraudulent videos are mounted in such a way that the game process on the screen of a mobile device looks believable.For greater credibility, such videos are accompanied by a detailed description, as well as avalanche of comments from users that allegedly successfully installed the game on their mobile devices. All reviews are obviously a fake.
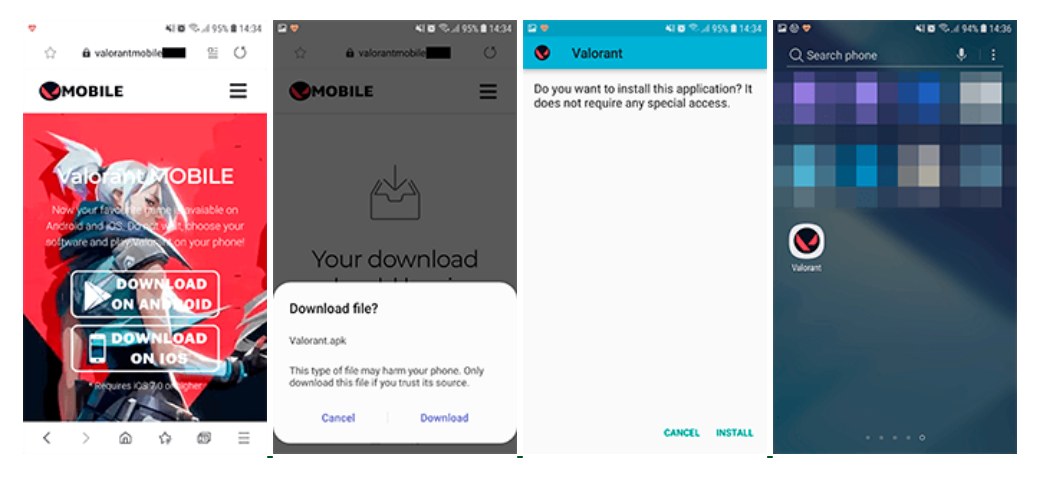
To download the game, users are invited to visit a site that looks similar to the official website of the Valorant project. There are two links on this resource, through which the game allegedly can be downloaded to a mobile device.”, – say the researchers.
If a site visitor tries to download a game for an iOS device, he will be redirected to the affiliate program site. If the download attempt is from an Android device, an APK file with the Android.FakeApp.176 Trojan is downloaded to it.
Since this file is not downloaded from the official Google Play catalog, on most modern devices it will be necessary to change the corresponding security settings to install it.
A malicious application mimics the game’s launch process, but then offers to “unlock” it by identifying the device. To do this, the user is required to download and install two other applications.
If consent to “unlock” is obtained, the trojan opens the site of the same affiliate service in the browser as in the case of iOS devices. After checking a number of parameters, this site redirects the user to the site of another affiliate program.
It presents the tasks that the visitor must complete in order to receive a reward. Experts concluded that the user finally is required to install and run the game from the Google Play catalog, as well as take part in an online survey.
In fact, such sites are typical services for making money on clicks, cheating on hit counts, advertising various software and cheating on the number of its installations, as well as monetizing online surveys and other marketing campaigns on the Internet”, – say the experts.
Some of these services really give the promised rewards to users, for example, when a users perform particular task, as to replenish the in-game balance or receive certain bonuses in games.
However, in the case of the Android.FakeApp.176 Trojan, users do not receive the promised game. The mobile version of Valorant simply does not exist, and the only task of fake is to download the partner service website, after what fraudsters will receive a reward for the victim.
Hackers often take advantage of gamers, for example the Syrc ransomware operators attacked Fortnite cheaters. Powerful hacking groups even attack game brands.