Exploit Definition: What is Exploit in Cyber Security?
An exploit is a code that takes advantage of a software vulnerability or security flaw.
Exploit is written either by security researchers as a proof-of-concept threat or by malicious actors for use in their operations. When used, exploits allow an intruder to access a network and gain elevated privileges remotely or move deeper into the network1.
They are usually embedded in malicious sources such as compromised sites, phishing emails in malicious attachments and often aren’t discovered until they are deployed.
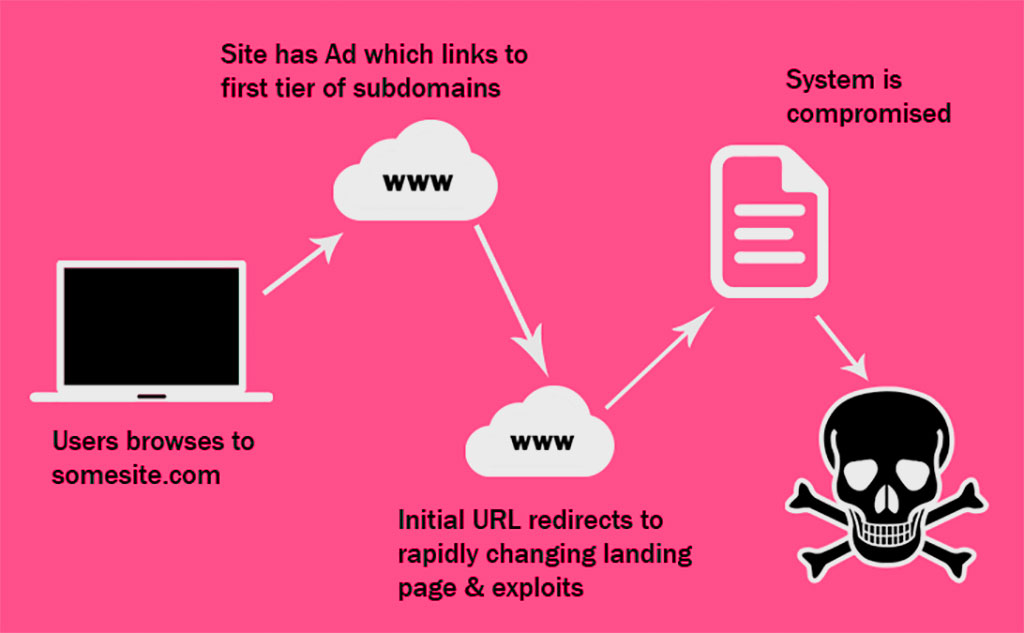
Example of attack with compromised site.
In some cases, exploits can be used as part of a multi-component attack. For example, instead of using a malicious file, the exploit may drop another malware, including Backdoor Trojans and Spyware, that can steal user information from the infected systems.
In addition, such kinds of malware have received a great deal of attention from the press, who may view them as a wake-up call to people. Perhaps the biggest shock is that many developers and users don’t take basic security precautions. The press has published news stories explaining the vulnerabilities and their exploits.
Example of Exploits
For 2020 and the first half of 2021, cybersecurity analysts and hackers detected 59 exploits in various products of this company. Adobe Experience Manager, Adobe Connect, and Adobe Creative cloud are among the most vulnerable programs.
- New exploit for the PlayStation 4 may be useful for the PS5
- Log4Shell: RCE 0-day exploit found in log4j 2, a popular Java logging package
- Cybersecurity researchers published an exploit for Windows that allows escalating privileges
- Trojan Source attack is dangerous for compilers of most programming languages
References
- Source: https://gridinsoft.com/exploits














