At the end of June 2020, cybersecurity specialists discovered the ThiefQuest ransomware targeting devices running macOS. Malware operators demanded money to get access back to the files. However, according to Trend Micro reports, the new version of ThiefQuest no longer encrypts victims’ files, but has different malicious functionality.
ThiefQuest was more than just a ransomware: the malware also installed a keylogger and reverse shell on infected machines to provide full control over compromised hosts.ThiefQuest also allows its operators to steal a variety of information from infected machines, including images, documents, databases, source code, encryption keys and cryptocurrency wallet data.
The ransomware is distributed with pirated software, for example, ThiefQuest was found in the Google Software Update, a pirated version of the popular DJ software Mixed In Key, and the macOS security tool Little Snitch”, – told Thomas Reed, Head of Mac & Mobile at Malwarebytes.
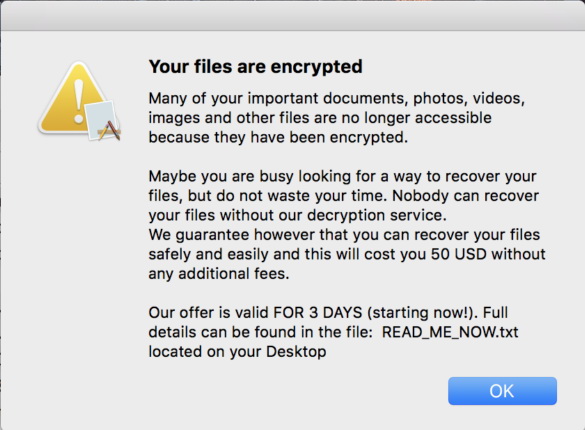
At the same time, it was noticed that the malware uses the same static bitcoin address for all victims, and the ransom note does not contain an email address or other contacts for communication.
In fact, because of this, the attackers could not in any way identify the victims who paid the ransom, and the victims could not contact the malware operators to decrypt the data. Because of this, the founder of Bleeping Computer Lawrence Abrams assumed that ThiefQuest was not an ordinary ransomware, but a wipe, a destructive malware that deliberately destroys files.
Fortunately for the victims, in early June 2020, SentinelOne specialists were able to create a free decryptor that malware victims could use to decrypt their files.
Now Trend Micro analysts conducted their own analysis of the malware and, comparing several versions, found that it continues to evolve and change.
It turned out that the latest versions of ThiefQuest no longer have file encryption functionality, and the malware no longer displays a ransom note to victims.
The first variants of ThiefQuest, which appeared in early June, were also more of a backdoor, and ransomware functionality appeared only in the second and third generations of the malware. In turn, the fourth version of malware, spotted in early July, is no longer ransomware”, – note the researchers.
Along with this, Trend Micro researchers discovered new functionality that allows malware to launch images and sound files using stock macOS applications. According to experts, this may indicate that the ThiefQuest developers are preparing to reintroduce the ransomware functionality into the code.
This is because previous versions of ThiefQuest displayed a ransom note in a modal window and used macOS speech function to read that note to the victim. These updates also may be used for similar purposes in the future.
Other changes that Trend Micro has found in newer ThiefQuest releases relate to the mode of reading payloads, compressing and decompressing files, generating of C&C IP addresses and changes to server files and subdomain names.