Security professionals have discovered a new EvilQuest ransomware that attacks macOS devices. EvilQuest is more than just an encryptor: the malware also installs a keylogger and reverse shell on infected machines for complete control over compromised hosts.
Firstly the new threat noticed Dinesh Devadoss, K7 Lab analyst, but, according to experts, EvilQuest has been active since at least beginning of June 2020.Currently, many new experts in the field of information security are studying the new malware. Among them are Patrick Wardle, Principal Investigator at Jamf Security and Founder of Objective-See; Head of Mac & Mobile at Malwarebytes, Thomas Reed, and Phil Stokes, MacOS security researcher at SentinelOne.
Reed and Stokes focused their efforts on finding an error or bug in the encryption scheme of the new ransomware, because a similar problem could be used to create a decryptor, and affected users would be able to recover their files without paying a ransom.
EvilQuest can be found in pirated software for macOS, posted on various torrent trackers and forums”, – Thomas Reed told ZDNet reporters.
Devadoss found EvilQuest in the Google Software Update, Wardle found EvilQuest samples in a pirated version of the popular DJ software Mixed In Key, and Reid spotted the malware in macOS Little Snitch.
At the same time, Reed is convinced that the ransomware is most likely distributed much wider and uses much more applications, not just the ones listed above.
Patrick Wardle has already published EvilQuest’s own technical analysis.
Malware is pretty simple and starts encrypting user files right after execution. As soon as the encryption is completed, the user sees a pop-up window where they are informed about data infection and encryption”, – writes Patrick Wardle.
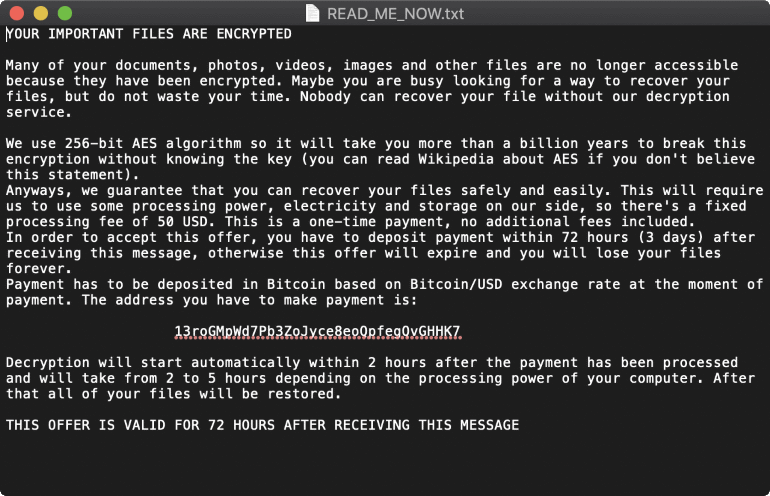
The victim also receives instructions: open a ransom note (a text file located on the desktop). Victims are asked to pay $50 ransom in cryptocurrency for three days (72 hours).
Interestingly, EvilQuest uses the same static bitcoin address for all victims, and attacker’s note does not contain an email address for communication. In fact, because of this, attackers cannot somehow identify the victims who paid the ransom, and the victims cannot contact malware operators to decrypt the data.
Because of this, the founder of Bleeping Computer Lawrence Abrams writes that all these features clearly indicate that EvilQuest is not an ordinary ransomware, but a wiper, a destructive malware that simply destroys files. Abrams is convinced that the ransomware is just a cover for the true purposes of criminals, namely the search and theft of files of certain types.
So, the ransomware encrypts any found files with the following extensions: .pdf, .doc, .jpg, .txt, .pages, .pem, .cer, .crt, .php, .py, .h, .m, .hpp, .cpp, .cs, .pl, .p, .p3, .html, .webarchive, .zip, .xsl, .xslx, .docx, .ppt, .pptx, .keynote, .js, .sqlite3, .wallet .dat.
Thomas Reed, who also presented his own analysis of EvilQuest, notes that the ransomware is trying to modify the files of the Google Chrome update mechanism and use them as a save vector on infected hosts. Apparently, the attackers did not take into account that when they start Chrome detects these changes and immediately replaces the files with clean copies.
Patrick Wardle writes that his 2016 RansomWhere tool is able to detect and stop the launch of EvilQuest. In turn, Thomas Reid notes that Malwarebytes for Mac has already been updated and now also detects and stops the new ransomware before it can do any damage.
It is worth noting that EvilQuest is only the third ransomware for macOS, known to information security experts. Before it, in 2016-2017, experts found only two threats of this kind – KeRanger and Patcher.
However, a small number of ransomware does not at all indicate good security of the system – let me remind you that recently Apple fixed 16 vulnerabilities in new macOS Catalina release.