Cybercriminals, as always, stay on top of the world news and monitor global trends. So, if earlier the attackers did not hesitate to use information about terrorist attacks and catastrophes for their own purposes, now they are actively exploiting the theme of the coronavirus pandemic. Users are lured to malicious sites and tricked into downloading a malware that is masked as a coronavirus distribution map.
Reason Cybersecurity analysts have warned that one of the new attacks is abusing the desire of users to obtain timely information about the coronavirus. This campaign is aimed at people who are looking for COVID-19 distribution maps.Reason Labs’ cybersecurity researcher, Shai Alfasi, found and analyzed this malware that had weaponized coronavirus map applications in order to steal credentials such as user names, passwords, credit card numbers and other sensitive information that is stored in the users’ browser. Attackers can use this information for many other operations as well, such as selling it on the deep web or for gaining access to bank accounts or social media”, — reports Reason Cybersecurity blog.
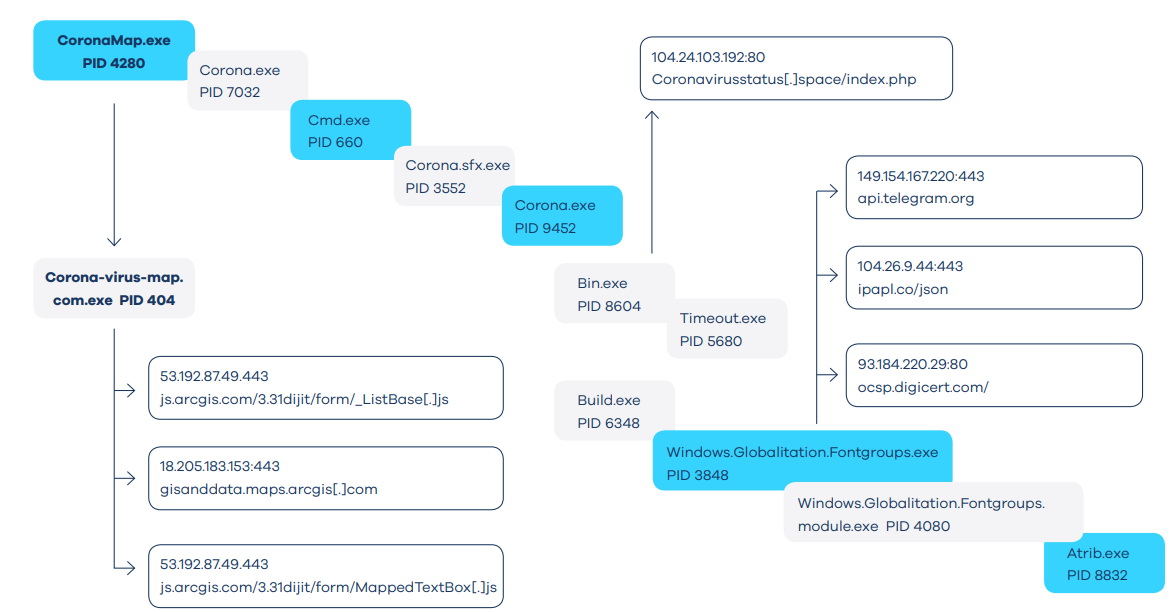
They are tricked into downloading and launching a malicious application that, at first glance, really displays a map downloaded from a legitimate site (the Johns Hopkins University actually monitors COVID-19), but the system is being compromised against this background.
The fact is that the malicious card, spreading under the guise of the file Corona-virus-Map.com.exe, contains the AZORult malware, designed to steal information.
Reference:
AZORult is an information stealer that was first discovered in 2016. It is used to steal browsing history, cookies, ID/passwords, cryptocurrency and more. It can also download additional malware onto infected machines. There is also a variant of the AZORult that creates a new, hidden administrator account on the infected machine in order to allow Remote Desktop Protocol (RDP) connections.
In turn, the ZDNet publication reports that government has not ignored the theme of the pandemic hack groups from China (Mustang Panda and Vicious Panda), North Korea (Kimsuky) and Russia (Hades group, associated with APT28).
Therefore, even in winter, coronavirus became a phishing bait and now spam containing malicious documents or links allegedly dedicated to COVID-19 is used to attack the Ministry of Health of Ukraine, South Korean officials and government organizations in Mongolia.
Additionally, Check Point experts said that more than 4,000 domains related to the theme of coronavirus have been registered and a considerable part of them are suspicious of cybercriminals.
As the coronavirus continues to spread and more apps and technologies are developed to monitor it, we will likely be seeing an increase in corona malware and corona malware variants well into the foreseeable future.