The software renewal scam is a very original form of online fraud that includes social engineering, scaring with false claims through email, phishing, and malware injection through remote access. In this post, you will see the detailed investigation of this fraud, and also the instruction on how to detect that somebody is trying to fool you.
Explaining the software renewal scam
These days, almost every user has many subscriptions with automatic software renewal. Every time the user is invoiced, he/she can find the corresponding email, where the sum is specified. The same sum is displayed as a transaction on the bank account. Hence, it is quite easy to track all the transactions you have, regardless of whether you approve every one or no. You usually know the coming payment size, so any increases in that sum will surely raise suspicion. At this moment, fraudsters are entering the game.
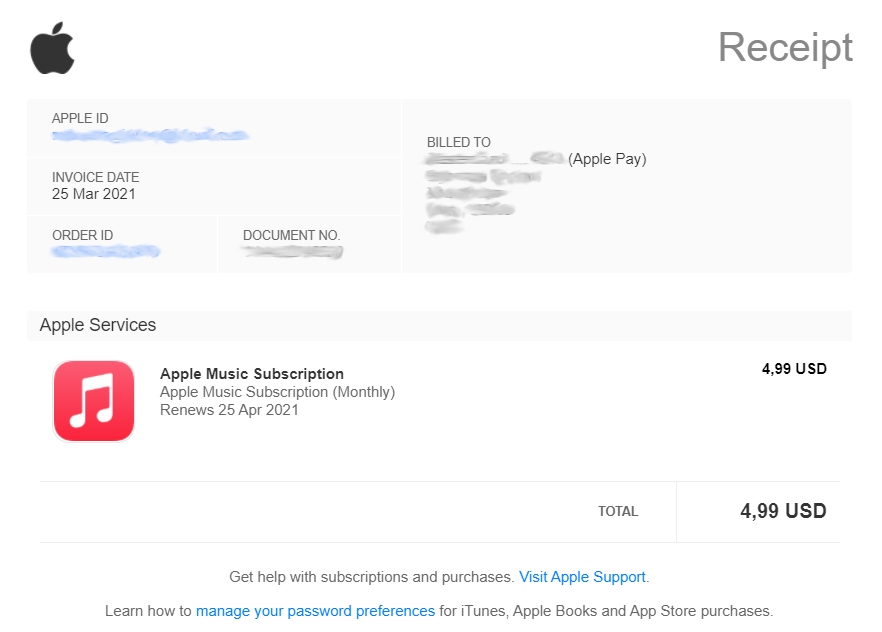
The example of real Apple invoice for Apple Music subscription
They compose the email, which looks like a legit notification about the software renewal. Experienced users who know a lot about how companies compose their invoice emails will definitely detect counterfeit. But people who ignore the appearance of the invoice will likely believe that message. It looks pretty sloppy, with strange fonts and, possibly, with several grammatical errors.
Here is the short review for this online fraud:
| Name | Software renewal scam |
| Appears as | Emails which contain fake invoices for software renewal |
| Distributes | Scareware, Potentially unwanted programs, Coin mining trojans |
| Way of distribution | Fake tech support call |
| Removal method | To remove possible virus infections, try to scan your PC |
Attracting the attention with a wrong invoice sum for the software renewal
The main thing which causes panic is the invoice sum. Fraudsters deliberately specify the amount of money that is up to 10 times bigger than the usual amount (250 dollars against $40 for an annual subscription). Of course, the indignant users will do everything to figure out the reasons and get their money back. And the crooks offer to call the number you can find at the bottom of the document. This number is supposed to be a support phone number, but, in fact, you will hear the same scammers on the phone.
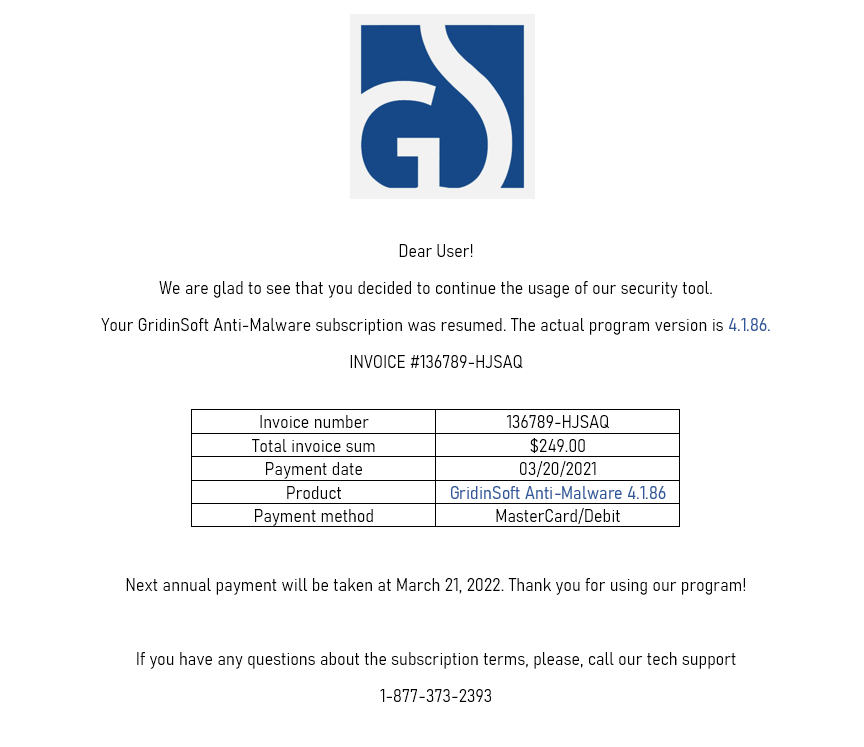
Fake software renewal invoice for GridinSoft Anti-Malware
Tricksters say that to perform the chargeback, they need to ensure that the program is completely deleted from your PC. The fact that you will be able to download it back and activate it with a key is not important, in their opinion. To ensure that you don’t have a program on your PC anymore, pseudo-support offers you to download a TeamViewer and give him remote access to your PC. However, they do not offer you to get this app from the official website, offering to use a third-party site.
These days, they use the zfix.tech page for this purpose. You will get a program in the bundle on that site, and the additional program installation is not displayed anywhere and cannot be stopped. This application is SupRemo – a remote administration tool that allows the admin to connect to the computer without any allowances from the owner of this PC. The majority of antivirus tools detect it as a potentially unwanted program, or riskware, since it is often used as a substitution for remote access trojan.
Your computer is hijacked
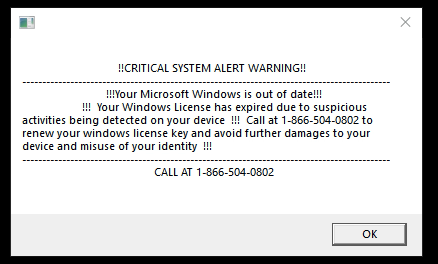
At this point, cybercriminals have full and non-disconnectable access to your computer. You may close the TeamViewer, but they will connect to your computer through the SupRemo and do their “job”. This “job” is to download a specific script from their internal server and add it to the Startup folder. That script is written on Visual Basic and, when added to the Startup, disables the launch of explorer.exe and several other processes responsible for the visual part of Windows. To initiate the launch of this script, crooks ask you to reboot the computer. As a result, you will see a black background without any usual elements, like a Taskbar and a scary window (CRITICAL SYSTEM ALERT WARNING) in the middle. The message in that window is the next:
Every time you click the “OK” button, a browser tab with a disruptive site will appear. “You won a prize” or “Take our gift for you as for 5 billion users” pages are very similar to phishing called Google membership rewards scam and Free Amazon GiftCard scam. Meanwhile, the scary window saying about the Windows activation will not disappear:
To get rid of all this madness, fraudsters offer you to call the number specified on the activation window. As you can guess, this one belongs to fraudsters, too. On that number, fraudsters will try to force you to pay the “activation fee”. Of course, no activation is needed. They try to force you to pay the ransom for cleaning your PC.
Manual removal of the scary window and system lock
It is very easy to get rid of this system locker. Since this is a Visual Basic script, you can stop it through the Task Manager and then remove it from the system. First, press the Ctrl+Shift+Esc combination to open the Task Manager. In it, you will see the running malicious script under the name of Microsoft Windows Based Script Host. Click on that task for one time and then click “End Task”:
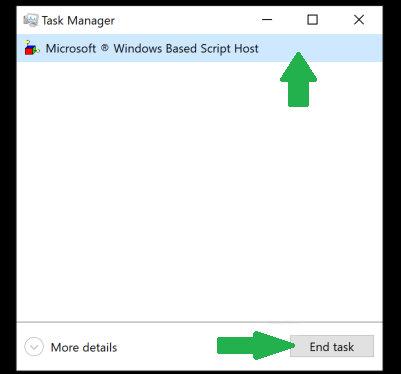
Now, the script is stopped. You need to remove it from the Startup folder and get your Windows interface back. Press the Win+R combination and type “explorer” in this window. Click “Ok” or press Enter on the keyboard to get your Windows interface back to the usual shape. When you have your system working properly, get rid of the WIN LICENSE.vbs file in the next location:
C:Users/%your_username%/AppData/Roaming/Microsoft/Windows/Start menu/Programs/Startup
Removing the software renewal virus with GridinSoft Anti-Malware
In some cases, the manual removal may be impossible. For that cases, anti-malware software is required. Microsoft Defender is efficient and easy-to-use tool, but a lot of users disable it because of its disadvantages. So, to avoid any possible troubles I can recommend you to remove the script with GridinSoft Anti-Malware1.
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of Ablotadom malware the default option is “Delete”. Press “Apply” to finish the malware removal.
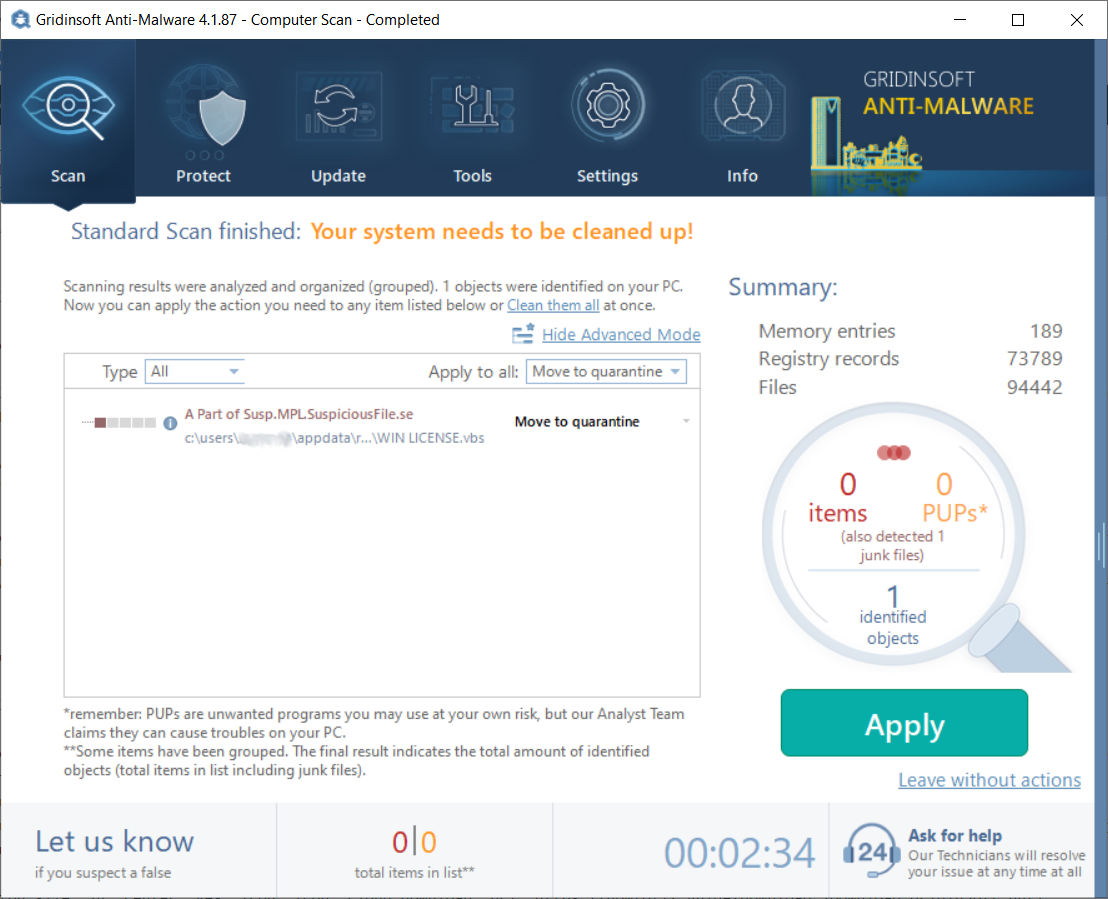

Who are those tricksters?
You may think that deanonymizing such actors requires hacker skills or FBI authority. However, you can do the same manipulations without any additional software or executive powers. You need to know where to search for this info. And the first place we need to check is the already mentioned site – zfix.tech, where we have got a dubious version of TeamViewer. A paid subscription for the resources with detailed info about the web domains allows getting information about the owner of this website. This person is called (at least, site data say so) Aman Deep Singh Sethi. He manages the email address [email protected], which was also used to register a wide range of other scam websites:
safebanking.biz
rightassists.com
2fix.tech
live-online-support.info
live-support.us
classifiedlookup.com
quickhelpdesk.in
network-security-alerts.com
help-live.us
cybersmart.xyz
cyberonservices.com
support247live.us
2fix.tech
cmdscan.info
rrlivehelp.com
cyberonservices.com
quickhelpdeskk.us
quick-help.us
quickhelpdeskk.us
amazondevicesupports.xyz
help365.us
cyberonservices.com
delvelogic.us
live-support.us
The associated phone number (i.e. specified as a contact number) +919810996265. That phone number is also used to register several other email addresses – [email protected], [email protected], and [email protected]. Crooks used these emails to purchase three additional domains, single per email. Those web pages are yahoomailhelplinenumber.com, hotmailhelplinenumber.com, and webroot-support-number.com, correspondingly. All these pages are used in the same online scams with a malicious script installation.
How can I detect that somebody tries to fool me?
Check your bank account. A large sum of money you can see in an invoice will surely be displayed as a transaction. If it isn’t, or you are not sure about the invoice you got, call the hotline of your bank. You can also check the number that is offered as a support phone. If this number is one of the lists which is used by fraudsters – ignore this message.
1-833-966-2310
1-954-800-4124
1-909-443-4478
1-877-373-2393
1-800-460-9661
1-325-221-2377
1-800-674-5706
1-855-966-6888
1-877-373-2393
1-866-504-0802
One more method, which may not be effective in some cases, is email address checking. Crooks are not able to register the email address which a real company already uses. Hence, you will get fake invoices from different email addresses than the original ones. If you do not receive the invoices regularly (for example, because of the annual payments), it may be hard to compare a new invoice with the older one. So, bank account checking will be the most effective (and the easiest) way to uncover the scam.
User Review
( votes)References
- Reasons why I recommend you to use GridinSoft Anti-Malware.


