Scammers impersonate the already defunct DarkSide hack group and are sending ransom letters to companies in the energy and food sectors, Trend Micro reports.
It is unclear why the imitators chose these particular industries, but it can be assumed that this is due to the fact that companies operating in these areas tend to pay money to the ransomware operators.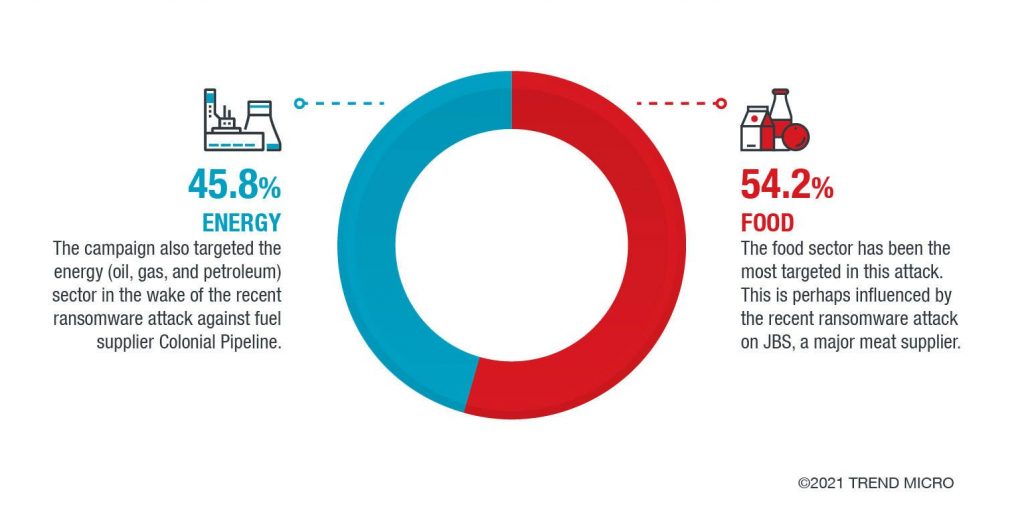
Let me remind you that the ransomware group DarkSide announced that it was stopping work last month, after the scandalous attack on the Colonial Pipeline company, which attracted too close attention of the authorities to hackers.
The group behind the DarkSide malware has been active since August 2020 and operated under the Ransomware as a Service (RaaS) scheme, actively advertising malware on the darknet and collaborating with other hack groups.
As a result, DarkSide was a classic “big game hunter”, that is, it attacked large corporate networks, encrypted data, and then demanded huge ransoms from the affected companies.
If the victims refused to pay, DarkSide members published the stolen data on their website on the darknet.
Trend Micro experts warn that a new ransomware campaign was discovered in June. In it, attackers impersonate DarkSide operators. Fraudulent emails that attackers send using contact forms on victims’ websites, for example, claim that the hackers have successfully compromised the target’s network and gained access to confidential information that will be “leaked” into the public domain if the victims do not pay a ransom 100 bitcoins (over $3 million).
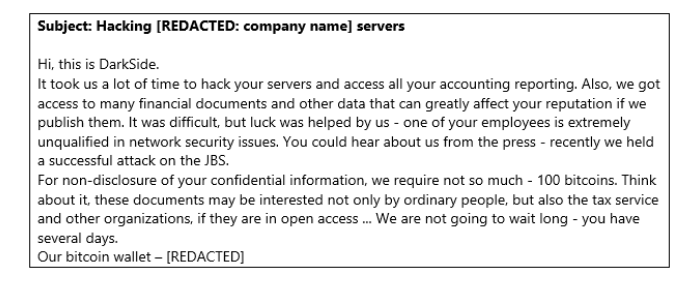
All letters from the attackers use the same bitcoin address: bc1qcwrl3yaj8pqevj5hw3363tycx2x6m4nkaaqd5e. No payments have been made to this address to date, and this will not change, given the enormous size of the ransom requested.
Trend Micro experts write that the emails they managed to study were sent from darkside@99email[.]xyz and Darkside @ solpatu[.]space, and the account at 99email.xyz is a disposable mailbox.
However, as we reported, Experts traced DarkSide group bitcoin wallets.
Pay attention to this: Pornographic Virus Alert from Microsoft
