Rundll32.exe process is an internal Windows process, which carries an important function. However, different malicious programs mimic this process to stay longer in the system. In this post, you will see the explanation of the task of the rundll32.exe process. Besides, I will show you the ways of recognizing that this process is a counterfeit.
Why this process is needed?
This system application is essential for the correct system functioning. The main task it carries is a correct execution of the programs, based on dynamic-link libraries (DLL). DLLs act as toolkits that allow the creation of the functions in the program. Every program needs its chain of dynamic-link libraries, and to make the calling of these DLLs easier, Windows offers such a function.
Besides these functions, rundll32 also allows calling different system functions manually, from the command prompt. For example, to call the Control Panel, you need to type the next command:
RUNDLL32 SHELL32.DLL,Control_RunDLL filename.CPL,@n,t
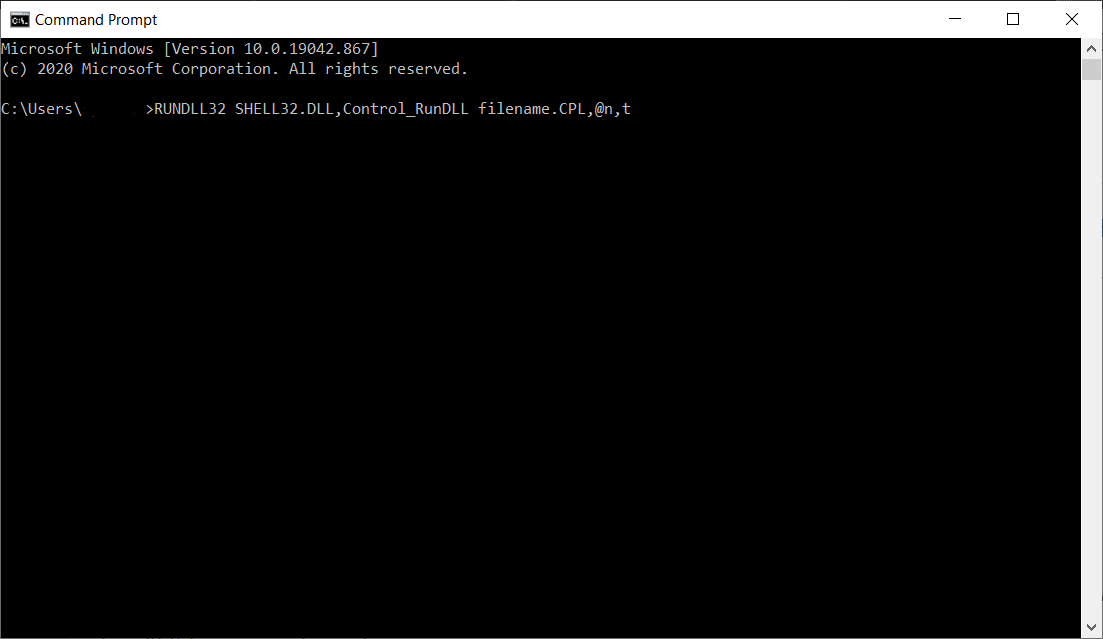
Where “filename” is the exact name of the Control Panel file, “n” is an applet of the CPL file, and “t” is the number of tabs the applet has (if it has several ones).
Such functions open a wide range of abilities for software developers, who don’t need to create a separate way of system function calling. Instead, they may make use of the embedded Windows mechanism.
Can I stop rundll32 exe?
You will not likely find this process in the classic Task Manager. It is hidden from the user without any clear reason. The only way to spectate the rundll32 process is to use another task management application from Microsoft – Process Explorer. It allows you to see a lot of different hidden processes, including the subject. Stopping this process will surely lead to various problems with the applications that require this service to be active. Moreover, that process consumes tiny amounts of CPU/RAM capacity, so there is no need to suspend it.
The times when Windows processes may be disabled to increase the system performance have passed long ago. When Windows XP was the last actual OS version, computers were quite weak, and their upgrade was expensive. Disabling several services could make your PC faster without any significant problems. Nowadays, such tricks can make things even worse.
How can I understand that rundll32 is a virus?
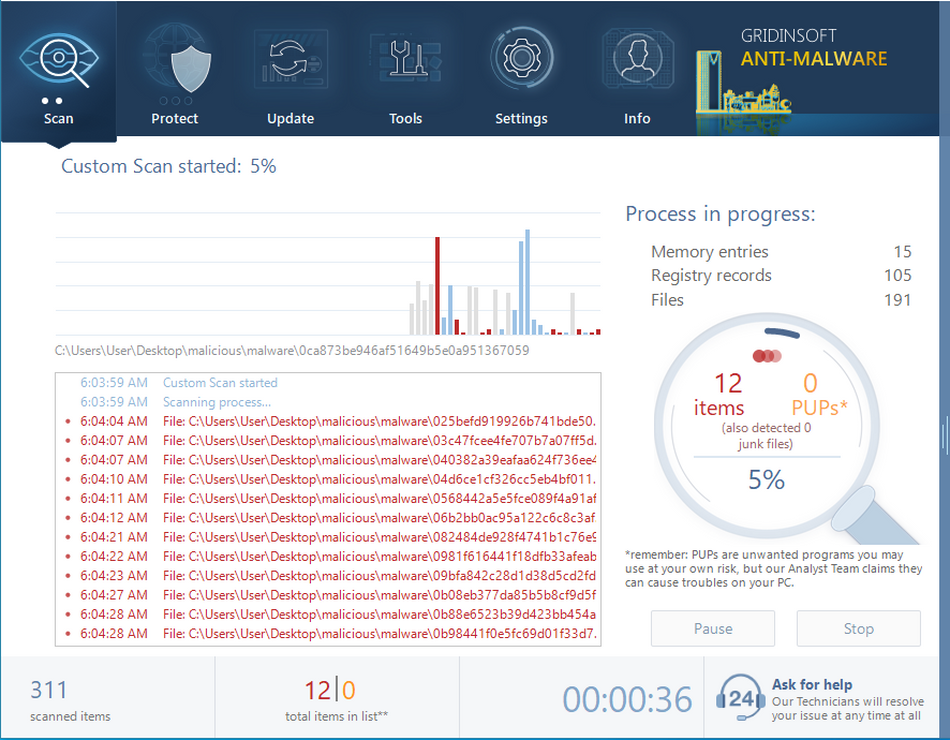
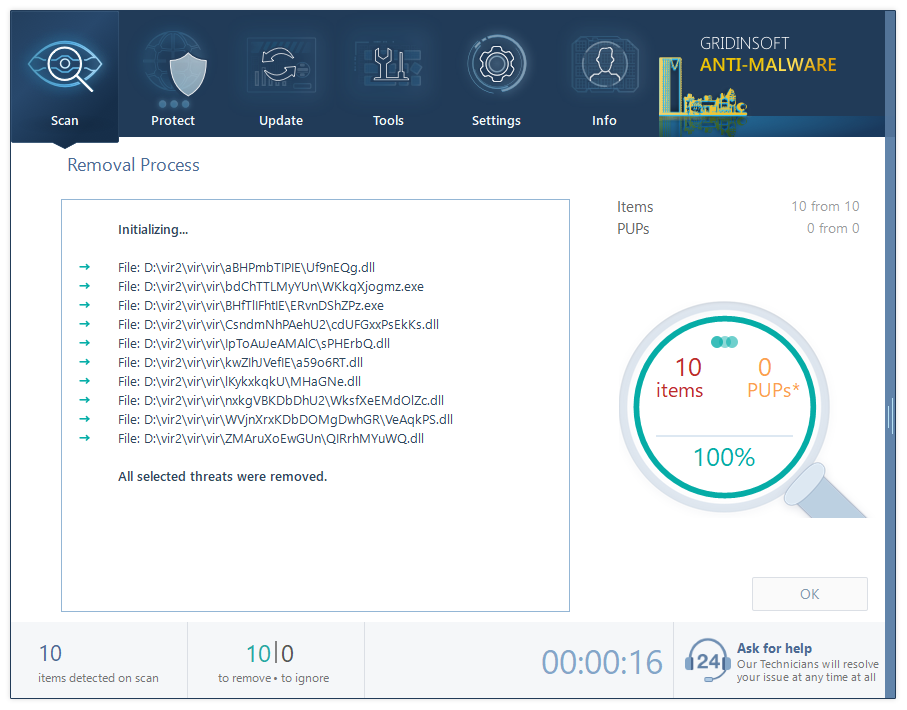
The perfect way to check if a malicious program launches the process is to open its file location. Find the rundll32.exe process in Process Explorer, and click it with the right mouse button. Choose the “Open file location” option, and you will see the folder where the .exe file is located. Everything is okay if the source file – rundll32.exe is located in C:/Windows/System32. Any other source file location means that you have malware on your computer. A wide range of viruses mimics this process, copying its name. To check your PC for viruses, I can offer you to use GridinSoft Anti-Malware1.
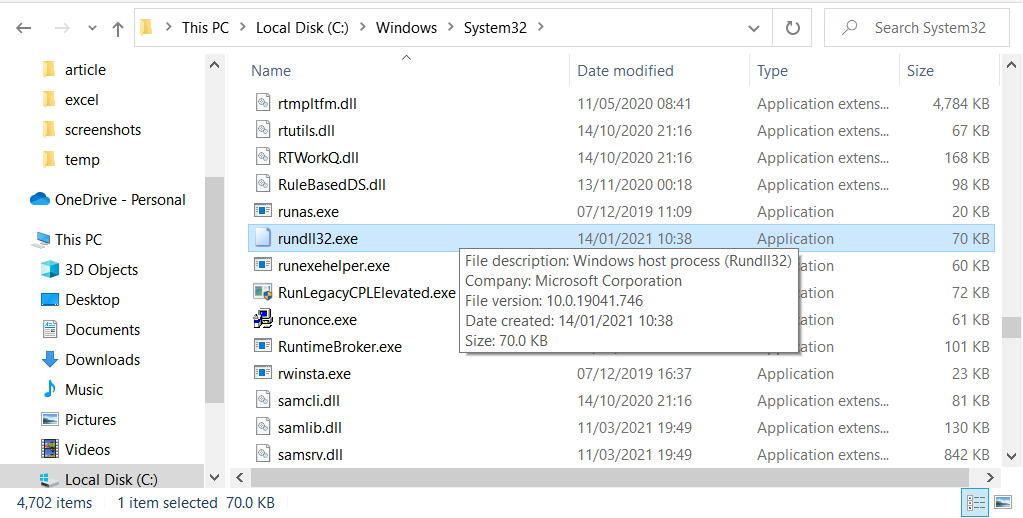
Proper location of rundll32.exe file
Removing the viruses with GridinSoft Anti-Malware

Frequently Asked Questions
No. If the process belongs to the legitimate system element, you will not be able to edit the system’s root directory, where it is stored, without permission for this action. And its deletion will undoubtedly lead to a system crash without the possibility of loading the system back because the crucial component is absent.
That process consumes nothing, so you will likely see no occasions when there is a need to make it less greedy with resources. However, it is expected to be a virus if you know that it takes more than 20-30% of your CPU and the same amount of RAM. Perform the guide I wrote above.
As was mentioned in the previous question, the CPU/RAM consumption of the actual process is deficient. So, the rundll32 process that uses a lot of hardware capacity is a virus. Another way to understand that this process belongs to a malicious program is its location inside the Process Explorer. System processes are listed in the corresponding thread so that process application among the user’s background processes is a sign of malware presence.
User Review
( votes)References
- Explanation why do I recommend you to use GridinSoft Anti-Malware.



