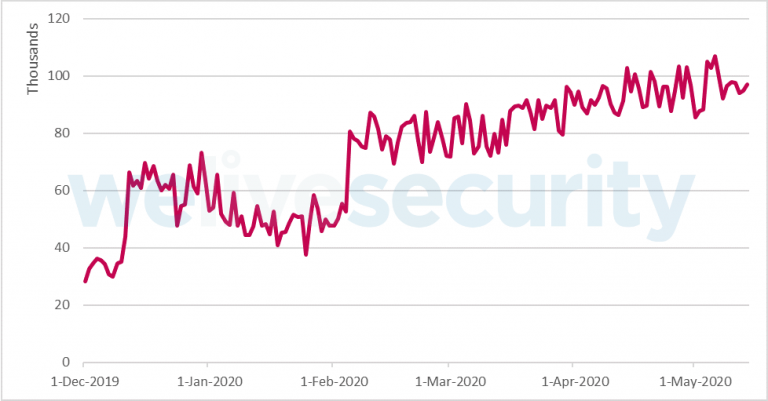
ESET announced an increase in brute force attacks on RDP. During the pandemic and the transition of companies to the home office mode, the number of attacks reached 100,000 per day.
Researchers explain that before the changes caused by the coronavirus pandemic, most organizations functioned under the control of the IT department. Now, many of them provide employees with remote access to the corporate network and sensitive data from home devices using RDP.As a result, appeared a security hole.
Staff often use weak passwords that are easy to pick up, which means the network is becoming more vulnerable to cybercriminals. The problem is compounded by the lack of additional protection in the form of two-factor authentication”, – write ESET analysts.
According to ESET, between December 2019 and February 2020, could be observed between 40,000 and 70,000 daily attacks. The upward trend emerged in February, when the number of brute force attacks reached 80,000.
Since then, the values have grown steadily and exceeded 100,000 in April and May, it is time when many countries with a large number of patients with COVID-19 were forced to implement quarantine measures, and the business massively switched to remote work.
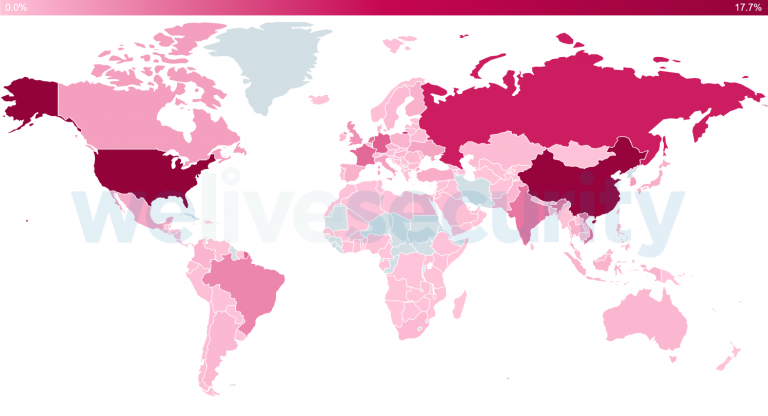
According to the telemetry collected by ESET, in January-May 2020, most of the blocked IP addresses from which the attacks were carried out were found in the USA, China, Russia, Germany and France. Russia ranked first in terms of the number of unique attacks detected by ESET.
By the way, Kaspersky Lab experts have already warned about the explosive growth of brute force attacks from this region more than a month ago.
Further in the ranking are Germany, Japan, Brazil and Hungary.
However, unauthorized access to the organization’s systems is only the first step, usually followed by more serious. RDP has become a popular vector of attacks, especially among hack groups that distribute ransomware.
Attackers often try to infiltrate a poorly protected network, gain administrator rights, disable or remove security solutions, and then run malware to encrypt sensitive corporate data. In addition, criminals can install a miner and even create a backdoor that will work even if unauthorized access to RDP is detected and terminated.
Recommendations for protection against ESET RDP attacks:
- Disable internet-facing RDP. If that is not possible, minimize the number of users allowed to connect directly to the organization’s servers over the internet.
- Require strong and complex passwords for all accounts that can be logged into via RDP.
- Use an additional layer of authentication (MFA / 2FA).Install a virtual private network (VPN) gateway to broker all RDP connections from outside your local network.
- At the perimeter firewall, disallow external connections to local machines on port 3389 (TCP/UDP) or any other RDP port.
- Protect your endpoint security software from tampering or uninstallation by password-protecting its settings.
- Isolate any insecure or outdated computers that need to be accessed from the internet using RDP and replace them as soon as possible.