With the spread of COVID-19, organizations all over the world transferred employees to remote mode of operation, which directly affected the cybersecurity of organizations and led to a change in the threat landscape. Kaspersky Lab analysts have noted an increase in the number of brute force attacks on RDP.
Along with the increased volume of corporate traffic, use of third-party services for data exchange and work of employees on home computers (in potentially insecure Wi-Fi networks), one more “headache” for IS specialists became increased number of people using remote access tools.One of the most popular application-level protocols that allows access to a workstation or server running Windows is Microsoft’s proprietary protocol, RDP.
During the quarantine, on the network arrived a large number of computers and servers that can be connected remotely. Currently experts are observing an increase in the activity of attackers, who want to take advantage of the current state of things and attack corporate resources, access to which (sometimes in a hurry) was opened for going to the remote job employees”, — say Kaspersky Lab analysts.
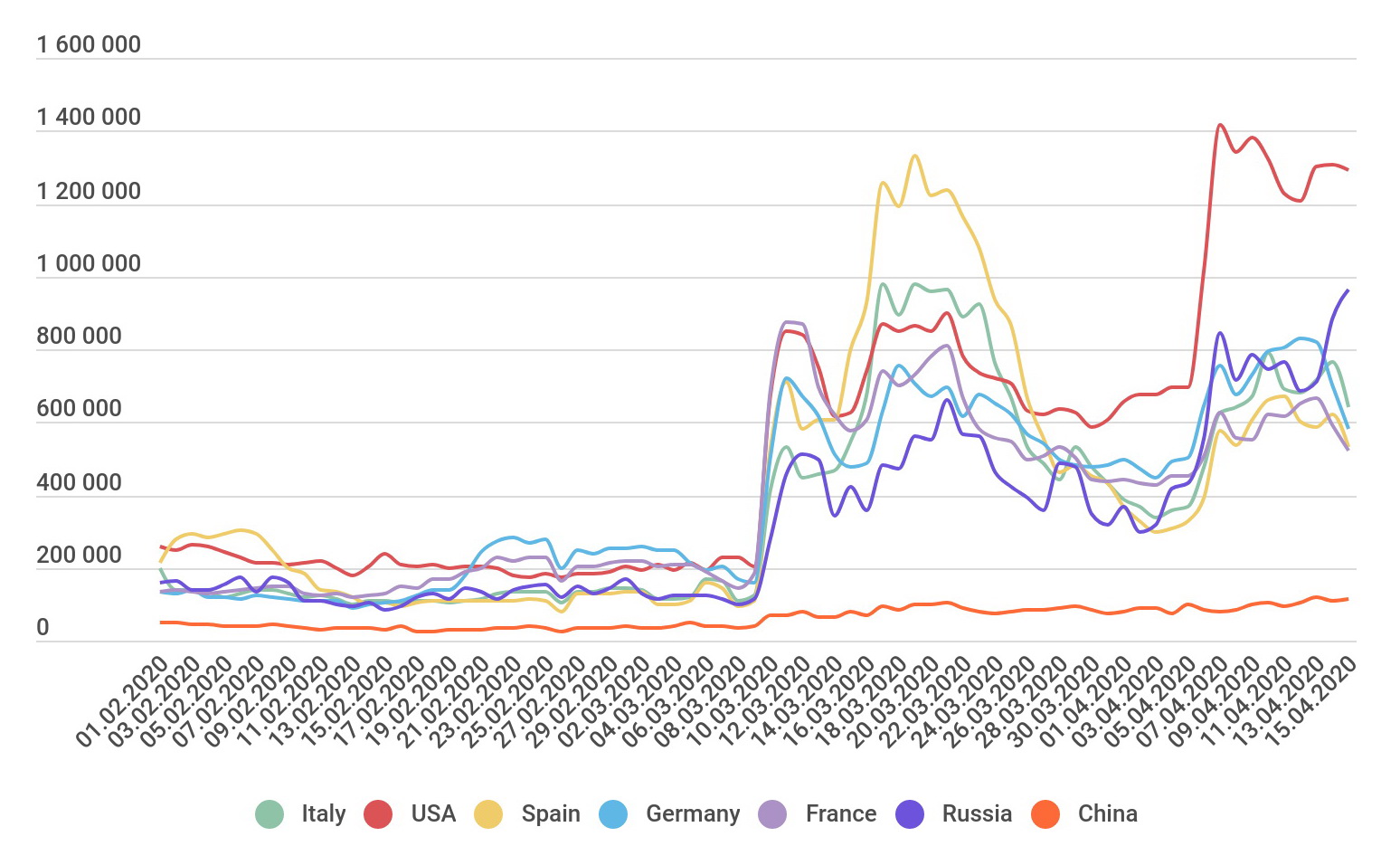
According to the company, since the beginning of March 2020 the number of brute-force attacks on RDP has jumped up and this picture is identical for almost the all the world:
Attacks of this type are attempts to select a username and password for RDP by systematically sorting through all possible options until the correct one is found. It can be used to search both combinations of characters and dictionary search of popular or compromised passwords. A successfully implemented attack allows an attacker to gain remote access to the host computer that it is targeting.
Attackers do not act pointwise, but “work on areas.” Apparently, after the ubiquitous transition of companies to work from home, the hackers came to the logical conclusion that the number of poorly configured RDP servers will increase, and in proportion to this, the number of attacks will increase”, – analysts say.
Even if you use other means of remote access instead of RDP, this does not mean at all that you can relax. Researchers recall that at the end of the last year, IS researchers investigated 37 vulnerabilities in various clients working with the VNC protocol.
Experts summarize that companies should closely monitor the programs used and timely update them on all corporate devices. Now this is not the easiest task for many, because due to the rapid transfer of employees to remote work, many had to allow employees to work or connect to company resources from their home PCs, which often do not meet corporate cybersecurity standards at all.