Earlier this week, information security specialist and creator of the ID-Ransomware service Michael Gillespie warned of the emergence of a new ransomware Qlocker, which attacks Qnap devices.
The creators of Qlocker use 7-zip and move files on Qnap devices to password protected archives. For example, files are locked at first, and the QNAP Resource Monitor displays multiple “7z” processes.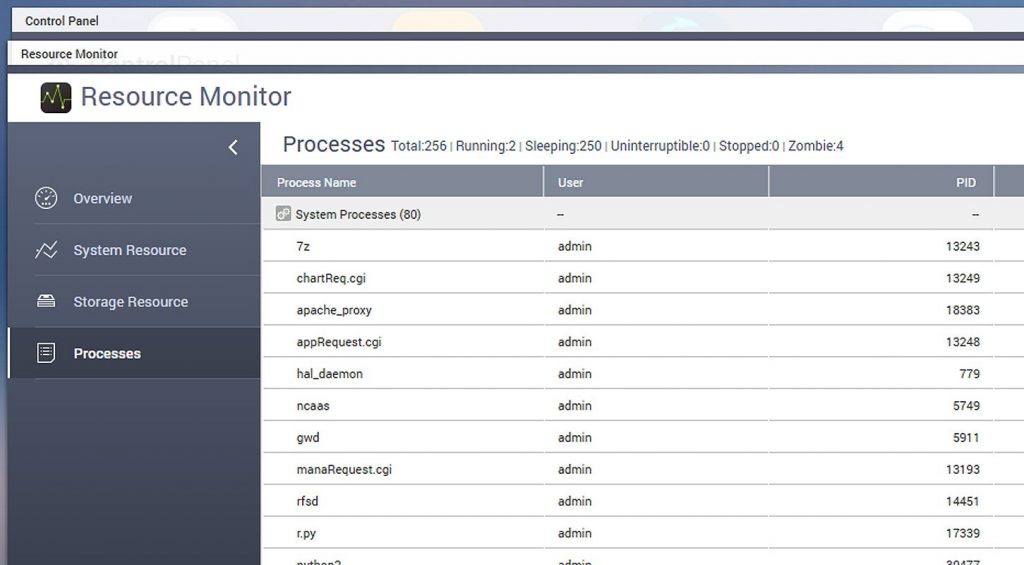
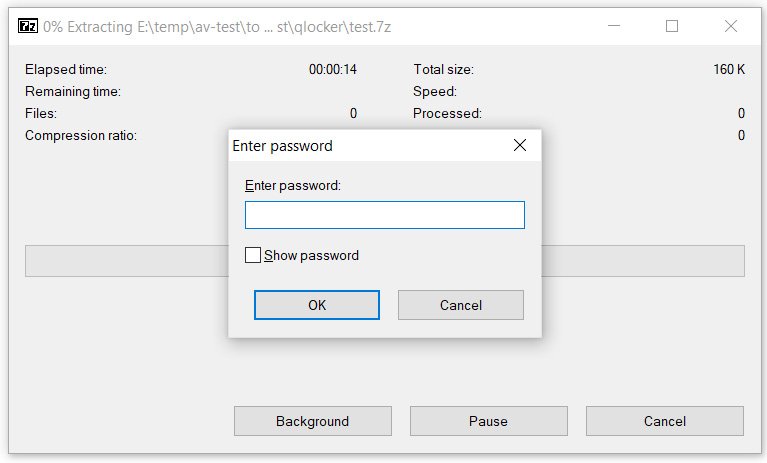
When the ransomware terminates its work, the files are placed in password-protected archives with the .7z extension. To unpack them, victims will need to enter a password known only to the attacker. The victims are left with a ransom note (file !!! READ_ME.txt), in the text of which you can find a unique client key that victims must enter to enter the Tor ransomware site.
Bleeping Computer writes that victims are encouraged to pay 0.01 bitcoin (roughly $557.74) to receive a password for their zipped files.
At the beginning of the week, information security specialist Jack Cable found a bug in malware that allowed users to save their files for free. The fact is that victims could ask for the Bitcoin transaction ID from another victim who has already paid the ransom and change it slightly. Such changed identifiers still worked on the attackers’ site, and victims received a password to decrypt their files.
An expert privately helped people to obtain passwords, and Emsisoft took steps to create a dedicated help system to assist people exploiting the vulnerability. But, unfortunately, soon the criminals also discovered a bug and made corrections to their code. This method no longer works. The researcher managed to help about 50 victims.
The Qnap developers have already published a security bulletin covering these attacks. It turned out that the criminals used a critical vulnerability that allowed them to infiltrate Qnap NAS devices. And the manufacturer fixed several vulnerabilities in its network devices at once.
The most serious issue was identified as CVE-2021-28799 and was found in the Hybrid Backup Sync (HBS) utility for disaster recovery and data backups. The bug consisted of hard-coded credentials (that is, essentially a backdoor account). The company stated that the bug has already been fixed in new versions of HBS, and recommends that customers update the software to the latest version as soon as possible:
- QTS 4.5.2: HBS 3 Hybrid Backup Sync 16.0.0415 and newer;
- QTS 4.3.6: HBS 3 Hybrid Backup Sync 3.0.210412 and newer;
- QuTS hero h4.5.1: HBS 3 Hybrid Backup Sync 16.0.0419 and newer;
- QuTScloud c4.5.1 ~ c4.5.4: HBS 3 Hybrid Backup Sync 16.0.0419 and newer.
Although it would seem that the CVE-2021-28799 issue was fixed only yesterday, the release notes for version 16.0.0415 say that the vulnerability was fixed almost a week ago, on April 16, 2021. Qnap representatives told reporters that the delay in disclosing information about the bug was required to prepare and release patches for QuTS hero and QuTScloud HBS.
Qnap also stressed that until recently, the PSIRT security team did not find any evidence of active exploitation of this vulnerability.
The vendor also fixed two other vulnerabilities related to command injection in HBS, as well as two more critical problems: the error of command injection in QTS and QuTS hero (CVE-2020-2509), as well as SQL injection in Multimedia Console and Media Streaming Add -On (CVE-2020-36195). These bugs also allowed attackers to gain full access to the NAS.
According to the developers, Qlocker uses some of these problems for its attacks and encryption of data on vulnerable devices.
It is also recommended to change the network port of the web interface from the default 8080 to any other, and use strong and unique passwords.
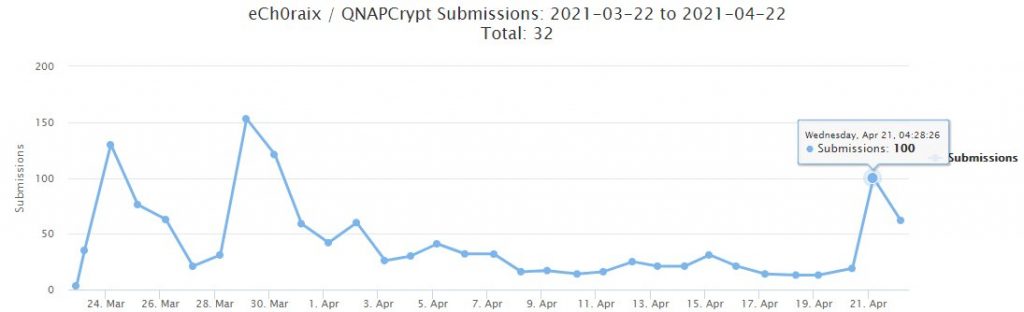
According to experts and the media, attacks by another previously known ransomware, eCh0raix, also targeting Qnap NAS, have become more frequent over the past week. For example, Michael Gillespie told The Record that the authors of eCh0raix could find and exploit the same errors as Qlocker operators, and this explains the recent spike in malware activity.
Let me remind you that I also wrote that QSnatch malware infects thousands of QNAP NAS devices, as well as that AgeLocker ransomware attacks Qnap devices and steals user data.