Last week, we warned that the new Qlocker ransomware is heavily targeting Qnap NAS users. This malware infiltrates devices thanks to recently fixed critical bugs, and then places all user files in password-protected archives with the extension .7z.
For decrypting the data, the attackers demand to pay 0.01 bitcoin (about $557 at the time of the start of the attacks), and this is quite a bit by modern standards, when hackers extort millions of dollars from companies.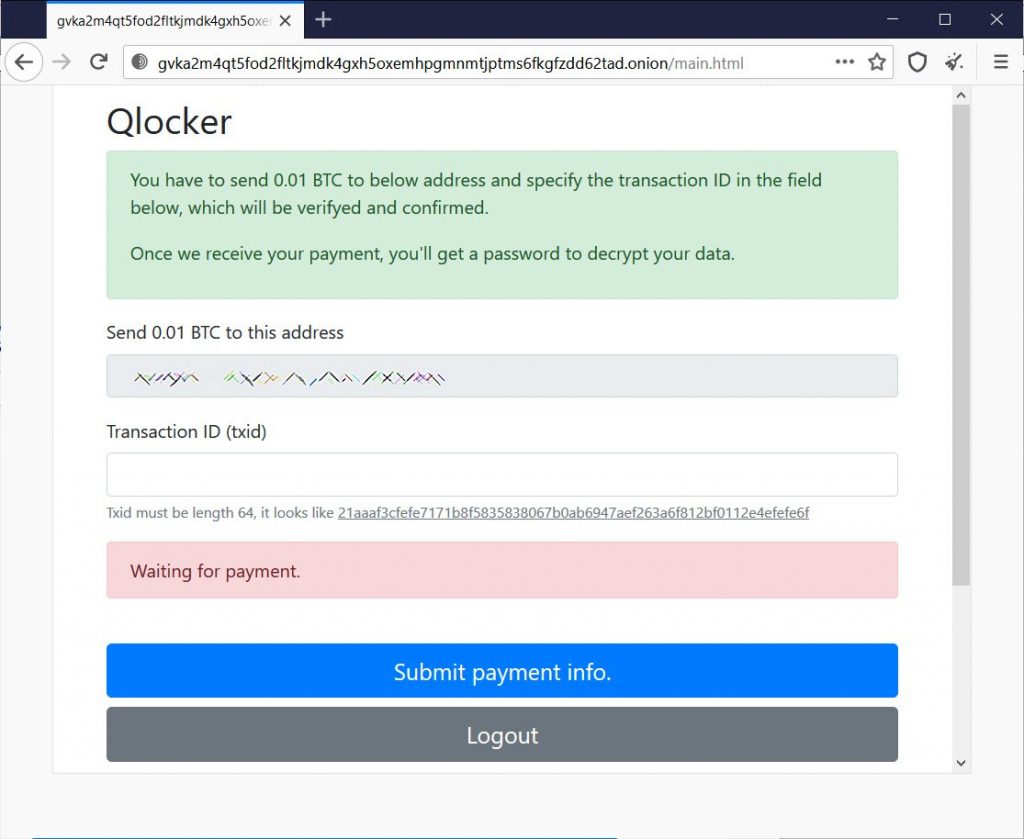
According to the Bleeping Computer, the attackers’ tactics paid off: in just five days, the hackers managed to hack and encrypt more than a thousand vulnerable devices. Since Qlocker uses a fixed set of bitcoin addresses through which ransoms of victims is passed, journalists were able to observe the payments.
Last week, information security specialist Jack Cable found a bug in malware that allowed users to save their files for free. The fact is that victims could ask for the Bitcoin transaction ID from another victim who has already paid the ransom and change it slightly. Such changed identifiers were still triggered on the attackers’ site, and victims received a password to decrypt their files.
This bug was quickly closed, but the researcher managed to collect a dozen bitcoin addresses of criminals. Another 10 were collected by the journalists themselves. A total of 5.25735623 bitcoins went through these wallets. This amount is equivalent to approximately US $ 281,000 at current exchange rates. Thus, approximately 525 victims have already paid the attackers.
Let me remind you that in order to protect against Qlocker, users need to update the Multimedia Console, Media Streaming Add-on and Hybrid Backup Sync on their devices as soon as possible, as well as download the latest version of Malware Remover and check the system for malware.
It is also recommended to change the default network port of the web interface from 8080 to any other port and use strong and unique passwords.
Let me remind you that we also talked about the fact that QSnatch malware infects thousands of QNAP NAS devices.

