What is NEMTY REVENUE 3.1?
NEMTY modifies your files by means of AES encrypting them and demanding the ransom to be paid allegedly to restore access to them.
NEMTY REVENUE 3.1 virus modifies all popular file types by means of adding the .NEMTY_XXXXXXX extension, thus making the data absolutely unavailable. The victims simply cannot open their important documents anymore. The ransomware also assigns its unique identification key, just like all previous representatives of the virus family. As soon the file is encrypted by the ransomware, it obtains a special new extension becoming the secondary one. The file virus also generates a ransom note NEMTY_XXXXXXX-DECRYPT.txt providing the users want instructions allegedly to restore the data.
Nemty Threat Summary
| Name | Nemty virus |
| Extension | .NEMTY_XXXXXXX |
| Type | Ransomware |
| Ransom note | NEMTY_XXXXXXX-DECRYPT.txt |
| Risks | Nemty ransomware operators publish data stolen from the victims |
| Emails | elzmflqxj@tutanota.de and elzmflqxj@tutanota.de |
| Detection | Troj/Nemty-A, Ransom:Win32/Nemty.ARJ!MTB, Ransom.Nemty, Trojan.Ransom.Nemty |
| Short Description | The ransomware modifies the documents on the attacked device through encryption and asks for the ransom to be paid by the victim supposedly to restore them. |
| Symptoms | The file virus encrypts the data by adding the NEMTY extension, also generating the one-of-a-kind identifier. |
| Distribution Method | Spam, Email attachments, Compromised legitimate downloads, Attacks exploiting weak or stolen RDP credentials1. |
| Fix Tool | See If Your System Has Been Affected by .nemty file virus |
NEMTY REVENUE 3.1
What Is It and How Did I Get It?
The Nemty ransomware is most commonly spread by means of a payload dropper. It runs the malicious script that eventually installs the file virus. The threat circulates actively on the web, considering the facts about the ransomware mentioned in the VirusTotal database. The Nemty ransomware may also promote its payload files through popular social networks and via file-sharing platforms. Alternatively, some free applications hosted on many popular resources may also be disguised as helpful tools, whereas they instead may lead to the malicious scripts that injected the ransomware. Your personal caution to prevent the Nemty virus attack matters a lot!
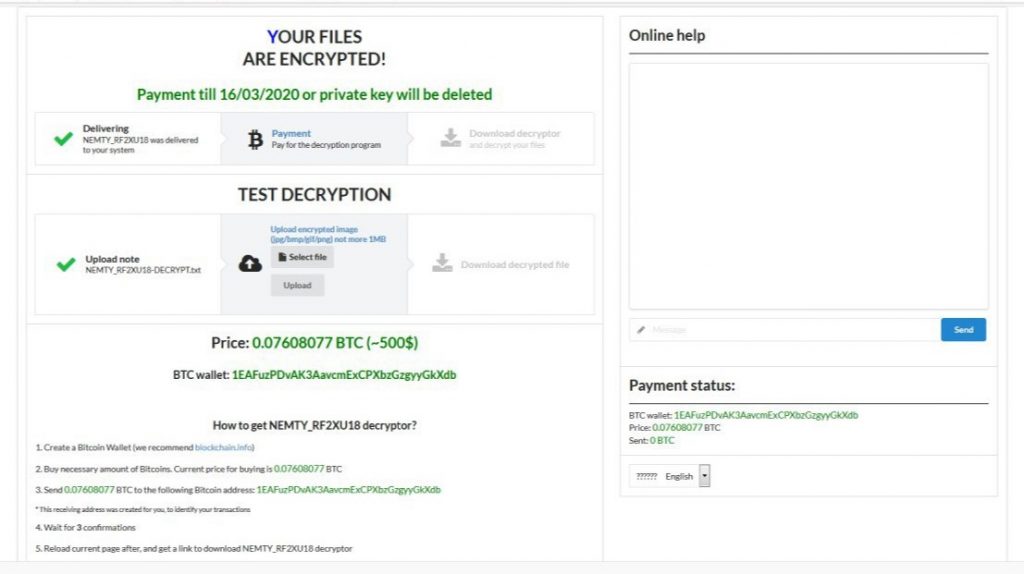
Nemty File Virus is a infection that encrypts your data and presents a frustrating ransomware notice. Below is the screenshot depicting the ransomware note:
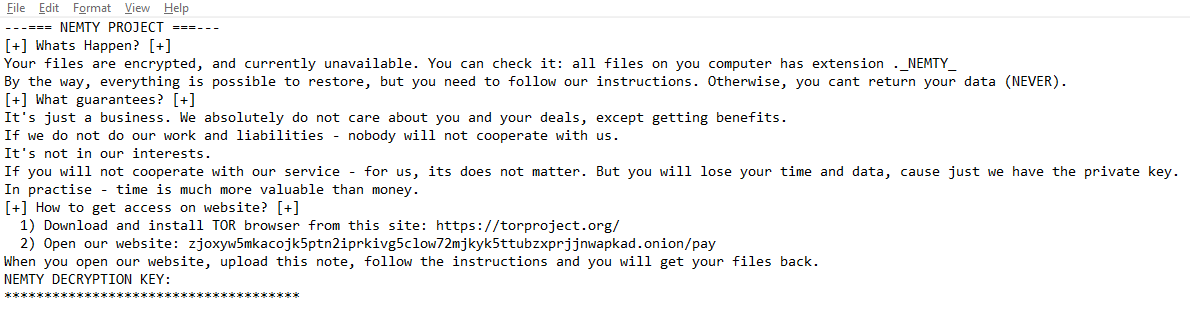
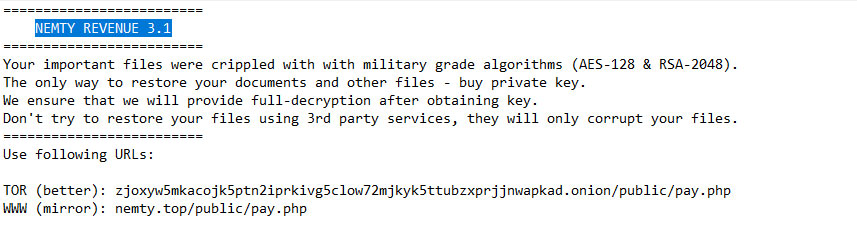
NEMETY Revenue 3.1 – Ransom Files
Quotation of the scary message
–> NEMTY REVENUE 3.1 <— Some (or maybe all) of your files got encrypted. We provide a decryption tool if you pay a ransom. Don’t worry, if we can’t help you with decrypting – other people won’t trust us. We provide test decryption, as proof that we can decrypt your data. You have 3 month to pay (after visiting the ransom page) until decryption key will be deleted from server. After 3 month no one, even our service can’t make decryptor. 1) Web-Browser a) Open your browser. b) Open this link: http://nemty.top/public/pay.php c) Upload this file. d) Follow the instructions. 2) Tor-Browser a) Download&Install Tor-Browser. b) Open Tor-Browser. c) Open this link: http://zjoxyw5mkacojk5ptn2iprkivg5clow72mjkyk5ttubzxprjjnwapkad.onion/public/pay.php d) Upload this file. e) Follow the instruction.
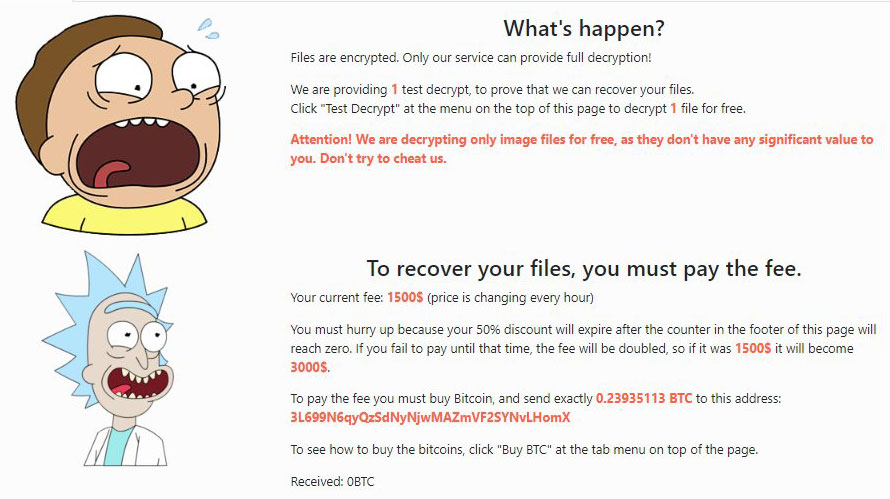
What’s happen? Files are encrypted. Only our service can provide full decryption! We are providing 1 test decrypt, to prove that we can recover your files. Click “Test Decrypt” at the menu on the top of this page to decrypt 1 file for free. Attention! We are decrypting only image files for free, as they don’t have any significant value to you. Don’t try to cheat us. To recover your files, you must pay the fee. Your current fee: 750$ (price is changing every hour) You must hurry up because your 50% discount will expire after the counter in the footer of this page will reach zero. If you fail to pay until that time, the fee will be doubled, so if it was 750$ it will become 1500$. To pay the fee you must buy Bitcoin, and send exactly 0.09602912 BTC to this address: 3EKmodX3aehnS4YRE8QoqSZ1ftYU3avo89 To see how to buy the bitcoins, click “Buy BTC” at the tab menu on top of the page. Received: 0BTC
Used URL:
- api.db-ip.com/v2/free/54.39.189.18/countryName
- www.myexternalip.com
- ghs.googlehosted.com
List of countries in NEMTY PROJECT ransomware's whitelist:
- Armenia
- Azerbaijan
- Belarus
- Kazakhstan
- Kyrgyzstan
- Moldova
- Russia
- Tajikistan
- Ukraine
Execute this commands:
cmd.exe /c vssadmin resize shadowstorage /for=C: /on=C: /maxsize=401MB cmd.exe /c vssadmin resize shadowstorage /for=C: /on=C: /maxsize=unbounded cmd.exe /c taskkill /f /im sql.* cmd.exe /c taskkill /f /im winword.* cmd.exe /c taskkill /f /im wordpad.* cmd.exe /c taskkill /f /im outlook.* cmd.exe /c taskkill /f /im thunderbird.* cmd.exe /c taskkill /f /im oracle.* cmd.exe /c taskkill /f /im excel.* cmd.exe /c taskkill /f /im onenote.* cmd.exe /c taskkill /f /im virtualboxvm.*
Kill processes:
vssadmin resize shadowstorage /for=C: /on=C: /maxsize=401MB C:\Windows\System32\cmd.exe /c vssadmin resize shadowstorage /for=C: /on=C: /maxsize=401MB vssadmin resize shadowstorage /for=C: /on=C: /maxsize=unbounded C:\Windows\System32\cmd.exe /c vssadmin resize shadowstorage /for=C: /on=C: /maxsize=unbounded taskkill /f /im sql.* C:\Windows\System32\cmd.exe /c taskkill /f /im sql.* taskkill /f /im winword.* C:\Windows\System32\cmd.exe /c taskkill /f /im winword.* taskkill /f /im wordpad.* C:\Windows\System32\cmd.exe /c taskkill /f /im wordpad.* C:\Windows\System32\cmd.exe /c taskkill /f /im outlook.* taskkill /f /im outlook.* taskkill /f /im thunderbird.* C:\Windows\System32\cmd.exe /c taskkill /f /im thunderbird.* C:\Windows\System32\cmd.exe /c taskkill /f /im oracle.* taskkill /f /im oracle.* C:\Windows\System32\cmd.exe /c taskkill /f /im excel.* taskkill /f /im excel.*
The image below gives a clear vision of how the files with NEMTY extension look like:
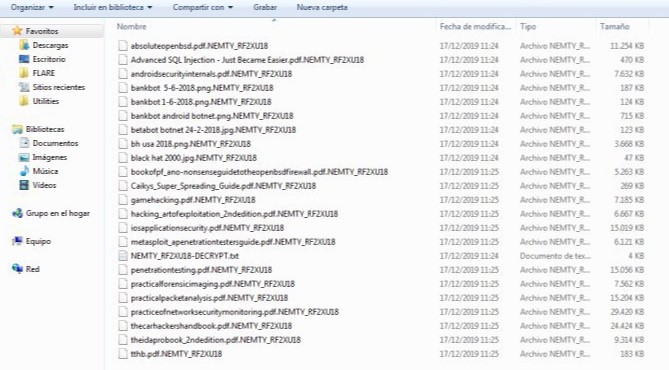
NEMTY PROJECT screenshot of delivering a ransom-demand message:
<>
Remove Nemty Virus
Reasons why I would recommend GridinSoft2
The is an excellent way to deal with recognizing and removing threats - using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes3.
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the install-antimalware-fix.exe file to install GridinSoft Anti-Malware on your PC.
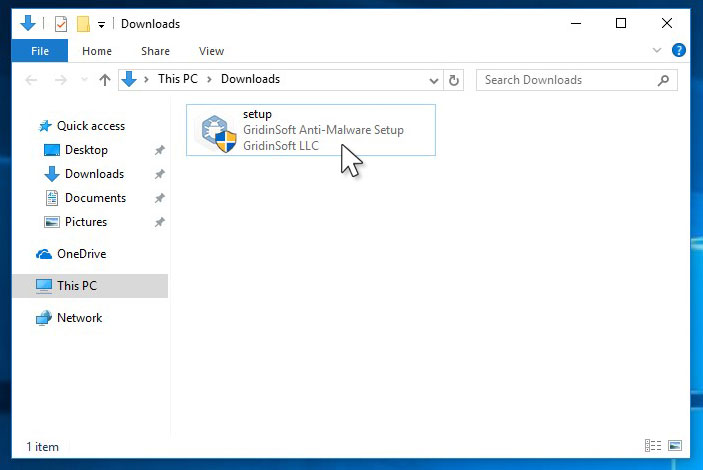
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press "Install" button.
Once installed, Anti-Malware will automatically run.

Wait for the Anti-Malware scan to complete.
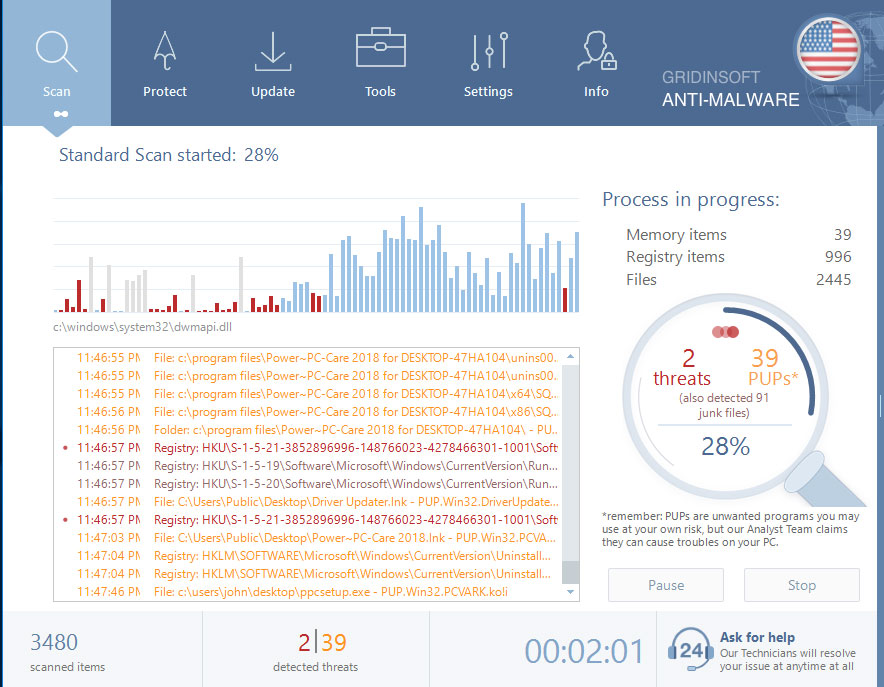
GridinSoft Anti-Malware will automatically start scanning your computer for Nemty infections and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
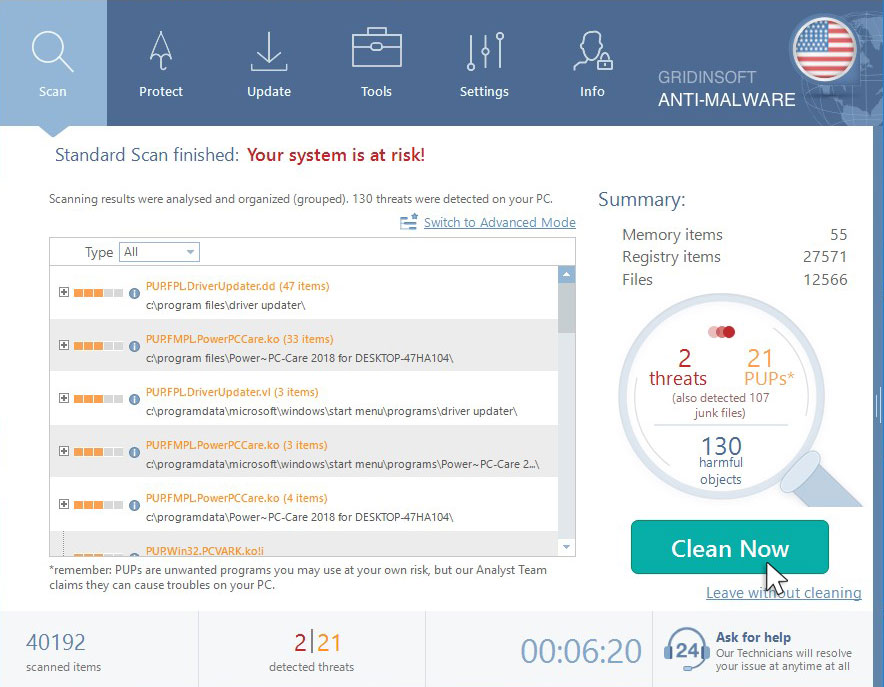
Click on "Clean Now".
When the scan has completed, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
How to decrypt .nemty files?
Jan 02, 2020 - Update to the #Nemty #Ransomware decryptor for Nemty versions 2.2 & 2.3
You can download and use Nemty Decryptor that Tesorion4 released if you were hit by Nemty virus.
For using Nemty Decryptor, please read the instructions on the Usage tab, it explains what files you can upload:
Hi, and thank you for using our Nemty decryptor!
You will have to go through a few steps to decrypt your files.
1. First please upload the ransom note from your encrypted system using File/Open.
This file is named: “NEMTY-DECRYPT.txt” or “_NEMTY_#######_-DECRYPT.txt” and
can be found in every folder with encrypted files.
2a. Optional step, depending on the result of step 1.
Please upload a single encrypted file from your system using File/Open.
The file may be in one of the formats below:
a. .docx
b. .pdf
c. .png
d. .pptx
e. .xlsx
f. .zip
2b. Please wait for the decryption server to finish processing your file.
This may take several minutes or up to half an hour, depending on how busy the decryption server is.
After this step, this application should be able to decrypt your files.
3. Lastly, please select a folder to decrypt (default is the path of the selected file), using 'Select'.
After selecting this folder press 'Decrypt' to start the decryption,
it will try to decrypt all files in that folder, as well as in any folders below it.
This may take a (very) long time.
For now;
please select ‘File/Open...’ or 'Start' to start the first step.
What the next?
If the guide doesn’t help you to remove Nemty infection, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments for getting help. Good luck!
User Review
( votes)References
- How To Change Remote Desktop (RDP) Port: https://howtofix.guide/change-remote-desktop-port-on-windows-10/
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison
- Tesorion site: https://www.tesorion.nl/


Bonjour,
J’ai un ordinateur qui a été infecté par le ransonware nemty (version ?). Le disk système a été formaté et une nouvelle installation a été faite, ce qui m’a permis de me débarrasser du virus. Auparavant j’ai copié sur un disque externe un certain nombre de fichier encryptés sans la NOTE RANSOM. Avez-vous une solution en dehors de celle proposé par TESORION pour décrypter mes fichiers.