Microsoft reported about coordinated attempt to eliminate one of the largest botnets, Necurs, which distributes spam and malware.
Thus, it is believed that due to to Necurs more than 9 million computers were infected worldwide. For example, according to Microsoft, the company’s engineers recently monitored a single computer infected with Necurs, from which more than 3.8 million messages were sent to more than 40.6 million victims.Microsoft and partners across 35 countries took coordinated legal and technical steps to disrupt one of the world’s most prolific botnets, called Necurs. This disruption is the result of eight years of tracking and planning and will help ensure the criminals behind this network are no longer able to use key elements of its infrastructure to execute cyberattacks”, — reported in Microsoft.
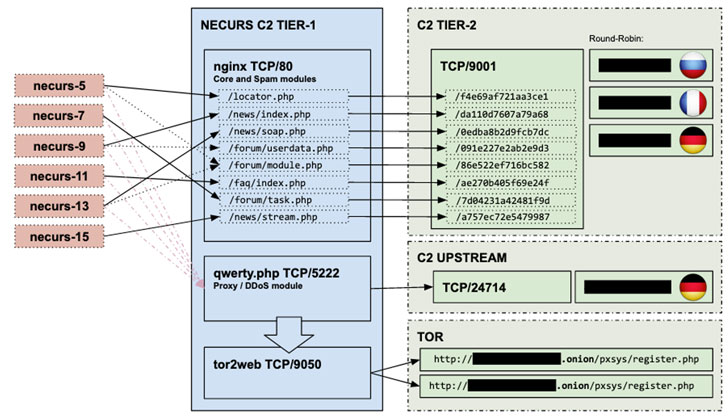
An attempt to destroy the botnet was made after Microsoft and its industry partners (cybersecurity companies, providers, domain registrars, CERTs and law enforcement agencies) were able to hack Necurs DGA, a domain generation algorithm by which the botnet generates random domain names.
Using DGA, Necurs operators register domains for several weeks or months, and then place management servers on them, to which bots (infected computers) connect to receive new commands.
Destruction of the DGA structure allowed experts to create complete list of future Necurs domains and management servers, and now became possible to block and prevent their registration.
We were able to accurately predict the more than six million unique domains that will be created over the next 25 months. Taking control of existing sites and limiting the possibility of registering new ones, we undermined the work of the botnet”, — said Tom Burt, vice president of Microsoft.
Additionally, a Microsoft law team joined the case, and received a court order granting the company control over existing Necurs domains that are located in the United States. However, I must say that Microsoft lawyers are quite strong team in the cyberwar of the new era: we recently talked about how they seized control of the domains of the North Korean group Thallium.
After Microsoft took control of the existing Necurs infrastructure, the company’s specialists and its partners were able to apply the sinkhole to the botnet and get information about all the bots. Microsoft is now working with Internet service providers and CERT teams around the world to notify affected users about the problem, so that they can remove the malware from their computers.
The company BitSight, which played a decisive role in this operation, has already published a report on the Necurs infrastructure, having studied the botnet before its elimination.