A new phishing campaign targets Microsoft Office 365 and Outlook corporate credentials from US organizations in the military defense, security software, manufacturing supply chain, healthcare and pharmaceutical industries.
Let me remind you that we also reported that Microsoft warns of ice phishing in blockchain and smart contracts, and also that Hackers attack e-banking users by phishing QR codes.According to researchers from ZScaler, the new phishing campaign has tactics and methods similar to another campaign discovered in mid-2020.
Attackers use postal services in Japan to send their messages and spoof the sender’s address, pretending to be employees of the victim company.
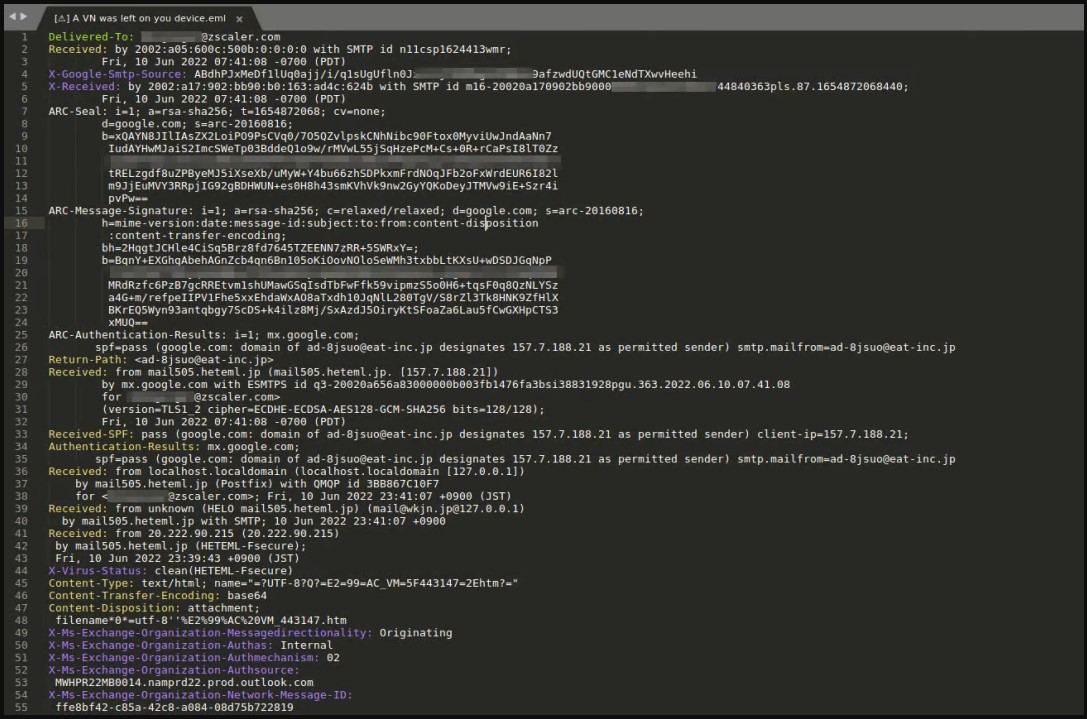
Fraud email headers
The emails contain an HTML attachment with a musical note symbol in the name, disguising the file as an audio message. In fact, the file contains obfuscated JavaScript code that takes the victim to a phishing site.
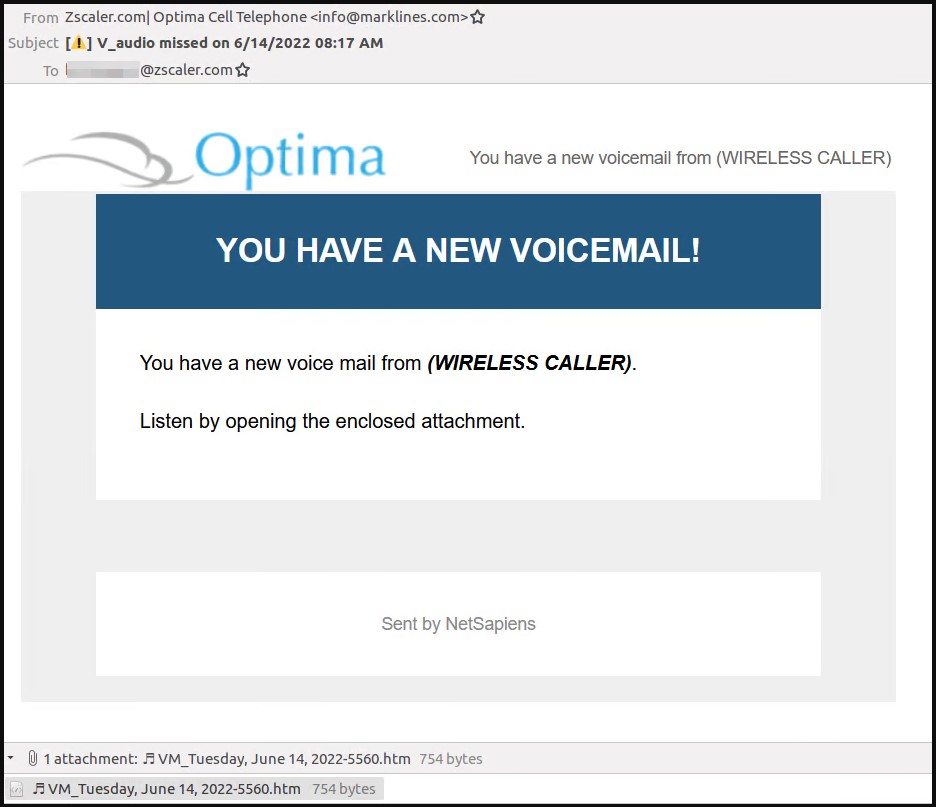
Message that is used in phishing campaign
The URL format is crafted to give the impression that the site is an official subdomain of the company.

Domain name generation process
Before ending up on the site, the victim goes through a CAPTCHA check, which actually serves to bypass anti-phishing systems. Once users pass this stage, they are redirected to a real phishing page that steals Microsoft Office 365 accounts.
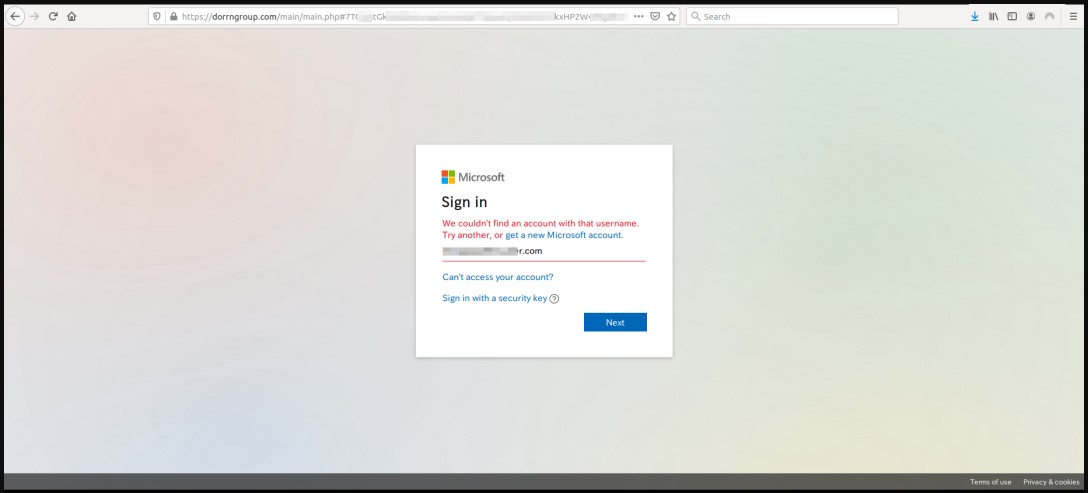
Final phishing page
However, users that were attentive enough may notice that the login page domain is not owned by Microsoft and looks like this:
- briccorp[.]com
- bajafulfillrnent[.]com
- bpirninerals[.]com
- lovitafood-tw[.]com
- dorrngroup[.]com
- lacotechs[.]com
- brenthavenhg[.]com
- spasfetech[.]com
- mordematx[.]com
- antarnex[.]com
That is why, before entering a login and password, users should always check the site they are on so as not to send data to intruders.
One of the reasons why phishing is so popular is that, despite great experience with computers and constant training provided by companies to increase employee security awareness, humans are still the weak link in cybersecurity. According to the Egress Insider Data Breach Survey 2021, 84% of organizations surveyed said that human error caused at least one of their computer security incidents.



