What is LimeRat?
LimeRat, also known as Lime Remote Administration Tool, is a malicious program that operates as ransomware, cryptocurrency miner, information stealer, keystroke logger, and computer worm.
This dangerous malware can cause data/financial loss, privacy problems, and various other serious issues. If LimeRat has infected your computer, you should immediately remove it.
Overview of LimeRat malware
LimeRat is a user-friendly tool that anyone can use. It enables cyber criminals to customize each payload with different attributes. When LimeRat connects to the victim’s computer or infected operating system, it automatically receives information about the operating system, CPU, geolocation (country), user, and other details.
| Name | LimeRat Remote Administration Tool |
| Detection | Backdoor:Win32/LimeRat.YA!MTB |
| Similar behavior | Toitoin, Muggle, Truebot |
| Damage | It can operate as ransomware, encrypting files and demanding a ransom for their release. Act as a cryptocurrency miner, using computer resources to mine cryptocurrencies like Monero. It can steal information, including keystrokes and screenshots, and spread itself as a computer worm. It can cause data and financial loss, invade privacy, and lead to serious issues for infected systems. |
| Fix Tool | It is important to remove LimeRat immediately if it has infected your computer. |
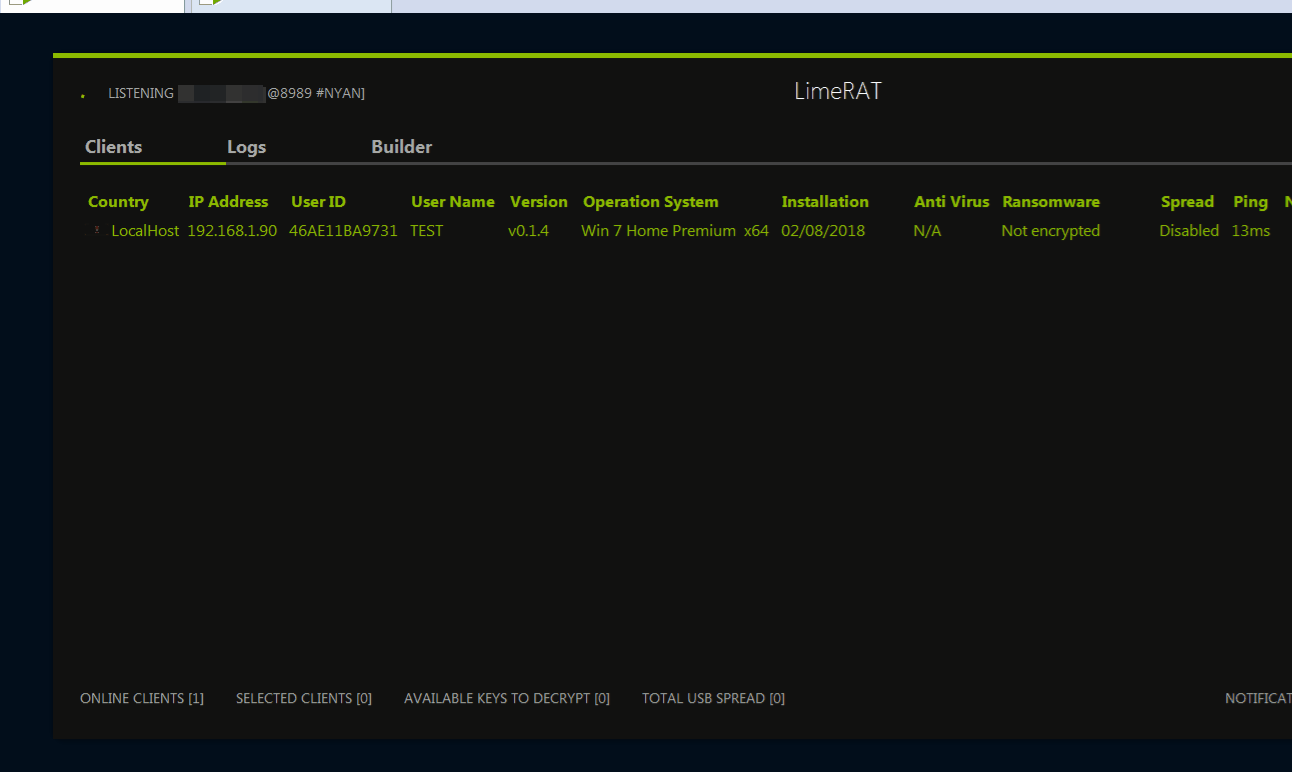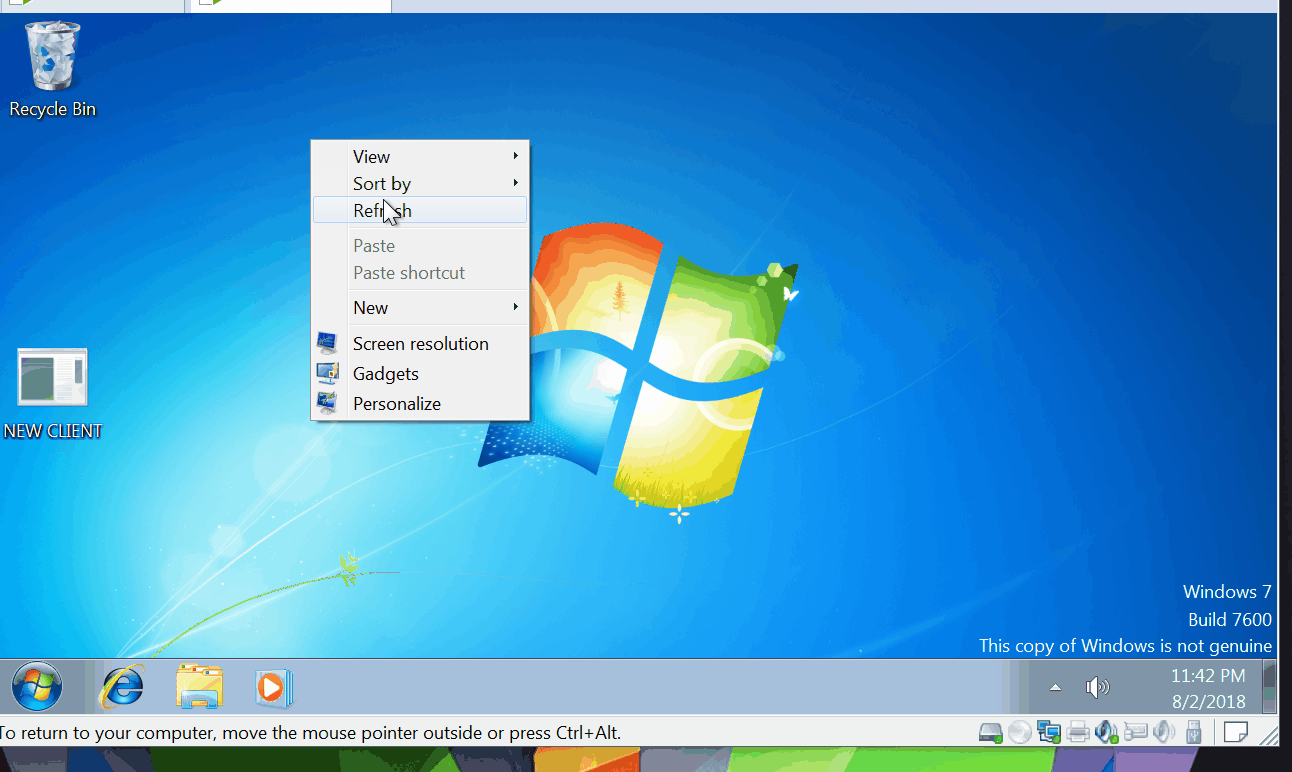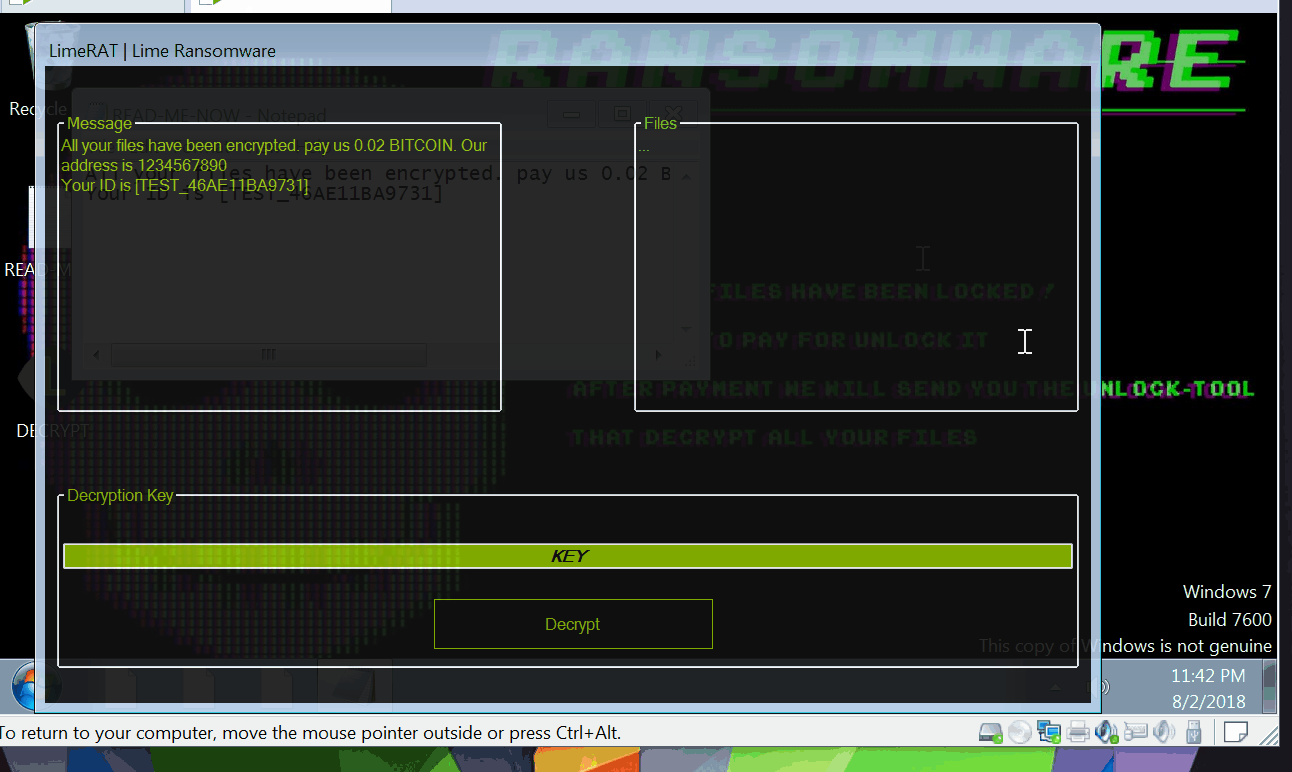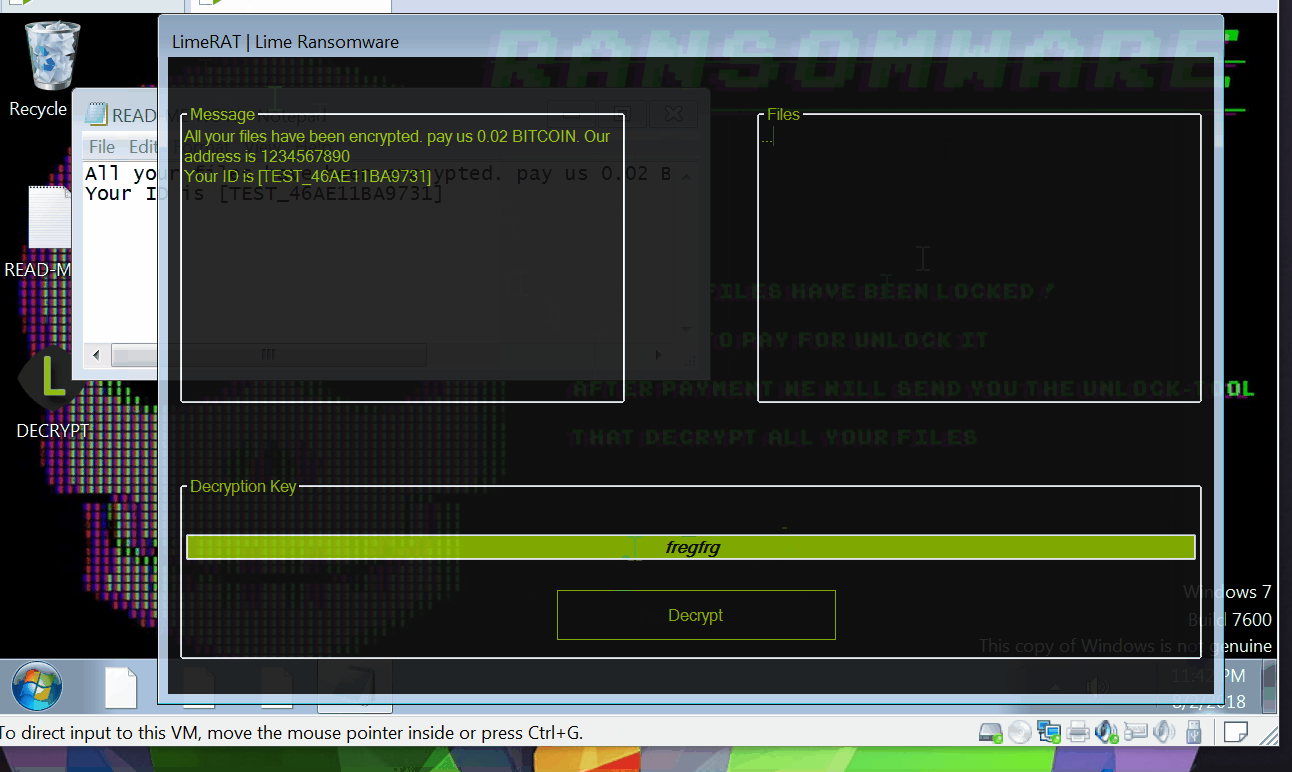
The administrative panel of LimeRat displays all connected or infected systems, allowing criminals to choose the type of attack. For instance, it can encrypt files using ransomware. Users can create a unique ransom message and select an image to appear after encryption.
All encrypted files are renamed with the “.Lime” extension. Additionally, LimeRat can deploy a keystroke logger tool to record key presses on the keyboard. However, it cannot capture auto-filled data or information copied to the clipboard. LimeRat can also propagate itself as a computer worm.
LimeRAT as Ransomware
Worms are programs that replicate to spread to other systems. LimeRat can also capture victims’ computing activities by taking screenshots. Furthermore, it is capable of running a cryptocurrency miner for mining Monero. These programs utilize computer hardware such as the CPU and GPU to solve complex mathematical problems.
Infected computers consume more power, experience reduced performance, or may not respond at all. Users may encounter unexpected system shutdowns and higher electricity bills. Moreover, this remote administration tool can be employed to steal various information and cryptocurrency details.
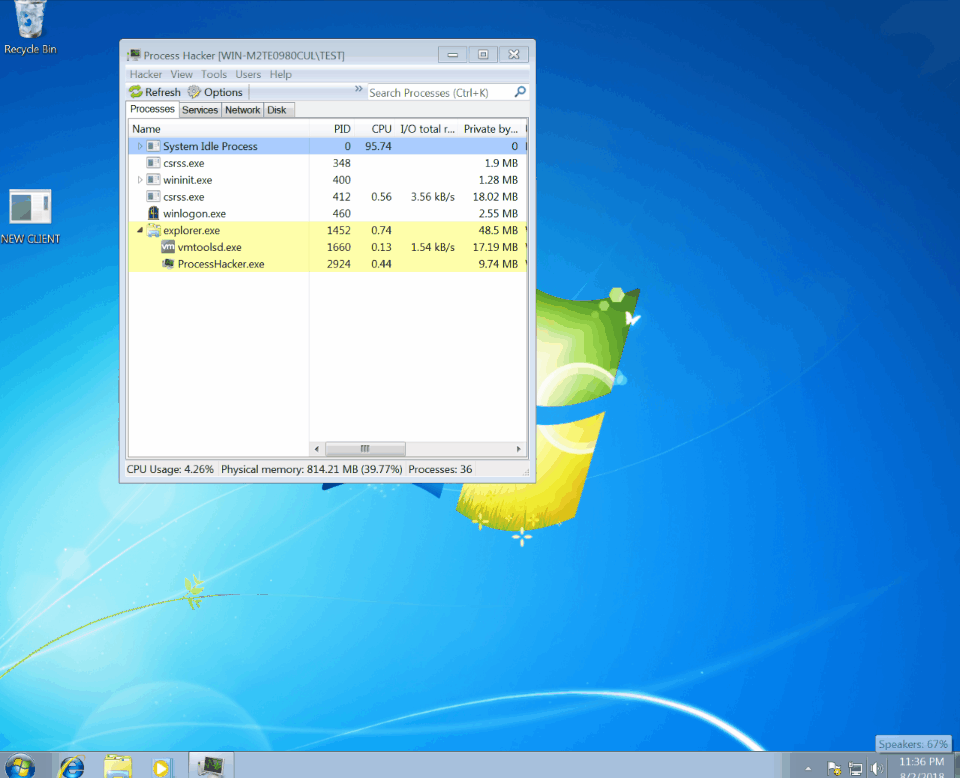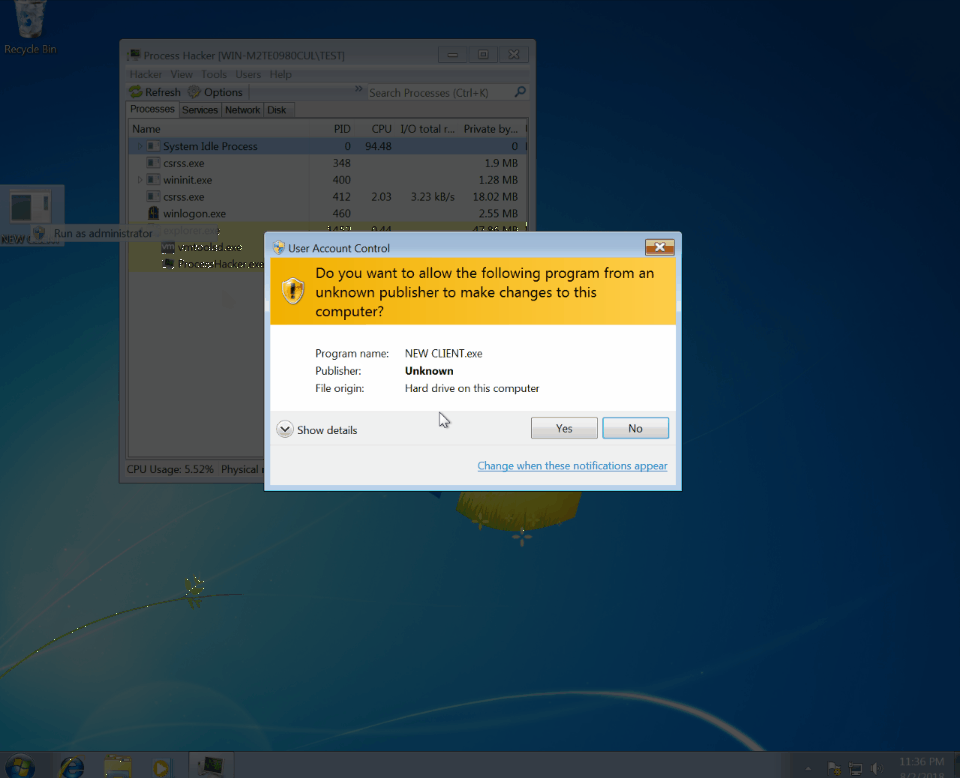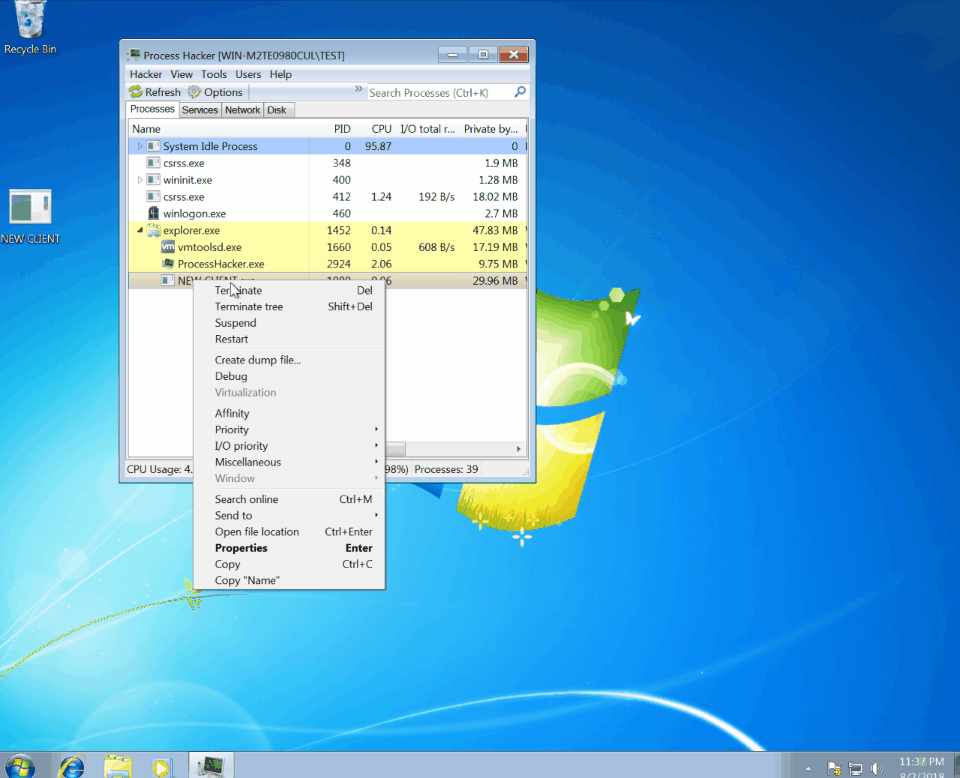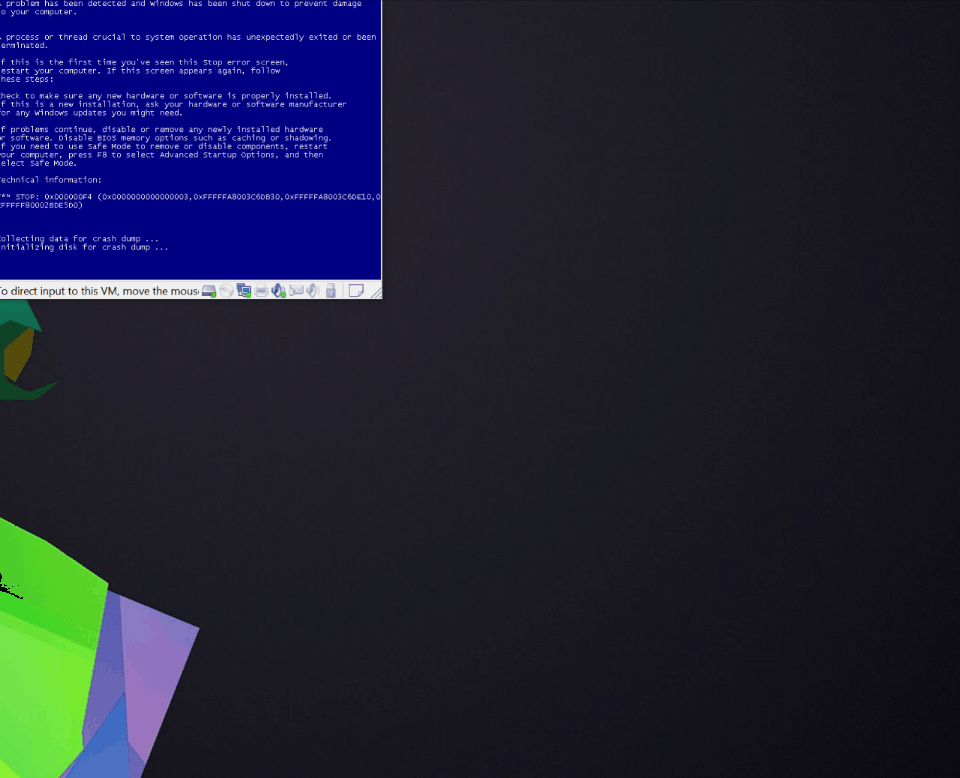
LimeRAT Process
For instance, it can steal credentials of banking/crypto wallet accounts and other sensitive information. LimeRat can compromise privacy, steal personal data, cause financial and data loss, and lead to other issues. If you suspect that your system is infected with this RAT, take immediate action to eliminate it.
Examples of RAT-type malware
There are numerous RATs available online, ranging from advanced to basic. Some examples of other programs in this category include Appyrinceaskeda, njRat, and Bifrost 3. While these programs possess varying capabilities, their primary purpose is revenue generation.
Cyber criminals utilize these tools to extort money from individuals by stealing private information and infecting their computers with ransomware, among other methods. If used maliciously, these tools can cause severe problems.
How did LimeRat infiltrate my computer?
Malicious programs are spread through various techniques. The most common methods include spam campaigns, software cracking tools, trojans, dubious software download sources, and fake software updating tools. Cyber criminals distribute malware through spam campaigns by sending emails with attached files.
These emails are often disguised as official or important to deceive recipients into opening the attachments. The attached files can be executable files, archive files (such as RAR and ZIP), PDF documents, JavaScript files, Microsoft Office documents, and more. Once opened, these files infect computers with malicious programs.
Software cracking tools are used to avoid paying for official software. However, users who utilize these tools often end up downloading and installing malware. Trojans are programs designed to propagate malware and cause chain infections, but they are only effective if the program is already installed.
Free file hosting websites, freeware download websites, and peer-to-peer networks like torrent clients and eMule are examples of dubious software download sources. These sources can present malicious files as harmless and legitimate, tricking users into downloading and installing malware.
Fake software update tools infect systems by downloading malware instead of updating the software or by exploiting vulnerabilities in outdated software.
How to avoid malware installation?
To avoid installing malware, refrain from opening email attachments from unknown or suspicious addresses. If an email seems irrelevant, do not open any included links or files. Download software from official and trustworthy websites using direct download links. Avoid using the aforementioned tools, as they can distribute malicious programs.
Do not update installed software using unofficial tools. The only safe way to update is through tools designed by official developers.
This also applies to software activation: cracking tools are illegal and used to propagate malware. Install and regularly run system scans with antivirus or anti-spyware software. If you suspect your computer is already infected, we recommend running a scan with Gridinsoft Anti-Malware to automatically remove infiltrated malware.
How to remove the LimeRat from my PC?
LimeRat malware is very hard to eliminate by hand. It places its data in numerous locations throughout the disk, and can recover itself from one of the parts. Moreover, a range of changes in the windows registry, networking configurations and Group Policies are pretty hard to identify and change to the initial. It is far better to make use of a special tool – exactly, an anti-malware app. GridinSoft Anti-Malware will fit the best for malware removal objectives.
Why GridinSoft Anti-Malware? It is pretty lightweight and has its databases updated almost every hour. Additionally, it does not have such problems and exploits as Microsoft Defender does. The combination of these details makes GridinSoft Anti-Malware perfect for clearing away malware of any kind.
Remove the LimeRat with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of LimeRat the default option is “Delete”. Press “Apply” to finish the malware removal.



Frequently Asked Questions (FAQ)
LimeRat, also known as Lime Remote Administration Tool, is a malicious program that can perform various harmful actions such as ransomware encryption, cryptocurrency mining, information stealing, keystroke logging, and spreading as a computer worm.
LimeRat can infiltrate computers through methods like spam campaigns, software cracking tools, trojans, dubious software download sources, and fake software update tools.
LimeRat can cause data and financial loss, invade privacy, lead to reduced system performance, unexpected shutdowns, higher electricity bills, and facilitate the theft of sensitive information and cryptocurrency details.
To avoid malware installation, it is recommended to avoid opening email attachments from unknown or suspicious sources, download software only from official and trustworthy websites, refrain from using software cracking tools, and regularly update software through official channels.
If LimeRat has infected your computer, it is crucial to take immediate action to remove it. You can use reliable antivirus or anti-malware software to scan and eliminate the malware automatically.
How to Remove LimeRat Malware
Name: LimeRat
Description: LimeRat is a malicious program that can perform various harmful actions. It can operate as ransomware, encrypting files and demanding a ransom for their release. It can also act as a cryptocurrency miner, using computer resources to mine cryptocurrencies like Monero. LimeRat can steal information, including keystrokes and screenshots, and spread itself as a computer worm. It can cause data and financial loss, invade privacy, and lead to serious issues for infected systems. It is important to remove LimeRat immediately if it has infected your computer.
Operating System: Windows
Application Category: Malware


