ThreatFabric experts studied the Letscall malware toolkit, which is used for voice phishing in South Korea.
An interesting feature of these attacks is that if the victim tries to call the bank, the malware intercepts the call and redirects the attackers to the call center.
Once installed, this malware redirects victims’ calls to a call center controlled by hackers. There, specially trained operators posing as real bank employees learn confidential information from unsuspecting victims.
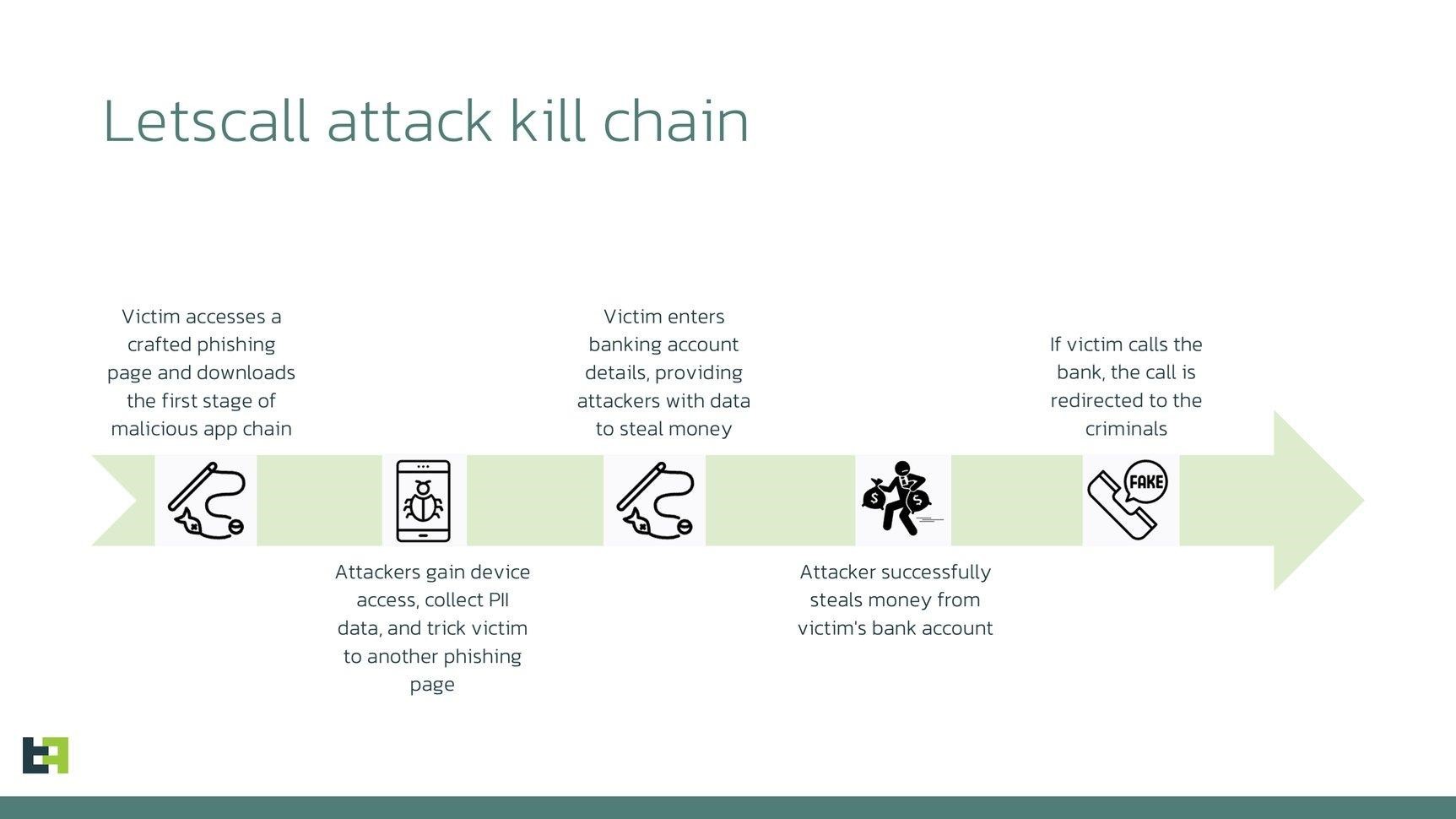
Scheme of Letscall attacks
Let me remind you that hackers have also learned to use ChatGPT for phishing.
We also wrote about banking phishing using QR codes and a phishing campaign against Microsoft Office 365 users.
According to ThreatFabric, the hack group behind Letscall includes Android developers, designers, interface and backend developers, and call center operators specializing in voice attacks and social engineering.
Experts describe Letscall as a multifunctional spyware or RAT (Remote Access Trojan), which was created with great attention to video and audio communication with the victim, and is also focused on intercepting messages and phone calls. Location tracking is also an important target for these attackers.
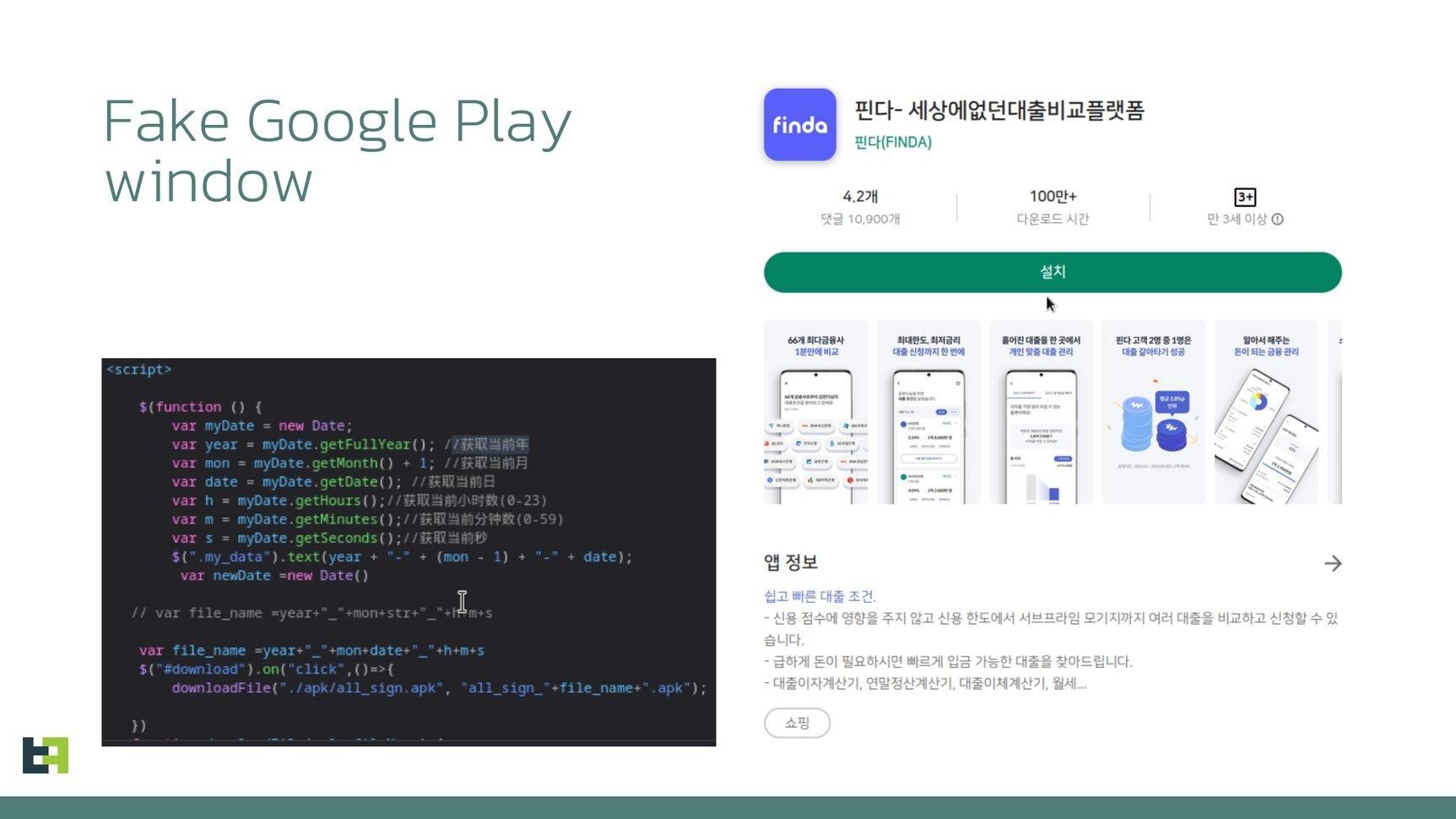
It all starts with the creators of Letscall using a multi-stage attack to trick their victims into downloading malicious apps from a website that mimics the official Google Play Store. Apparently, black hat SEO and social engineering using spam are used for this.
Fake Google Play Store
As a result, the infection is carried out in several stages: first, the downloader application, downloaded from the fictitious Google Play Store, prepares the victim’s device for installing powerful spyware: it receives the necessary permissions, opens the phishing page, and installs the second-stage malware received from the command and control server.
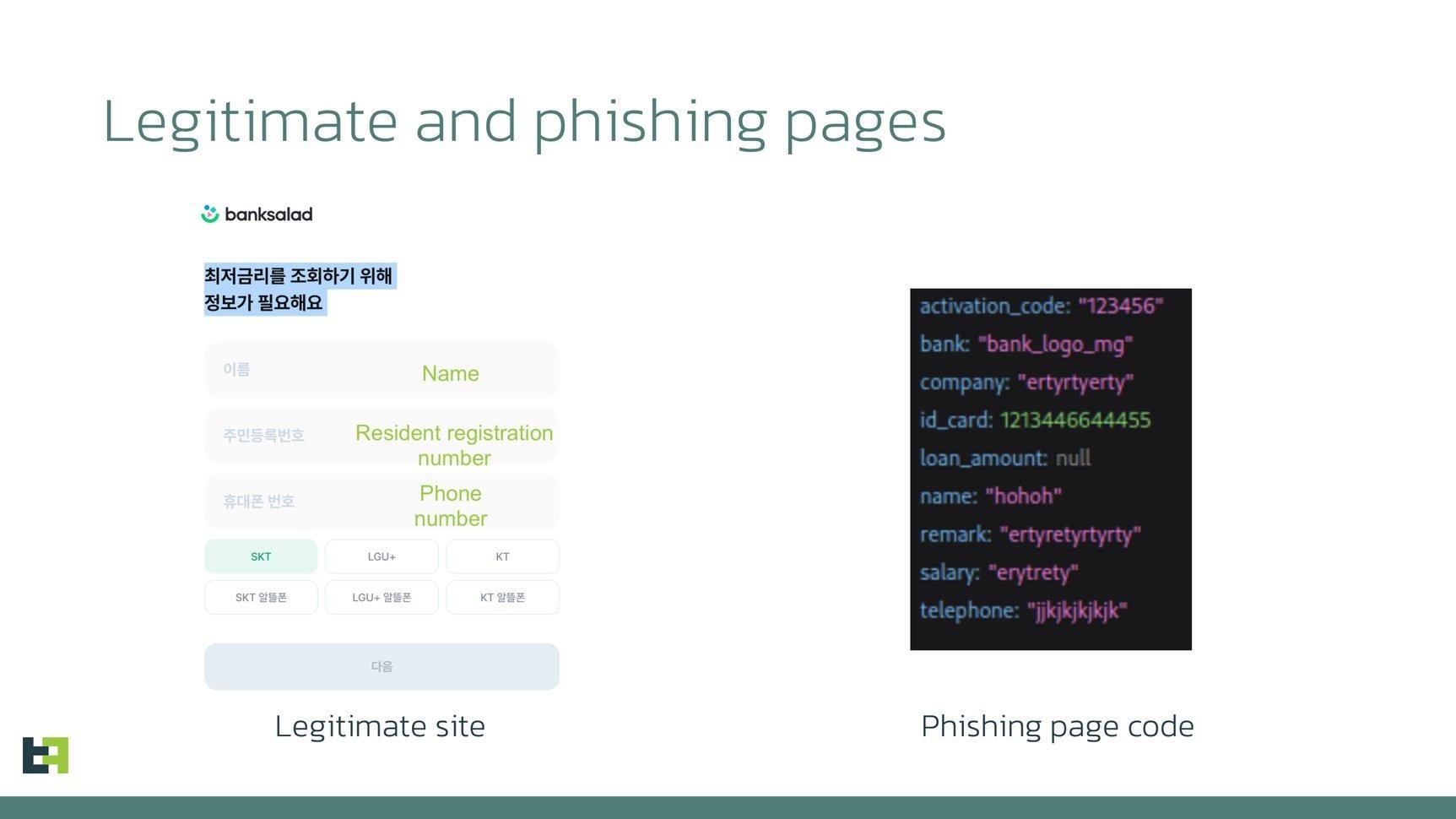
On the mentioned phishing page, which can imitate, for example, the sites of well-known loan offer aggregators, the victim is persuaded to provide confidential information: identity document details, phone number, home address, salary, name of the employer company, and so on. This data will be automatically transferred to attackers.
As a result, hackers either use the received data to fill out a similar form on the real site (to apply for a loan), or the phishing page generally acts as a proxy between the victim and the page of this loan aggregator.
The second stage of the attack is the installation of a spyware application that helps the attackers steal data and also registers the infected device on the P2P VoIP network used to communicate with the victim via video or voice calls. In addition, this application prepares the launch of the third stage of the attack.
At the third stage, another application is installed on the victim’s device, which has the functionality to make phone calls. Attackers use it to redirect calls from the victim’s device to the call center of the hackers themselves.
Moreover, among the assets of the third APK there are pre-prepared voice messages in MP3 format that will be played back if the victim tries to call the bank.
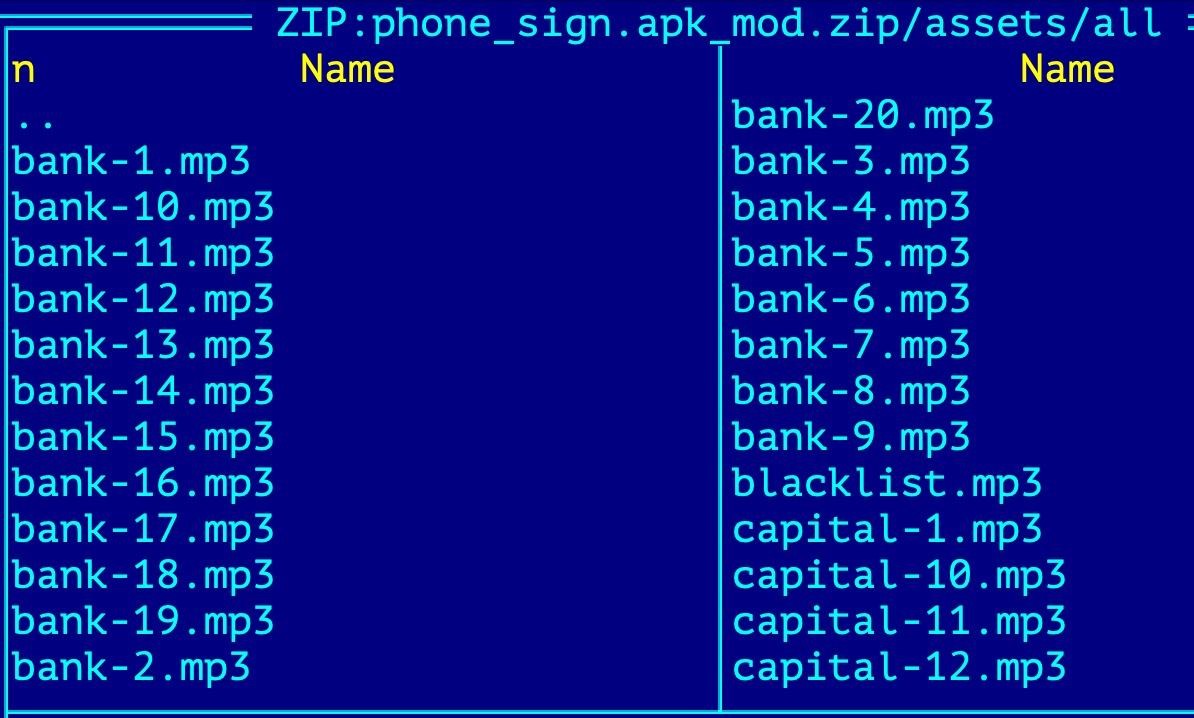
The researchers note that Letscall uses WEBRTC, a VoIP traffic routing technology, to operate and connect victims with call center operators. In addition to high quality voice and video calls, as well as to bypass NAT and firewalls, hackers rely on STUN/TURN techniques, including Google’s STUN servers.
In addition, according to analysts, some versions of the bootloader were protected using Tencent Legu obfuscation or using Bangcle (SecShell). The second and third stages of the attack used long names in the directory tree of the ZIP files and various manifest mangling methods.

