Two malicious file management apps have been found on Google Play with over 1.5 million installations in total.
They collected a lot of user data, far beyond the information they needed for their work, and then sent the collected information to China.
Recall that we also reported that the US authorities published a list of vulnerabilities that are most often exploited by Chinese hackers, but there is information that the policy of the Chinese authorities encourages the collection of vulnerabilities for attacks by Western companies.
The media also wrote that the United States and Britain accused Chinese government hackers of attacking Microsoft Exchange servers.
Researchers at mobile threat company Pradeo report that the first app was called File Recovery and Data Recovery (com.spot.music.filedate) and had at least a million installs. The second application, called File Manager (com.file.box.master.gkd), had at least 500,000 downloads. Both have now been removed from the Google Play Store.
Both apps were published by the same publisher (wang tom). Their description, in the Data Safety section, states that they do not collect any user data, but this was a misinformation.
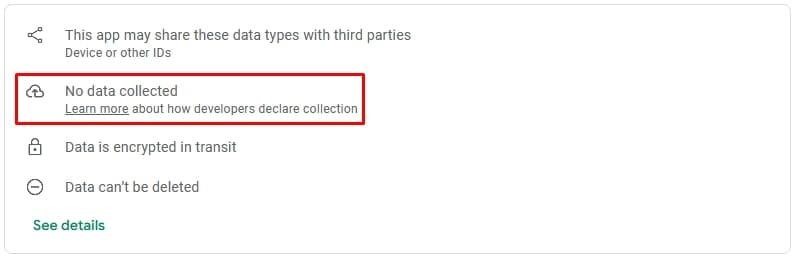
Analysts write that in fact, applications extracted the following information and transmitted it to servers located in China:
- a list of contacts from the device’s memory, as well as data on connected e-mail and social networking accounts;
- images, audio, and video that have been manipulated or restored through malicious applications;
- real-time user location;
- mobile country code;
- the name of the telecom operator;
- network code of the SIM provider;
- operating system version;
- make and model of the device.
Although some applications may collect such data in order to work, file managers obviously did not need this. Worse, the information was collected secretly and without the consent of users.
The researchers add that apps have hidden their icons from the home screen to make them harder to find and remove. They could also abuse the permissions the user gave them during installation to reboot the device and run in the background.
Experts believe that the creator of these applications used emulators or bot farms to increase the number of installations and increase the popularity of their products. This theory is backed up by the low number of reviews on Google Play, which clearly didn’t match the app’s huge user base.

