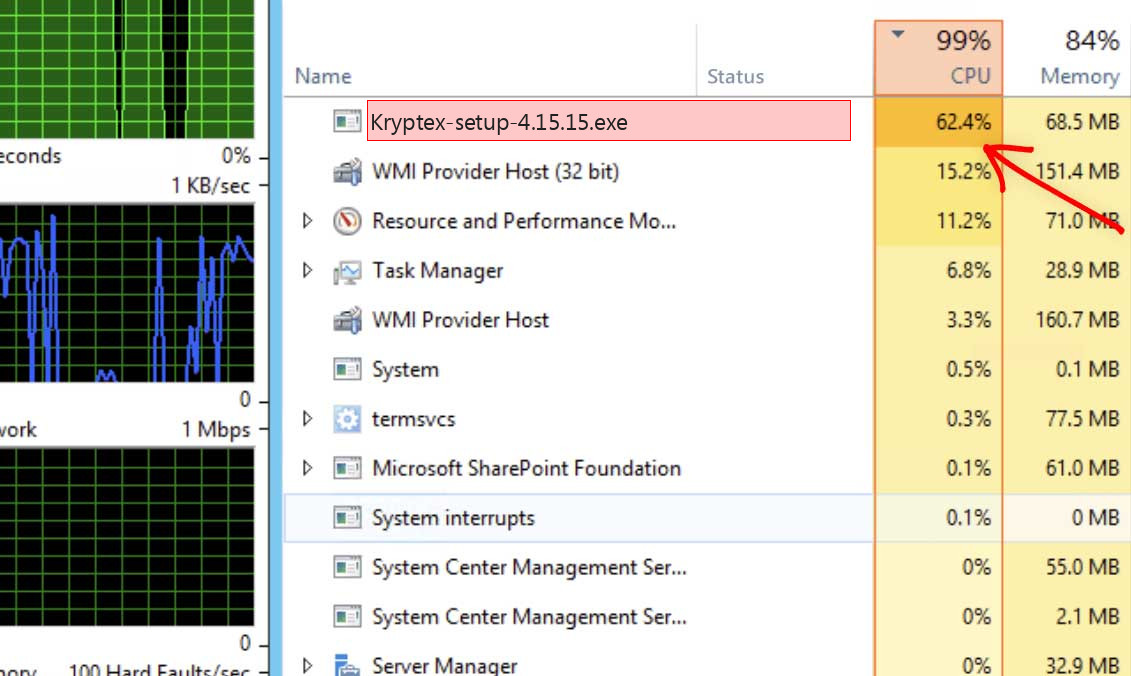
Kryptex-setup-4.15.15.exe process is a Trojan Coin Miner that utilizes the contaminated computer system’s sources to mine digital currency without your authorization. It can be Monero, Bitcoin, DarkCoin or Ethereum.
About “Kryptex-setup-4.15.15.exe”
Kryptex-setup-4.15.15.exe will certainly utilize greater than 70% of your CPU’s power as well as graphics cards resources
What this indicates, is that when the miners are running you will find that your computer system is running slower as well as video games are stuttering or cold since the Kryptex-setup-4.15.15.exe is utilizing your computer’s sources to create profits on their own. This will certainly trigger your CPU to run at really high temperatures for prolonged time periods, which might shorten the life of the CPU.
Kryptex-setup-4.15.15.exe Technical Summary.
| File Name | Kryptex-setup-4.15.15.exe |
| Type | Trojan Coin Miner |
| Detection Name | Trojan:Win32/CoinMiner |
| Distribution Method | Software bundling, Intrusive advertisement, redirects to shady sites etc. |
| Similar behavior | Ngen.exe, Protect.exe, Gsvr.exe |
| Removal | Download and install GridinSoft Anti-Malware for automatic Kryptex-setup-4.15.15.exe removal. |
Besides reducing your PC, going for peek degree for very long times may trigger damage to your device and raise electrical energy costs.
Central processing unit is not the only hardware element that is exploited by Kryptex-setup-4.15.15.exe miner. graphic card is also attacked, and while little and well-protected processor cooling system is quite hard to crack, graphic cards have large and easy-to-access rotors, which can be easily broke if touched while spinning, for instance, by the user much earlier before the coin-miner injection. Malfunctioning cooling system, together with the unusually high load caused by Kryptex-setup-4.15.15.exe miner can easily lead to graphic card failure.
When a PC is infected with Kryptex-setup-4.15.15.exe trojan, usual signs include:
- Very high CPU and graphics cards usage
- Windows reduce as well as optimize slowly, as well as programs run slower.
- Programs don’t release as quickly.
- General sluggishness when using the computer.
How to detect Kryptex-setup-4.15.15.exe Coin Miner Trojan?
Unlike ransomware, cryptocurrencies mining risks are not obtrusive and also are most likely to stay unnoticed by the sufferer.
However, finding Kryptex-setup-4.15.15.exe danger is reasonably simple. If the target is making use of a GridinSoft Anti-Malware it is practically specific to discover any mining malware. Even without a protection service, the victim is likely to suspect there is something incorrect since mining bitcoin or various other cryptocurrencies is a really resource extensive procedure. One of the most typical signs and symptom is a visible and typically constant decrease in performance.
This signs and symptom alone does not inform the sufferer what the precise trouble is. The individual can experience similar problems for a variety of factors. Still, Kryptex-setup-4.15.15.exe malware can be really turbulent since it will certainly hog all readily available computing power as well as the sudden change in the way the infected tool performs is most likely to make the victim seek remedies. If the equipment of the impacted device is powerful enough, as well as the sufferer does not detect and also remove the danger swiftly, the power intake as well as consequently the power bill will certainly rise visibly also.
Observant users can also see strange alterations in the Task Manager, or any other tool for having a look on the actually active processes. System programs, that are typically started in the thread of Windows tasks, are displayed as the program started by the user. Besides this difference, you may also observe that the icon of the notebook, that is usual for system apps operating in the background, is substituted by another picture. And sometimes, Kryptex-setup-4.15.15.exe virus does not even attempt to mimic the system processes, and can be observed with his original name.
How to Remove Kryptex-setup-4.15.15.exe?
As soon as the target has determined that their problem is Kryptex-setup-4.15.15.exe threat, for the usual user there are a couple of solutions.
Use GridinSoft Anti-Malware would be the finest service. There is no scarcity of readily available cybersecurity software that will find and eliminate mining malware.
Additionally, if the infected equipment doesn’t have crucial information or the target has actually supported such information in a tidy place, as well as the customer has some experience, formatting the hard disk drives could function. This solution might not suffice if the infection has infiltrated one or more networks the device belongs of.
Download Removal Tool.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your system.
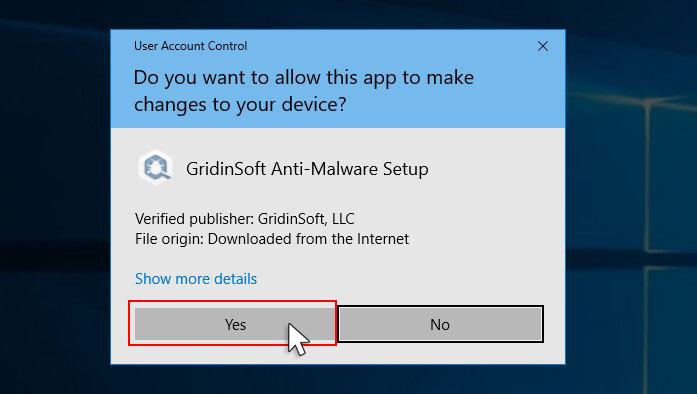
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.

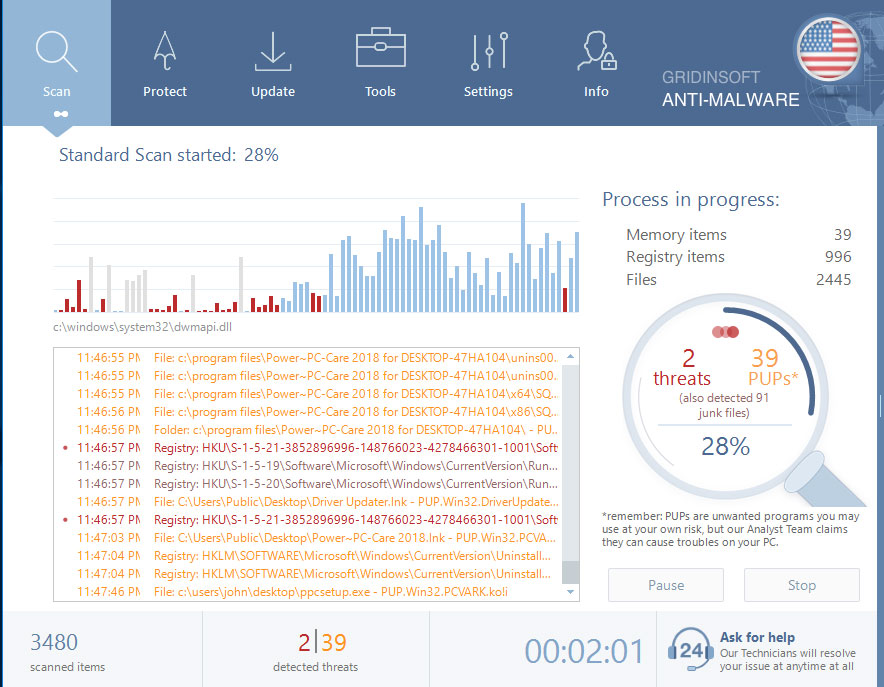
Wait for the Anti-Malware scan to complete.
GridinSoft Anti-Malware will automatically start scanning your system for Kryptex-setup-4.15.15.exe file and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
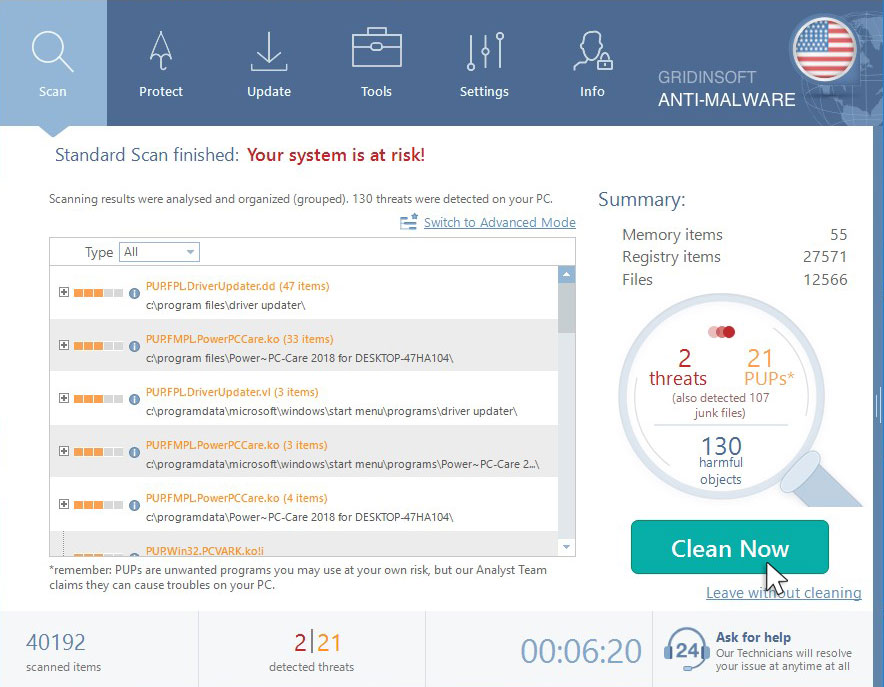
Click on “Clean Now”.
When the scan has finished, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
If the guide doesn’t help you to remove Kryptex-setup-4.15.15.exe infection, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments for getting help. Good luck!
Remove Kryptex-setup-4.15.15.exe Virus ⛏️ Trojan Coin Miner

Name: Kryptex-setup-4.15.15.exe
Description: The Kryptex-setup-4.15.15.exe is a Trojan Coin Miner that uses the infected computer’s sources to mine electronic money without your authorization. This Kryptex-setup-4.15.15.exe will create your CPU to go for very warm temperatures for prolonged periods of time, which could reduce the life of the CPU.
Operating System: Windows
Application Category: Trojan
User Review
( votes)References
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/comparison