KMSPico is quite a popular tool that can be correctly described as a hack tool for Windows. Because antivirus must be disabled to use this tool, it is straightforward to inject the malware using it as the carrier. In this post, you will read about the essence of KMSPico and its danger and usage for evil purposes.
What is KMSPico?
KMSPico, also known as KMS Pico, is a software tool that activates Microsoft products by utilizing an unofficial key management services (KMS) server. Many other hacking tools perform similar functions
KMSPico is a highly popular software activation tool for Windows and Office Suite, boasting millions of users worldwide. Interestingly, it is associated with numerous “official websites.”
If you search for the “official KMSpico site” on your preferred search engine, you’ll come across thousands of results. However, many portals caution against downloading KMSPico from Website A or Website B due to malware concerns—and they’re absolutely right.
It’s important to note that any “official” KMSPico website you encounter during your search is undoubtedly fake. This realization may lead some to believe that KMSPico is merely a myth. However, this tool is far from mythical. It does exist, with the latest version, 10.2.0, available for download exclusively from a members-only forum that was posted nearly a decade ago.
Is KMSPico Safe? An In-Depth Analysis
When it comes to the safety of KMSPico, it is important to consider the potential risks and security implications. Below, we delve into a detailed analysis of the safety aspects of KMSPico:
1. Malware and Security Concerns
KMSPico is commonly associated with malware and other security threats. Several cybersecurity organizations, such as Malwarebytes, have identified KMSPico and similar tools as risks. Here are some examples of malware detections associated with such tools:
- HackTool.KMSpico
- RiskWare.AutoKMS
- AutoKMS.HackTool.Patcher.DDS
- RiskWare.KMS
- HackTool.KMS
- HackTool.Agent.KMS
- HackTool.IdleKMS
- HackTool.AutoKMS
- HackTool.WinActivator
These detections highlight the potential dangers of using KMSPico and similar software tools.
2. Unauthorized Activation
KMSPico operates by bypassing the official activation process of Microsoft products. It changes the product key to a generic volume licensed (VL) key and connects to an unofficial KMS server. This method of activation is unauthorized and against Microsoft’s terms of service.
3. Legal Implications
Using KMSPico or any other software tool for unauthorized activation of Microsoft products violates copyright laws. Engaging in software piracy can have severe legal consequences, including fines and legal actions against individuals or organizations involved.
4. Unreliable Sources and Fake Websites
Searching for KMSPico may lead to numerous websites claiming to be the official source. However, it is important to note that these sites are almost always fraudulent. The genuine KMSPico tool is not distributed through official websites. Relying on such sources can expose you to counterfeit software, malware, and potential data breaches.
5. Trustworthy Alternatives
Instead of using KMSPico or similar tools, it is recommended to obtain legal licenses for Microsoft products. Genuine licenses ensure compliance with copyright laws, guarantee software authenticity, and provide access to updates and support from Microsoft.
Ultimately, the decision to use KMSPico should be made with careful consideration of the risks involved. It is crucial to prioritize cybersecurity, legality, and the protection of your personal and organizational data.
Note: The information provided above is based on cybersecurity reports and industry best practices. It is essential to conduct thorough research and consult legal experts for specific guidance regarding software licensing and compliance.
How does KMSPico work?
To comprehend the inner workings of KMSPico, it’s necessary to understand the process of KMS activation.
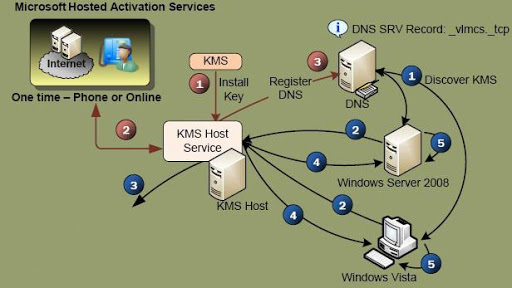
KMS activation is a legitimate method used to activate Windows licenses on client computers, particularly in large-scale scenarios (volume activation). Microsoft even provides documentation on creating a KMS activation host.
A KMS client establishes a connection with a KMS server, which acts as the activation host and contains the necessary host key for the client’s activation process. Once KMS clients are validated, the Microsoft product on these clients contacts the server every 180 days (6 months) to maintain its validity. However, setting up a KMS environment is only practical for organizations that possess Volume Licensed (VL) Microsoft products.
This is precisely what KMSPico exploits. After being installed on user clients, it transforms their retail version of Microsoft into a “Volume Licensed” version by simply changing the product key to a generic VL key. Additionally, KMSPico modifies the default KMS server to an unofficial KMS server established by the developer of the hacking tool.
It is worth noting that if the KMSPico developer decides to terminate the server, the users who rely on it will lose their activated Microsoft product status.
As it was mentioned, KMSPico is a hack tool that allows you to activate your Windows without purchasing the license key. The mechanism used is quite complicated, and the manual performance of this operation is likely impossible; that’s why such tools are so popular nowadays. Besides the Windows activation, KMSPico may also have a function of activating Microsoft Office.
The majority of anti-malware software detects this program as a hack tool/riskware; these types of hazards are about to be blocked instantly after the detection. Hence, to use KMSPico, you need to shut your antivirus down or add the application to the whitelist. Due to that fact, there is no trouble adding the virus you want through this app. And malware distributors know about this loophole, so the chance of getting infected via KMSPico is very high.
This hack tool’s ease of malevolent usage is caused by its main functionality. It connects to the Key Management Service (KMS, maintained by Microsoft)1. It sends it one of the leaked activation keys for OEM PC producers. Then the program receives the individual key for this device from the mentioned server, and the activation procedure completes. But what is the problem with changing the KMSPico configurations to force it to connect not to the KMS server but to the server that malware distributors control? After such manipulation, it is easy to send back a pack of viruses instead of the individual key; if the user tries to activate the system multiple times, he will get new and new viruses.
There is also a much more clumsy but the same effective method. When downloading the KMSPico, you don’t get the same program – there is an executable file of the trojan virus instead of the offered app. The problem is that the anti-malware program with working on-run protection will start notifying you about the malware presence (this time – about the trojan virus), so the user who has such a good security tool will stop at this point. Nonetheless, many people ignore this information and run the virus under the guise of the Windows activation tool.
KMSPico may also be dangerous in another way. Using the hacked Windows is a prosecuted action. And if the executive authorities detect such usage, you (or your corporation) will be fined a large sum of money. Keep this fact in mind if you have a cracked version of Windows on your home computer and are going to develop the program or to do any other activities which may uncover the fact of license hacking.
Which viruses may I get with the KMSPico?
Generally, most viruses you may get through the KMSPico and similar KMS-hacking apps are trojans of different categories. Usually, it is a trojan-downloader that will inject a lot of other viruses after getting launched, or Adrozek trojan, who has similar behavior with adware. A rare case is ransomware injection through the ransom-trojan – a specific type of trojan-downloader, which can make several system changes that make the ransomware activity much easier.
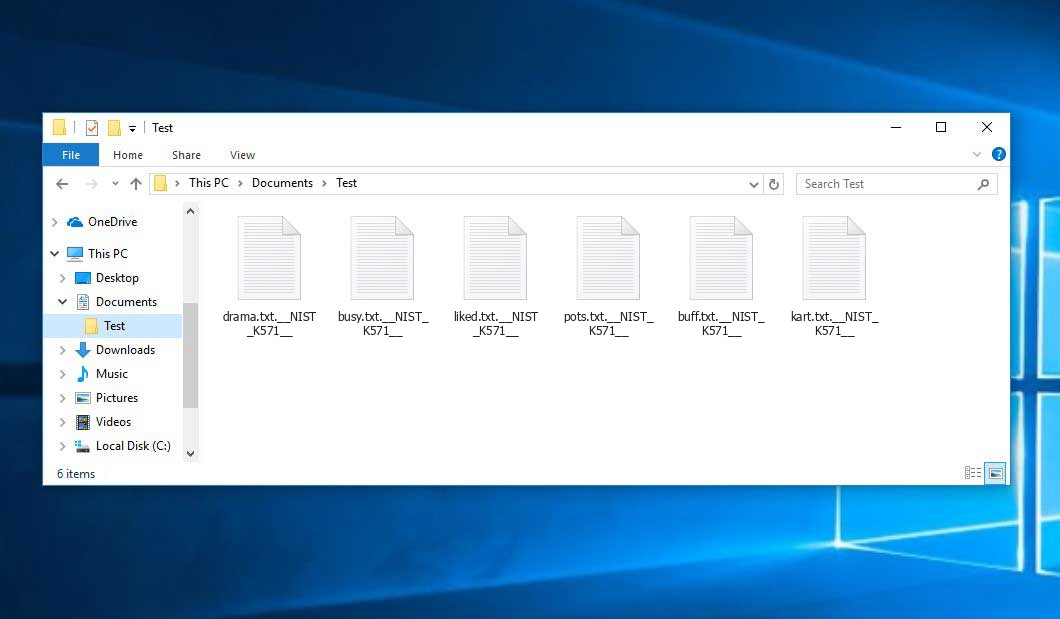
All of these viruses significantly influence the infected PC’s performance. And besides the usability harm, this malware may also damage your confidential data, especially when we talk about ransomware. It is recommended to remove this malware as soon as possible.
How can I understand that my version of KMSPico was a counterfeit?
The sign of the false program is the absence of its efficiency. Check your PC with an antivirus program if it does not show the results it was promoted with. The correct functioning of the KMSPico is also not a guarantee that there are no viruses onboard. However, if you are going to use such questionable programs, using anti-malware software must be like washing your hands during a pandemic.
If the malware from the KMSPico-related bundle were successfully injected into your system, you would see the common symptoms typical for trojan virus activity. System slowdown, blinking windows on the desktop, and many unknown apps running in the background and launched as a user process are the clearest signs of trojan presence.
How to wipe the trojans out of my PC?
Manual trojan removal is likely impossible due to the wide range of changes implemented by this type of virus. It is better to use anti-malware software. But the Microsoft Defender2, that is present on each computer with Windows 10, has a lot of vulnerabilities, and may be easily disabled by the trojans via Group Policies editing. Moreover, many users disable it manually due to the consumption of computer resources. Hence, it is not the most reliable solution.
GridinSoft Anti-Malware is a perfect solution for such a case. It has an On-Run Protection option, which allows it to detect & block viruses before the start of its activity. And the perfect efficiency of its scans will surely help you to deal with the malware that is already present on your PC.
Install and launch GridinSoft Anti-Malware. Start the Full scan: it will check all logical disks in your system, so the malware will surely be found.
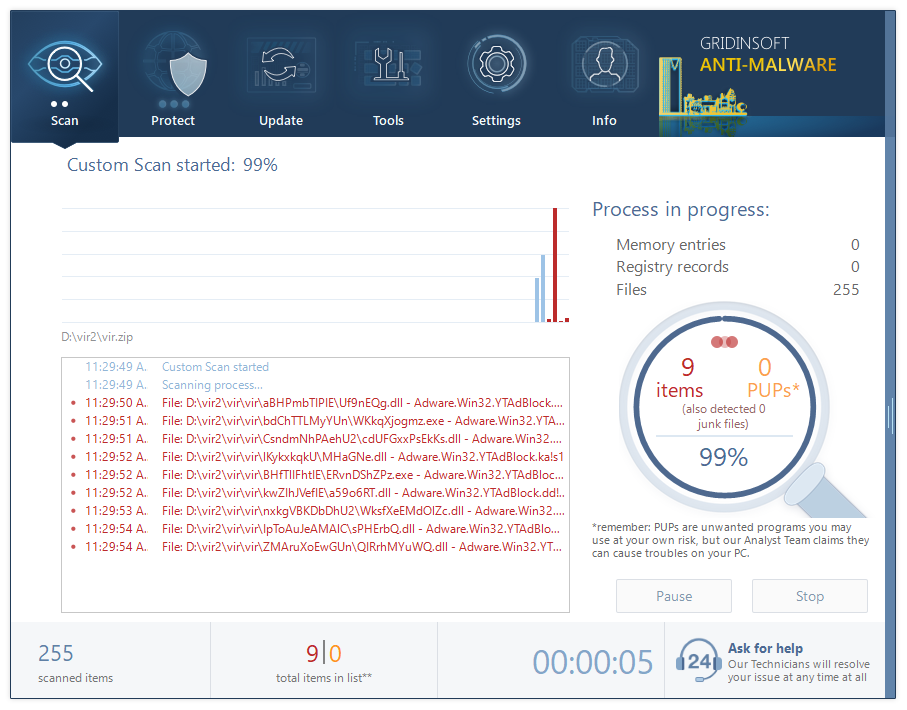
When the scan is over, press “Apply” to delete the detected malware.

Frequently Asked Questions (FAQ) about KMSPico
1. What is KMSPico?
KMSPico is a software tool used to activate Microsoft products, such as Windows and Office Suite. It utilizes an unofficial key management services (KMS) server for activation.
2. Is KMSPico safe to use?
Using KMSPico can pose security risks to your computer. It is often associated with malware, and downloading it from unofficial sources can potentially harm your system. It is recommended to use genuine and legally obtained software to ensure the safety of your device.
3. How does KMSPico work?
KMSPico works by altering the product key of a user’s Microsoft software to a generic volume licensed (VL) key. It also changes the default KMS server to an unofficial server set up by the tool’s developer. This allows the software to be activated without a legitimate license.
4. Can KMSPico activate all versions of Microsoft products?
KMSPico is primarily designed to activate Windows and Office Suite products. However, its compatibility may vary depending on the specific version and edition of the software. It is always advisable to use legal and authorized methods to activate Microsoft products.
5. Are there any legal alternatives to KMSPico for activating Microsoft products?
Yes, Microsoft provides legitimate methods for activating their products. This includes purchasing genuine licenses or using volume licensing for organizations. It is recommended to follow the official channels and obtain legal licenses to ensure compliance and security.
6. What are the risks of using KMSPico?
Using KMSPico carries several risks, including the potential for malware infections. By downloading and using unauthorized software, you expose your system to security vulnerabilities and compromise the integrity of your data. Additionally, using cracked or pirated software is against copyright laws and may lead to legal consequences.
7. Can I trust websites claiming to be the official KMSPico site?
No, websites claiming to be the official KMSPico site are almost always fraudulent. The official KMSPico tool is not distributed through official websites but is rather shared through unofficial channels. Beware of scams and only download software from trusted and reputable sources.
8. How can I ensure the legality and authenticity of my Microsoft products?
To ensure the legality and authenticity of your Microsoft products, it is recommended to purchase genuine licenses from authorized retailers or directly from Microsoft. This guarantees that you receive official software, updates, and support, while also avoiding potential security risks associated with counterfeit or cracked software.
9. What are the consequences of using counterfeit or pirated software?
Using counterfeit or pirated software is against copyright laws and can lead to legal consequences. It may result in fines, legal actions, and reputational damage. Moreover, such software often lacks important security updates and exposes your system to vulnerabilities and malware infections.
10. Where can I find reliable information about Microsoft product activation?
For reliable information about Microsoft product activation, it is best to refer to official Microsoft documentation, support forums, or contact Microsoft directly. These sources provide accurate and up-to-date information to ensure you follow legal and legitimate practices.
User Review
( votes)References
- About Key Management Service on Wikipedia
- Perfect Defender comparison with one of the top-tier antimalware programs





