Fragmentation and aggregation attacks (FragAttacks) is a new shape of cyberattacks, related to the network vulnerabilities. This hazard may be present everywhere, even in-home networks, in contrast to public Wi-Fi threats. Let’s figure out how it works, and how to protect you and your devices from this threat.
What are FragAttacks?
Cybersecurity world began talking about FragAttacks about two months ago. It is a group of various vulnerabilities, which are present on each Wi-Fi device in use. Every device which is able to connect to Wi-Fi networks, since the creation of this technology in 1997, is under attack. The whole list of with the description of vulnerabilities was published by Mathy Vanhoef – network security expert1. Earlier, he published his investigation on KRACK – the vulnerability of WPA2 protocol.
This time, the security breach appears even in WPA3, which is much more reliable than WPA2. WEP – the “original” Wi-Fi protection mechanism – is also under attack. As Vanhoef says, hackers can exploit it to get access to the attacked device and see the packets you send over this network. Some of the described vulnerabilities are related to design flaws, but fortunately, they are hard to exploit. 95% of all vulnerabilities appear to be possible because of the mistakes in Wi-Fi devices’ firmware.
How do FragAttack work?
There are two vulnerability sources for FragAttacks, determined by Mr.Vanhoef. Even though initially, they are related to different aspects of Wi-Fi technology, in deep areas, they have a lot of common traits. People used to think that setting up a password for their network is enough. Thus, let me bust that myth.
“External” security breaches
The developers of various software products and network engineers must keep their eye on the vulnerabilities. They are always present in systems. However, not all of them are discovered yet. Even after publishing the vulnerability, hackers must create a way to use that vulnerability. Nonetheless, all self-respecting companies update their products as soon as possible to avoid giving the hackers a chance and to avoid possible lawsuits in the future.
How can the problems in hardware or software be exploited? Let me tell you about the example. A lot of friends of mine use cheap Wi-Fi routers that were never updated. As Vanhoef showed in his research, hackers can break into your network, injecting an unencrypted Wi-Fi frame into your device. Especially high risks are with the mentioned cheap routers. Ones can sometimes pass the unencrypted packets, ignoring the security layer you set up.

The exact vulnerability that allows the injection of the unencrypted packet is related to the specific bug into certain models of Wi-Fi routers. When the device receives a handshake packet, he accepts it even if it is unencrypted. Hackers can imitate the handshake in the plaintext format, add to it the malicious part, and then cut this packet into two pieces. After receiving the pseudo-handshake, the router will automatically allow both this handshake and malevolent code.
Design flaws
Design flaws mean the problems which are related to the original idea of technology. Usually, the majority of these mistakes are fixed during the further development of this technology. However, when we are talking about Wi-Fi, there is a problem that depends not only on the technology but also on the exact device. This refers to hardware-related breaches that allow crooks to use FragAttacks.
It is also important to note that the majority of design flaws are quite hard to exploit. They must be conducted in specific consequences that are hard to reach. Nonetheless, you can never predict if the hacker can meet these consequences or not.
Aggregation attack
CVE-2020-24588. One of the reasons for the appearance of the “Frag..” particle in the name of FragAttacks. That breach is based on the feature that makes the Wi-Fi faster. Inside the network, small frames are aggregated into bigger ones to decrease the number of operations done. The beginning of each frame contains the header, which shows if it is a single frame or aggregated one.
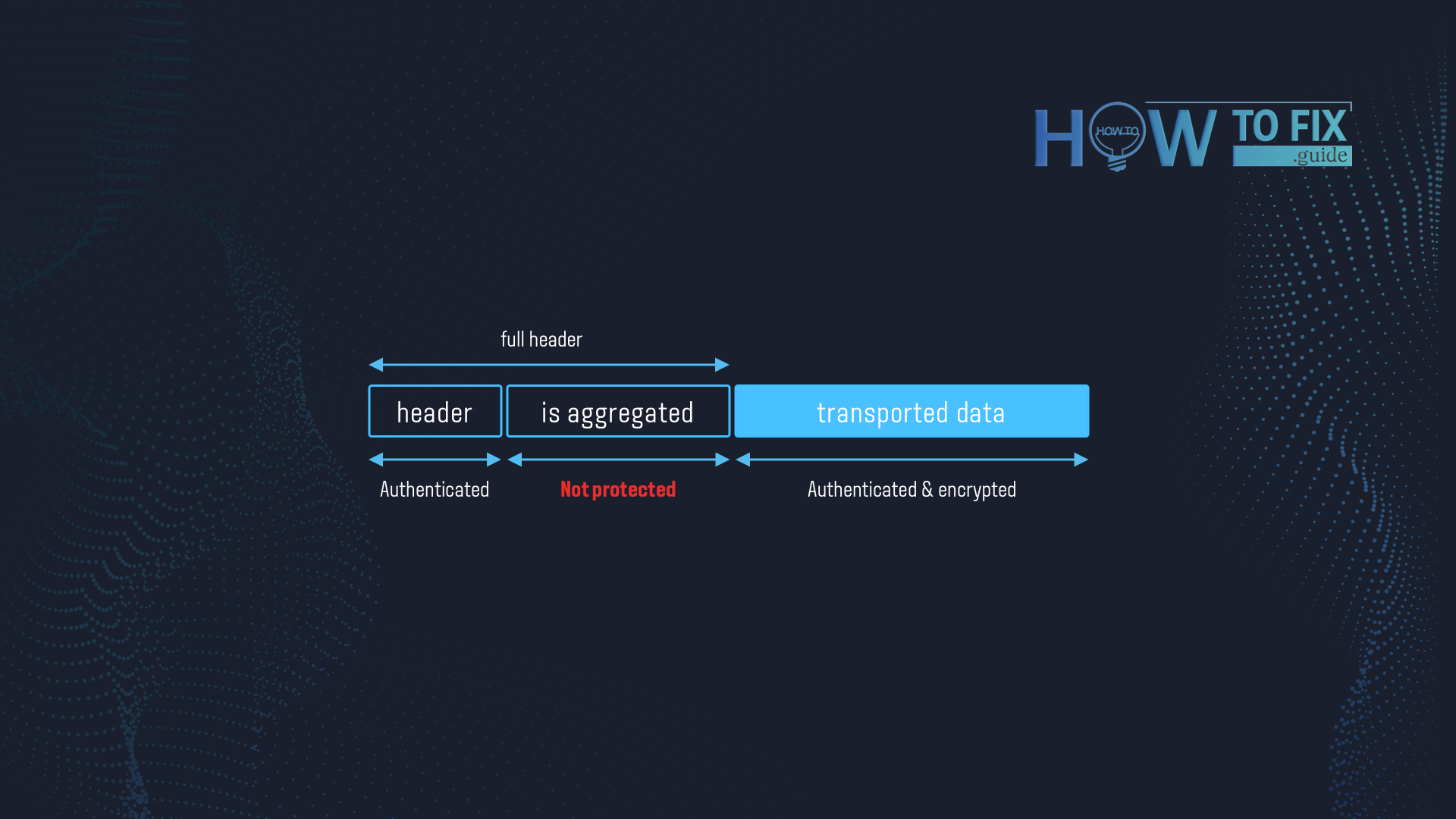
“Aggregation” flag may easily be counterfeited, and the Wi-Fi network will apply it without any problems. Why so easy? According to the original idea, the network must authenticate each flag it receives, using the so-called SPP A-MDSU frames. In fact, almost all networking devices don’t use this ability since firmware manufacturers disable it by default. And a hacker can easily drop his own frame into your network without any chances for you to protect.
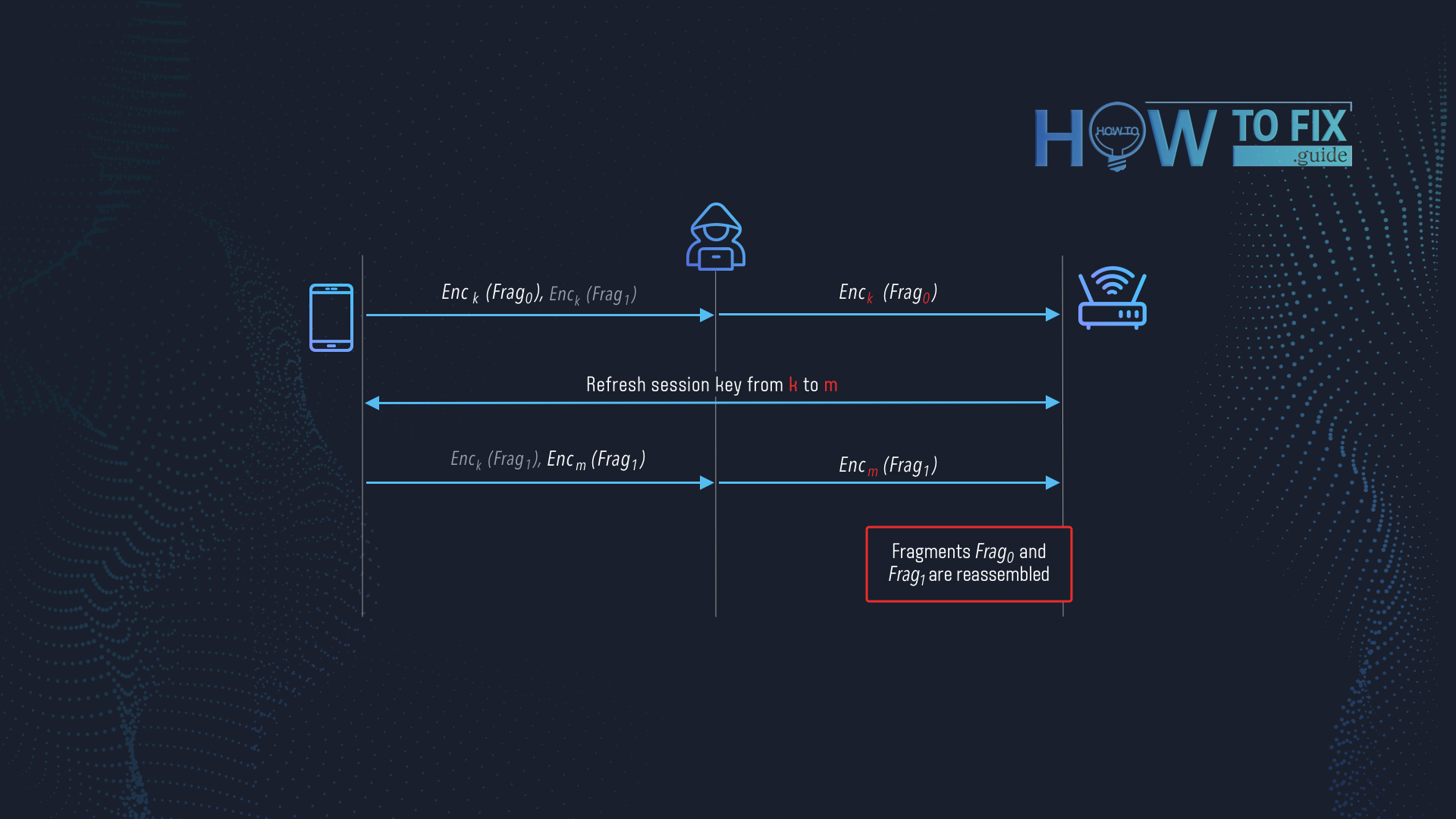
Mixed key attack
CVE-2020-24587. That security breach is related to the feature that allows you to receive every packet you must. Large frames are divided into smaller ones and then encrypted with the same key. Thus, the receiver device understands that these fragments belong to the same large frame and make corresponding actions (decryption and consolidation). However, the Wi-Fi devices are not required to check the correspondence of the encryption keys of the frame fragments. In some conditions, attackers can inject their packets among the frame elements, and they will reach your computer without any resistance.
Fragment cache attack
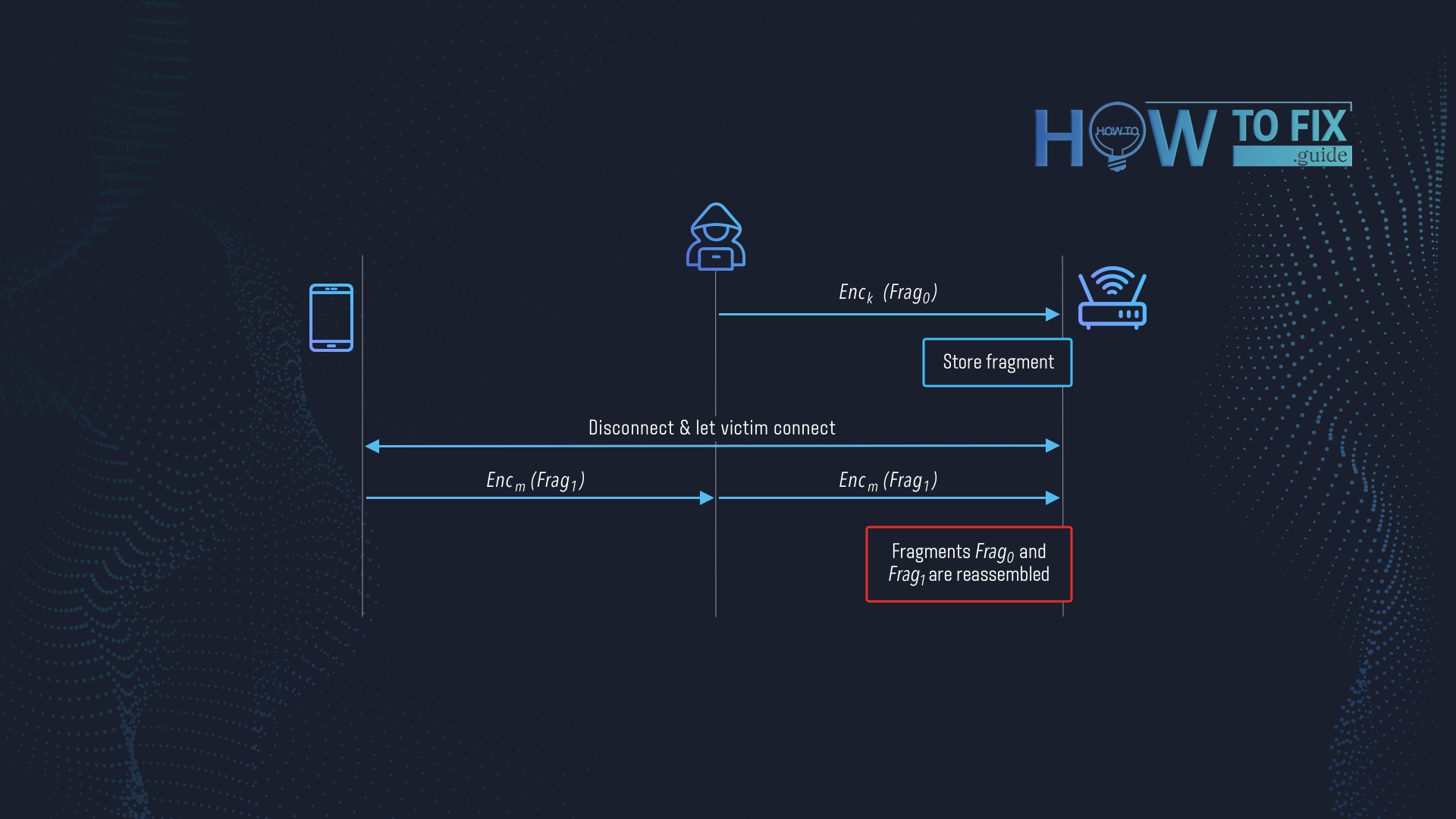
CVE-2020-24586. This vulnerability also appears because of the fragmentation of the frame. When the user disconnects from the Wi-Fi network, the network is not obliged to wipe out the rest of the non-reassembled fragments. Those vulnerabilities appear to be especially easy to exploit in such access points as Eduroam or Govroam. Adversary connects to that hotspot, leaves the malicious code inside the fragment in the memory of the router, and then disconnects. Then, when the victim connects and attempts to receive a fragmented frame, the router reassembles the frame adding one with the malicious code inside.
What is the tagret of FragAttacks?
Cybercriminals use these vulnerabilities to get access to your Wi-Fi network. If you have an IoT network at home, a hacker can easily break in and do anything he wants with your devices. There were also several cases when hackers infected the home IoT network with ransomware. Whatever it was, there is nothing pleasant when someone interrupts in such a private thing as your home network.
Meanwhile, devices inside of the home network may give the crooks less physical but much more valuable things – information. After getting access to your home network, cybercriminals can intercept the data packages you send over the Wi-Fi network. If you use WEP encryption or do not use it, hackers can easily read your conversations or check the database you have just uploaded. This information may be sold in the future on Darknet. Possibly, fraudsters can blackmail you threatening to publish some sensitive information, especially if they got access to some of your private videos.
Is it possible to avoid FragAttack?
As I described earlier, FragAttacks exist because of firmware problems. Usually, the term firmware users mean device drivers. However, if we are talking about IoT devices, we mean exactly their firmware. Luckily, manufacturers who care about the support for their products released the corresponding security patches long ago. Nonetheless, there is still a lot of people who use devices from no-name manufacturers. Thus, we can already make several conclusions.
Follow these hints:
- Update the firmware regularly. If you use the devices from well-known manufacturers, they usually offer regular updates on their products. These patches may bring not only cybersecurity features but also new functionality for your devices.
- Set up your Wi-Fi security. Wireless Encryption Protocol (WEP) is a very bad solution for network security. Cybersecurity experts recommend using at least WPA2 or WPA3. As you can see, even these encryption standards are not invulnerable, but they will stop the hackers who use commonly known tools, like aircrack-ng.
- Do not use the IoT devices from no-name manufacturers. I have no right to tell you which brands you need to buy. But cybersecurity is a thing that does not give you a choice. Wi-Fi-controlled light bulbs, RGB strings, or any other small trinket you order on AliExpress likely have no updates, and you will barely be able to get the firmware documentation on it. Hence, the chance that someone will hack your network is very high, and you will not be able to fix it.
- Upgrade your devices. Using obsolete OS, like Windows 7 or OSX 10.11, is a huge risk. Even if crooks hacked into your network, they will not be able to reach your information if you use the operating system with the most modern security features. Such an old OS version does not receive all actual updates, so the breaches used in FragAttack are free to be used.
- Prefer the websites with HTTPS. When your Wi-Fi network is not encrypted, HTTPS is your last chance to keep the privacy of your information. HTTPS means the usage of RSA-1024 encryption mechanism. It has 2^1024 possible keys variants, so it is impossible to hack it with the common hacking methods.
- Mathy Vanhoef’s Twitter account.
How can I know that I am risking?
Besides the mentioned factors, there is a single one covering exactly all mentioned breaches. If no one tries to break into your network – there is no problem. FragAttack does not appear out of the blue. When you live in a private house, and your home network range does not reach the fence – you have nothing to worry about. You will barely miss the hacker who sits in the middle of your garden. Meanwhile, living in an urban area gives you a risk that there is a man interested in your data two floors above.
Luckily, there are no cases when cybercriminals use FragAttack vulnerabilities. Of course, that does not mean that you may relax and forget about the prevention methods I described above. Fragmentation and aggregation attacks are just starting their way, and I am sure that the cybersecurity world will talk again about them in the future.
User Review
( votes)References



