FadeStealer, an information stealer with wiretapping capabilities, distributes itself via email. It incorporates a backdoor created using GoLang and exploits the Ably platform, a legitimate platform designed for instantaneous data transfer and messaging.
FadeStealer actively captures screenshots, extracts data from removable media devices and smartphones, records keystrokes, and conducts wiretapping, providing cybercriminals with various functionalities.
By exfiltrating confidential data such as personal information, financial details, login credentials, and intellectual property, FadeStealer enables cybercriminals to compromise compromised devices.
FadeStealer: An Overview
| Name | FadeStealer |
| Detection | Downloader/CHM.Generic |
| Damage | FadeStealer can cause significant damage by compromising the privacy and security of individuals and organizations. It can exfiltrate confidential data, record keystrokes, conduct wiretapping, and invade privacy by capturing screenshots. Additionally, it can enable cybercriminals to engage in fraudulent activities such as unauthorized transactions, identity theft, and phishing attacks. |
| Fix Tool | See If Your System Has Been Affected by FadeStealer Virus |
The keylogging and wiretapping capabilities of FadeStealer allow cybercriminals to monitor and intercept communications, gather intelligence, and potentially engage in targeted espionage against individuals or organizations. By capturing screenshots, FadeStealer invades privacy and compromises sensitive or personal information stored on the compromised devices.
With access to captured login credentials and financial data, cybercriminals can carry out fraudulent activities, including unauthorized transactions, identity theft, or phishing attacks. Therefore, it is crucial to remove FadeStealer from compromised devices promptly.
To conclude, FadeStealer is a highly dangerous and sophisticated tool that empowers cybercriminals to engage in various malicious activities. With capabilities such as data exfiltration, keylogging, wiretapping, and more, FadeStealer poses a significant threat to individuals, organizations, and the overall security of digital systems.
How Did FadeStealer Infiltrate My Computer?
Currently, it is believed that cybercriminals approach targets through spear phishing emails containing a regular password-protected document accompanied by a disguised CHM malware file labeled as a password file.
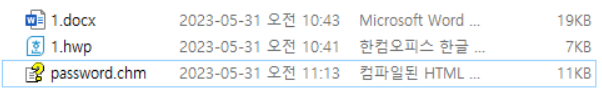
According to ASEC, the phishing emails employ tactics to entice individuals into opening the CHM file in order to obtain the document password, thereby infecting their Windows computer.
Essentially, the threat actor compresses the password-protected document along with the CHM malware, deceiving users into thinking that executing the CHM file is necessary to access the protected document.
Upon executing the CHM file, users gain access to the password information. However, the internal script code within the CHM file initiates the execution of MSHTA.exe, resulting in the execution of a malicious script from the threat actor’s command and control (C&C) server.
How to Avoid Malware Installation
To minimize vulnerabilities, it is crucial to keep your operating system and software up to date. When dealing with email attachments or encountering suspicious links, particularly from unfamiliar or untrusted sources, exercise caution and remain vigilant. Utilize trusted antivirus or anti-malware software and regularly scan your system to detect and mitigate potential threats.
Adopt safe browsing practices, which include refraining from downloading files from untrusted websites and being cautious of pop-up ads or deceptive download buttons. By implementing these measures, you can enhance your overall cybersecurity posture and protect yourself from online risks.
If you suspect that your computer is already infected, we recommend running a scan with Gridinsoft Anti-Malware for Windows to automatically eliminate infiltrated malware.
How to remove the FadeStealer from my PC?
FadeStealer malware is incredibly hard to eliminate manually. It stores its documents in numerous locations throughout the disk, and can get back itself from one of the elements. Moreover, a lot of modifications in the windows registry, networking configurations and Group Policies are pretty hard to discover and change to the original. It is much better to use a special app – exactly, an anti-malware program. GridinSoft Anti-Malware will definitely fit the best for malware removal objectives.
Why GridinSoft Anti-Malware? It is very lightweight and has its databases updated just about every hour. Furthermore, it does not have such problems and exposures as Microsoft Defender does. The combination of these facts makes GridinSoft Anti-Malware ideal for taking out malware of any form.
Remove the FadeStealer with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of FadeStealer the default option is “Delete”. Press “Apply” to finish the malware removal.



Frequently Asked Questions (FAQ)
FadeStealer is primarily distributed via email. Cybercriminals send spear phishing emails containing a password-protected document along with a disguised CHM malware file, tricking users into executing the file and compromising their devices.
FadeStealer offers a range of functionalities, including capturing screenshots, extracting data from removable media devices and smartphones, recording keystrokes, and conducting wiretapping..
FadeStealer can exfiltrate various types of confidential data, including personal information, financial details, login credentials, and intellectual property.
FadeStealer poses significant risks by compromising privacy, enabling unauthorized access to sensitive data, facilitating fraudulent activities, and potentially engaging in targeted espionage against individuals and organizations.
Cybercriminals distribute FadeStealer through spear phishing emails containing a password-protected document and a disguised CHM malware file. Users are tricked into executing the CHM file, which initiates the execution of a malicious script.
To protect yourself from FadeStealer and similar threats, it is important to keep your operating system and software up to date. Be cautious when dealing with email attachments and suspicious links, use trusted antivirus or anti-malware software, and practice safe browsing habits.
If you suspect that your computer is infected with FadeStealer, it is recommended to run a scan with reliable anti-malware software, such as Gridinsoft Anti-Malware for Windows, to detect and remove the infiltrated malware.
Yes, FadeStealer can be removed from compromised devices. It is important to promptly detect and eliminate the malware using appropriate security tools to ensure the device’s security and prevent further damage.
Information regarding legal action against FadeStealer developers is not available at the moment. However, law enforcement agencies and cybersecurity organizations actively work to identify and apprehend cybercriminals involved in such activities.
How to Remove FadeStealer Malware
Name: FadeStealer
Description: FadeStealer can cause significant damage by compromising the privacy and security of individuals and organizations. It can exfiltrate confidential data, record keystrokes, conduct wiretapping, and invade privacy by capturing screenshots. Additionally, it can enable cybercriminals to engage in fraudulent activities such as unauthorized transactions, identity theft, and phishing attacks.
Operating System: Windows
Application Category: Malware


