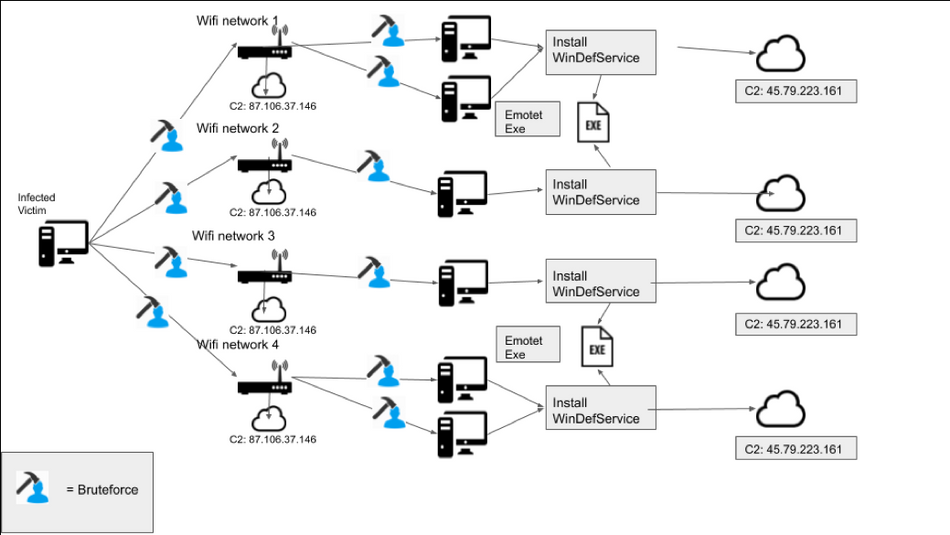
At the edge of August 2021, the users of Confluence (a program for collaboration between employees) suffered a massive attack on their companies. Regardless of the fact that this attack was performed through the exact Confluence app, the whole corporate networks fell like a clay-made Colossus. But the exact reason and endpoints of these attacks were published only 20 days later – together with another loud attack on MidnightBSD developers group.
What happened?
The majority of victims among ones who reported the incident used an outdated Confluence version. No one can surely say why they didn’t update their version – even though a lot of those users were using a free version which was offered by Atlassian for open-source and non-commercial projects. However, history doesn’t tolerate the subjunctive moods. Even if they would be using an updated version, their networks would not be safe.
The interface of Confluence app
The reason for such a paradox is called “CVE-2021-26084” – an exploit that allows the hackers to execute the arbitrary code on the server, even being unauthorized. Another uncertain detail of those attacks is that hackers were not trying to download the data from compromised servers, or deal damage in some other way. Their actions after breaking into the network were aimed at the installation of cryptocurrency mining software. So greedy and so fresh!
MidnightBSD is one of the last victims, who have reported the incident on the day when this article was written, 09/14. Once again, crooks did not take even a thing of all files that were stored on their servers. Currently, the attack is reflected, and all server elements that were disabled after the attack were reinstalled. The behavior of those crooks is pretty strange, but it is obvious that those attacks are not over.
Is there some response from Atlassian?
The company who develops the Confluence, Australia-based IT corporation Atlassian, issued the official note – Confluence Security Advisory – on August 25. In that note they have presented a list of versions that are vulnerable to CVE-2021-26084, and it takes almost all versions of this program, starting from 4.x.x:
All 5.x.x versions
All 6.0.x versions
All 6.1.x versions
All 6.2.x versions
All 6.3.x versions
All 6.4.x versions
All 6.5.x versions
All 6.6.x versions
All 6.7.x versions
All 6.8.x versions
All 6.9.x versions
All 6.10.x versions
All 6.11.x versions
All 6.12.x versions
All 6.14.x versions
All 6.15.x versions
All 7.0.x versions
All 7.1.x versions
All 7.2.x versions
All 7.3.x versions
All 7.4.x versions before 7.4.11
All 7.5.x versions
All 7.6.x versions
All 7.7.x versions
All 7.8.x versions
All 7.9.x versions
All 7.10.x versions
All 7.11.x versions before 7.11.6
All 7.12.x versions before 7.12.5
The versions that have this security breach fixed are 6.13.23, 7.4.11, 7.11.6, 7.12.5 and 7.13.0. As you can already guess, the majority of companies still use the vulnerable versions of the Confluence app. And as the other side of this situation says (exactly, ransomware developer which does not have any direct relation to this article), companies are prone to ignore the security breaches until the attack is committed.
Fortunately, the attackers that use the aforementioned vulnerability deal pretty low damage to the server and network. However, solving the incident can take a few days, which is not OK for small companies that try to hold on in the tight market. However, the threat is always a threat – even after being forgotten for years. In contrast to the nature, where the 500-years-old virus cannot bring a lot of damage, in the computer world ransomware, coin miners, spyware, as well as the security breaches that are used to inject them, keep being dangerous even after 10 years of inactivity.
Only serious technological changes, like swapping the x86 architecture to ARM, can stop the malware from spreading and beat the obsolete viruses – but only for a while. We live in a rock-crushing time – don’t miss the best moments!
User Review
( votes)