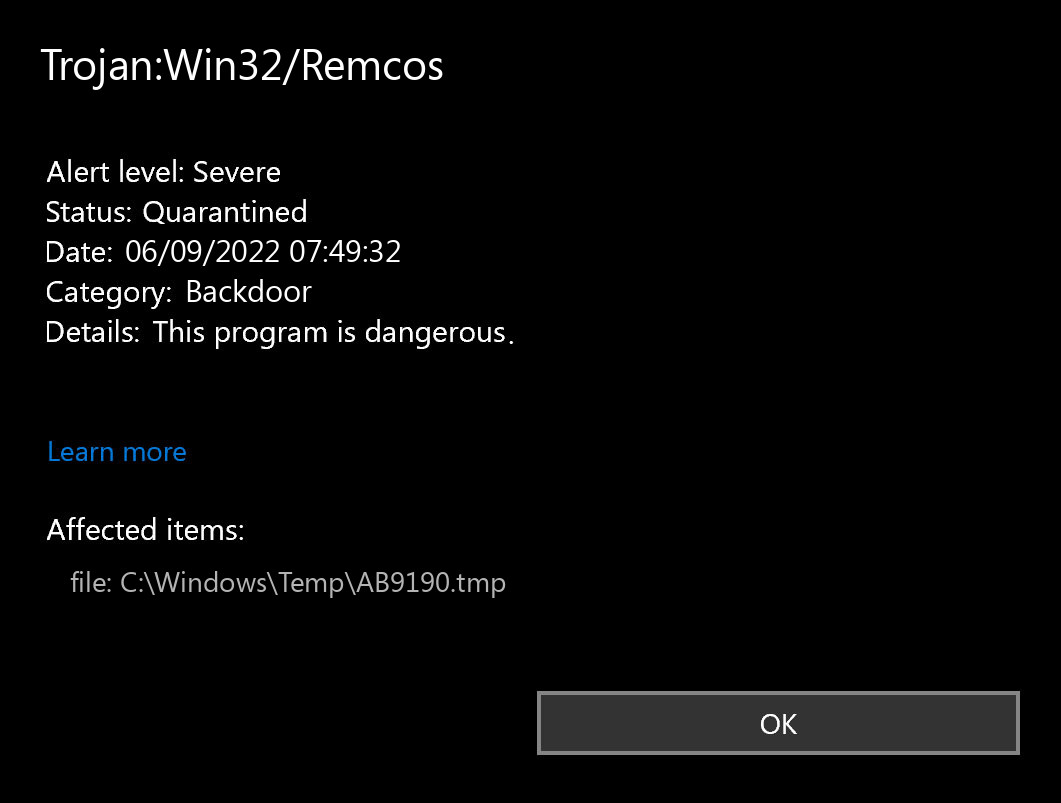
If you spectate the notification of Backdoor.Win32.Remcos detection, it seems that your system has a problem. All viruses are dangerous, without any deviations. Remcos grants the cybercriminals access to your system, or perhaps adds it to the botnet.
Any kind of malware exists with the only target – gain money on you1. And the programmers of these things are not thinking of morality – they utilize all available methods. Taking your private data, getting the payments for the banners you watch for them, exploiting your CPU and GPU to mine cryptocurrencies – that is not the complete list of what they do. Do you like to be a riding horse? That is a rhetorical question.
What does the notification with Backdoor.Win32.Remcos detection mean?
The Trojan:Win32/Remcos detection you can see in the lower right side is demonstrated to you by Microsoft Defender. That anti-malware software is quite OK at scanning, however, prone to be generally unreliable. It is prone to malware invasions, it has a glitchy interface and problematic malware clearing capabilities. Therefore, the pop-up which says about the Remcos is simply a notification that Defender has found it. To remove it, you will likely need to use a separate anti-malware program.
The exact Backdoor.Win32.Remcos virus is a very nasty thing. This malware is designed to be a sneaky burglar, which functions as a remote-access tool. When you grant somebody remote access willingly, it is OK, but Remcos will not ask you if you would like to give it. After connecting to your system, crooks are able to do whatever they want – snatching your files, browsing your messages, gathering personal data, and so on. Backdoors often bring a supplementary stealer – the virus that is developed to gather all available data about you. Nonetheless, far more widespread use of the backdoors is creating the botnet. After that, the network of infected PCs may be used to conduct DDoS attacks or to inflate the vote results on various web pages.
Backdoor Summary:
| Name | Remcos Backdoor |
| Detection | Trojan:Win32/Remcos |
| Damage | Gain access to the operating system to perform various malicious actions. |
| Similar | Coroxy, Bladabindi, Tukrina, Redcap, Msil Remcos, Bladabindi, Mydoom, Blackmoon |
| Fix Tool | See If Your System Has Been Affected by Remcos backdoor |
File Info:
crc32: F1CCBF60md5: 5d551a59c6d6a87341dd453f4ce6c2e9name: 5D551A59C6D6A87341DD453F4CE6C2E9.mlwsha1: 3e60589d80fb951d1b41fc23eeca142706f494d2sha256: 6da5a41c6dd6f0ddc638a3bccceeae8132814f605971a2f9eb1af58040f60eb8sha512: 8788b1d4a7c86198712d8cb5c79cd66ef2d31d078d26d86c815c1e267d6ee63be66f756a017cbd5b56bb856a0ff54b1d4a2d5ab186ce6270ebf56f93fbedfc9cssdeep: 6144:7z42yjsqWRwT+qp1LJFZa90JsjCWAQQqdg3b5PloRxQwh2SEgy82SiyLF91Z5:7GnFF1pWHQ53t9o3Q/SrNtLrZtype: PE32 executable (console) Intel 80386, for MS WindowsVersion Info:
0: [No Data]
Backdoor.Win32.Remcos also known as:
| GridinSoft | Trojan.Win32.Kryptik.oa!s1 |
| Elastic | malicious (high confidence) |
| MicroWorld-eScan | Trojan.GenericKD.35909012 |
| ALYac | Backdoor.Remcos.A |
| Cylance | Unsafe |
| AegisLab | Trojan.Multi.Generic.4!c |
| Sangfor | Malware |
| BitDefender | Trojan.GenericKD.35909012 |
| K7GW | Riskware ( 0040eff71 ) |
| K7AntiVirus | Riskware ( 0040eff71 ) |
| Arcabit | Trojan.Generic.D223ED94 |
| Symantec | ML.Attribute.HighConfidence |
| APEX | Malicious |
| Paloalto | generic.ml |
| Kaspersky | HEUR:Backdoor.Win32.Remcos.gen |
| Alibaba | Trojan:Win32/Kryptik.0e73cd34 |
| NANO-Antivirus | Virus.Win32.Gen.ccmw |
| ViRobot | Trojan.Win32.Z.Wacatac.401408.E |
| Ad-Aware | Trojan.GenericKD.35909012 |
| Emsisoft | Trojan.GenericKD.35909012 (B) |
| F-Secure | Heuristic.HEUR/AGEN.1123409 |
| DrWeb | Trojan.DownLoader36.31534 |
| VIPRE | VirTool.Win32.Obfuscator.da!k (v) |
| McAfee-GW-Edition | BehavesLike.Win32.VirRansom.fc |
| FireEye | Generic.mg.5d551a59c6d6a873 |
| Sophos | Mal/Generic-S |
| Ikarus | Win32.Outbreak |
| Avira | HEUR/AGEN.1123409 |
| MAX | malware (ai score=89) |
| Kingsoft | Win32.Hack.Undef.(kcloud) |
| Microsoft | Trojan:Win32/Caynamer.A!ml |
| ZoneAlarm | HEUR:Backdoor.Win32.Remcos.gen |
| GData | Win32.Backdoor.Remcos.32ETFE |
| Cynet | Malicious (score: 100) |
| AhnLab-V3 | Trojan/Win32.Agent.C4282552 |
| McAfee | Artemis!5D551A59C6D6 |
| Malwarebytes | Spyware.TelegramBot.TOR.Generic |
| ESET-NOD32 | a variant of Win32/Kryptik.HILO |
| Rising | [email protected] (RDML:4trhuSSJ74xIcmRfN+orwA) |
| SentinelOne | Static AI – Suspicious PE |
| Fortinet | W32/Kryptik.HILO!tr |
| BitDefenderTheta | Gen:NN.ZexaF.34700.yuZ@aiQUN5ei |
| AVG | Win32:Malware-gen |
| Avast | Win32:Malware-gen |
Shortly about backdoors
Backdoors are viruses that can obtain both separated and incorporated shapes. Once you may find that an official program from a well-known company has a functionality that makes it possible for somebody to connect to your system. Will it be somebody from the creators or a 3rd party – no one knows. But the scandal when this thing is identified in an official program is nearly impossible to miss. There is additionally chatter that there is a hardware-based backdoor in Intel CPUs2.
Is Backdoor.Win32.Remcos dangerous?
As I have mentioned previously, non-harmful malware does not exist. And Backdoor.Win32.Remcos is not an exclusion. This backdoor does not deal a many harm just after it releases. Nevertheless, it will likely be a really bad surprise when an occasional forum or website in the Web will not let you in, due to the fact that your IP-address is disallowed after the DDoS attack. But even if it is not critical for you – is it pleasant in any way to know that someone can easily access your PC, read your discussions, open your documents, as well as spectate what you do?
The spyware that is often present as a supplement to the Backdoor.Win32.Remcos virus will be just an additional argument to remove it as fast as you can. Nowadays, when users’ data is priced very high, it is too goofy to provide the criminals such an opportunity. Even worse if the spyware will somehow manage to steal your banking information. Seeing zeros on your savings account is the worst headache, in my opinion.
How did I get this virus?
It is difficult to trace the origins of malware on your PC. Nowadays, things are mixed, and distribution ways utilized by adware 5 years ago can be used by spyware nowadays. But if we abstract from the exact spreading tactic and will think of why it works, the answer will be quite basic – low level of cybersecurity knowledge. People press on promotions on strange websites, click the pop-ups they receive in their web browsers, call the “Microsoft tech support” believing that the odd banner that says about malware is true. It is very important to know what is legitimate – to stay away from misconceptions when attempting to determine a virus.
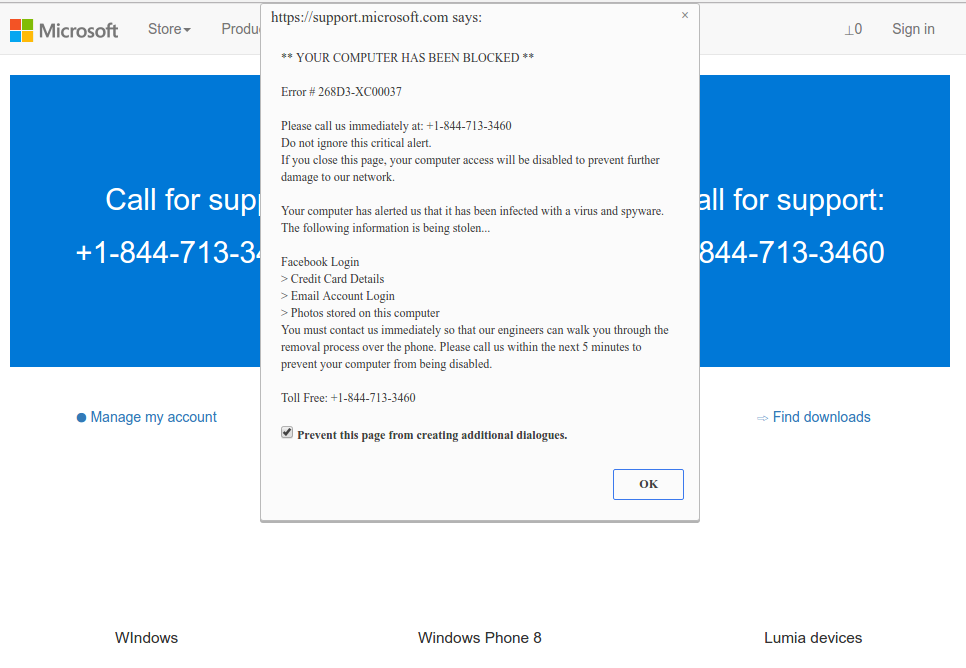
Microsoft Tech Support Scam
Nowadays, there are two of the most widespread tactics of malware distribution – lure e-mails and also injection into a hacked program. While the first one is not so easy to stay away from – you should know a lot to recognize a counterfeit – the second one is easy to solve: just don’t use hacked programs. Torrent-trackers and various other sources of “free” applications (which are, exactly, paid, but with a disabled license checking) are just a giveaway place of malware. And Trojan:Win32/Remcos is just within them.
How to remove the Trojan:Win32/Remcos from my PC?
Backdoor.Win32.Remcos malware is very difficult to delete by hand. It stores its documents in multiple places throughout the disk, and can recover itself from one of the elements. Furthermore, a number of alterations in the registry, networking configurations and also Group Policies are quite hard to discover and return to the initial. It is far better to use a special app – exactly, an anti-malware program. GridinSoft Anti-Malware will fit the most ideal for malware removal purposes.Why GridinSoft Anti-Malware? It is pretty light-weight and has its detection databases updated almost every hour. Additionally, it does not have such problems and exploits as Microsoft Defender does. The combination of these details makes GridinSoft Anti-Malware perfect for removing malware of any type.
Remove the viruses with GridinSoft Anti-Malware
- Download and install GridinSoft Anti-Malware. After the installation, you will be offered to perform the Standard Scan. Approve this action.
- Standard scan checks the logical disk where the system files are stored, together with the files of programs you have already installed. The scan lasts up to 6 minutes.
- When the scan is over, you may choose the action for each detected virus. For all files of Remcos the default option is “Delete”. Press “Apply” to finish the malware removal.



User Review
( votes)References
- Read about malware types on GridinSoft Threat encyclopedia.
- Gossip about the backdoor in Intel processors on Reddit.