According to Palo Alto Networks’ annual report, the average ransomware ransom demand for the first half of 2022 was $30 million, with a maximum payout of about 25% of that amount, indicating that hackers are willing to...
Author - Emma Davis
Hackers Use WebAssembly Miner to Avoid Detection
Sucuri experts recently discovered 207 sites infected with a malicious cryptocurrency miner, whose work is based on the use of WebAssembly (Wasm) in the browser. me remind you that we talked about the fact that Mining botnet...
Sources of Rust-Written Luca Stealer Malware Published on Hacker Forums
On the hack forums, the sources of the Luca Stealer malware, designed to steal information and written in Rust, are published for free. Information security researchers report that this infostealer is already actively used in...
Microsoft Updates May Break Printing in Windows Server
Microsoft has warned that starting with optional preview updates last week, a year-old workaround that fixed Windows Server printing issues on non-compatible devices will no longer work. Therefore, there may be problems with...
Cloud Botnet of 8220 Group Infected 30,000 Hosts for Cryptocurrency Mining
SentinelOne specialists have discovered the 8220 group mining botnet, which has about 30,000 infected hosts worldwide. experts write that the 8220 group has been active since 2017 and that it is “one of many low-skilled criminal...
Vulnerabilities in MiCODUS GPS Trackers Allow Remote Car Hacking
Information security specialists have discovered serious vulnerabilities in GPS trackers, which are used in about 1.5 million cars in 169 countries around the world. We are talking about the device MiCODUS MV720, which contains...
Gas Station Hacks on the Rise Due to Rising Gas Prices
In recent months, US gas prices have hit record highs, leading some people to believe that gas station hacks are a good idea. me remind you that we also reported that Cyberattack disrupted operation of gas stations across Iran...
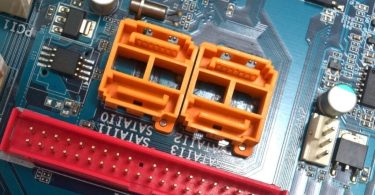
Data from Isolated Computers Can Be Stolen Using SATA Cables
Specialists from the Israeli Ben-Gurion University have developed a new method for extracting data from computers that are physically isolated from any networks and potentially dangerous peripherals. This time, the experts...
Hackers Scanned 1.6 Million WordPress Sites Looking for a Vulnerable Plugin
Wordfence researchers discovered a massive campaign in which hackers scanned about 1.6 million WordPress sites. hackers were looking for a vulnerable Kaswara Modern WPBakery Page Builder plugin that allows to upload files without...
Bugs in UEFI Affect about 70 Models of Lenovo Laptops
ESET experts reported that UEFI in many Lenovo laptops is vulnerable to three buffer overflow bugs, which can allow attackers to interfere with the OS startup process and disable security mechanisms. me remind you that in April...